A vulnerability that makes it easy to decrypt ciphers with well-known manufacturer's hardware encryption SSD turned out

By Hong Chang Bum
A vulnerability has been revealed in Samsung and Crucial's SSD (Solid State Drive), in which encrypted and stored data is decrypted by a third party. This problem is based on the debugging function of SSD, and once cracking is done, it will be possible to open the contents data without the password set by the user.
Solid state of fear: Euro boffins bust open SSD, Bitlocker encryption (it's really, really dumb) • The Register
https://www.theregister.co.uk/2018/11/05/busted_ssd_encryption/
Two subjects who announced this problem were Carlo Meijer and Bernard van Gastel, researchers at Rudboud University in the Netherlands. Using the hardware encryption function implemented in the SSD, even if you set the password to protect the data, we clearly see that you can bypass this password and see the data in its complete state .
Basically, the encryption key used for SSD data encryption and decryption is not derived from the user's password. This means that third parties can reprogram themselves to get the SSD body and accept any passwords via "Debug Port".
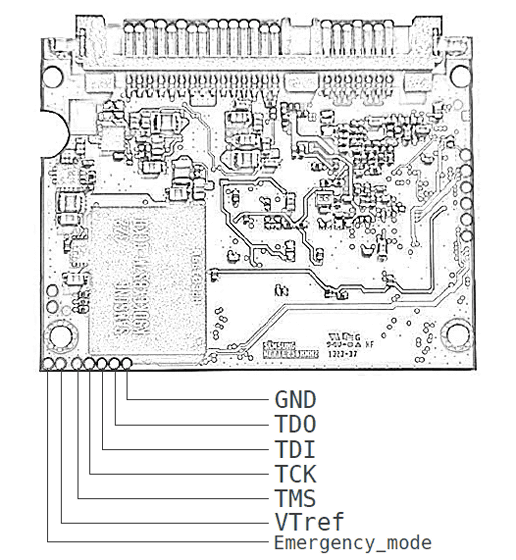
Two researchers have tested this problem with Samsung's SSD 4 model and Crucial's SSD 3 model and found that it was possible to decrypt all models. The important point here is that decryption was possible with models from multiple manufacturers. Researchers point out that there is a problem in the flow itself of SSD's hardware encryption function rather than due to firmware etc. of a specific manufacturer.
Specifically, there is a problem that the problem SSD fails to link the owner's password stored in the chip and the actual data encryption key (DEK). You can use the DEK at any time when you need the SSD built-in processor and firmware, but only when the correct password is entered. However, when a third party physically accessing the debug port of the SSD reprograms or manipulates the firmware, it is revealed that it is possible to skip authentication of the password and use the DEK It is.
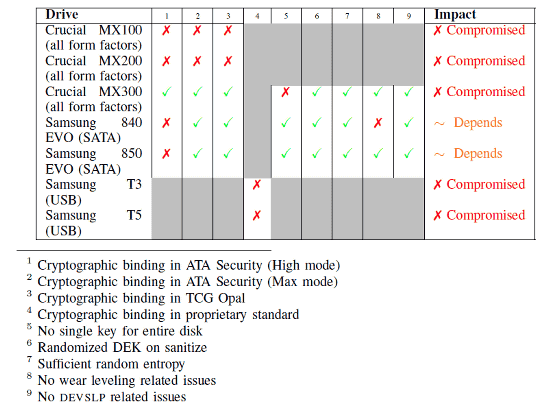
Originally, DEK is of a nature that should somehow be obtained from the owner passphrase. However, in actual SSD, it seems that there are cases where the principle is not applied. Furthermore, many SSDs says "It is possible to set different passwords for each section", but in fact it is confirmed that a single DEK is used in the device.
As a method to avoid this problem, two researchers recommend "encrypt the entire drive with the host computer without using SSD's hardware encryption function".
Related Posts: