Why a random string-like password 'ji32k7au4a83' was used by a large number of users?

by
It is recommended that passwords used for user authentication etc. are hard to guess from the outside, and combinations of alphabetic letters and numbers that do not pass meaning tend to have high security, as it is difficult for other people and passwords to be worn. However, engineer Robert Ou discovered that a seemingly irrelevant password ' ji32k7au4a83 ' is used by many people, 'Why such random-looking strings are used by many people About the mystery of 'is there?'
But if you check eg HIBP, it's been seen over a hundred times. Challenge: explain why and how about Happiness I remembered today concerning secure passwords: the password 'ji32k7au4a83' looks like it'd be decently secure, right? this password might be guessed
— Robert Ou @ BSidesSF (@rqou_) March 1, 2019
Why 'ji32k7au4a83' Is a Remarkably Common Password
https://gizmodo.com/why-ji32k7au4a83-is-a-remarkably-common-password-1833045282
Mr. Ou has checked the number of leaks at the site ' Have I Been Pwned: Pwned Passwords (HIBP) ' for checking password leakage for the string 'ji32k7au4a83'. HIBP is a service created by Troy Hunt , a Microsoft Regional Director , and is a service that allows anyone to check for free whether their passwords have been leaked in the past personal information leak incident. You are
'Pwned Passwords', a service that allows you to check for free whether your password appears in the past leaked data or not-GIGAZINE
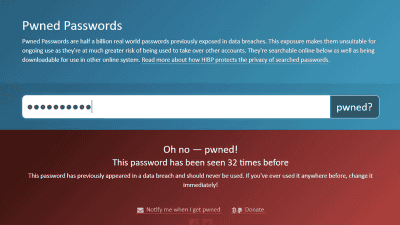
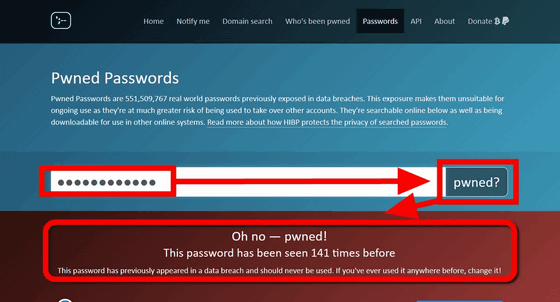
Actually, when I checked the number of leaks of 'ji32k7au4a83' in HIBP, it was surprising that at the time of writing the article, there were 141 leak histories hit. Considering this number of times, there are several people who used at least the same password 'ji32k7au4a83' for various services, and it is considered that the password was leaked in any incident. In addition, it can be inferred that many users use the password 'ji32k7au4a83', considering that many people are not involved in password leakage.
The question of why a random alphanumeric string 'ji32k7au4a83' is used frequently, Mr. Ou was listed as a problem on Twitter. As a result, it seems that Twitter followers received an extremely accurate answer.
In fact, the character string 'ji32k7au4a83' is one of the Chinese phonetic symbols of '
In Taiwan, the importation law using the importation code is used also for the input to PC etc. In the keyboard for importation law, the injection symbol is stamped on the keyboard. According to a survey conducted in Taiwan in 2011, 71.3% of people are doing Chinese input according to the importation law, which is the mainstream input method in Taiwan.
The keyboard layout corresponding to the importation import law looks like this. The voiced sign shown in red can be used to input Chinese sounds using this combination and convert them into kanji in the same way as Japanese. In recent years, the batch conversion accuracy of multiple characters by context judgment has also been improved, and the conversion efficiency of the import sound import method seems to show remarkable progress.

Therefore, if the character string 'ji32k7au4a83' is disassembled according to the importation law, it can be divided into four groups 'ji3' '2k7' 'au4' 'a83'. Each group represents one syllable including tone, 'ji3' → 'ㄨ ㄛ ˇ', '2k7' → 'ㄉ ㄜ ̇', 'au 4' → 'ㄇ 一 ˋ', 'a 83' → ' In the case of “ㄇ ㄚ ˇ”, the first two notes of the consonant and vowel in the first note and the last note indicate the note of the note.
It will be like this if we convert each punctuation mark notation 'ㄨ ㄛ ˇ' 'ㄉ ㄜ ̇' 'ㄇ ˋ ㄇ' 'に' into romaji + tone and further convert it into kanji.
'ㄨ ㄛ ˇ' → 'u + o + third voice' → ' I '
'ㄉ ㄜ →' → 'd + e + light voice' → ' like '
'ㄇ 一 ˋ' → 'm + i + fourth voice' → ' dense '
'ㄇ ㄚ ˇ' → 'm + a + third voice' → ' 碼 '
The four letters ' My Secret ' mean ' My Password '. In other words, many Taiwan users use the password 'ji32k7au4a83' for the same reason that English speakers set 'mypassword' as their password. Some users might have thought that 'it is not easy to understand because this is a syllabary sign notation', but as far as HIBP's outflow results are concerned, it seems that not many users had the same idea is.

by JeongGuHyeok
Related Posts:
in Note, Web Service, Security, Posted by log1h_ik