It turns out that the backup function of Google Authenticator is not E2E encrypted and is likely to be exposed to serious security risks

A security researcher's investigation revealed that end-to-end (E2E) encryption was not performed in the cloud backup of 'Google Authenticator'
Google has just updated its 2FA Authenticator app and added a much-needed feature: the ability to sync secrets across devices.
— Mysk ???????????????? (@mysk_co) April 26, 2023
TL;DR: Don't turn it on.
The new update allows users to sign in with their Google Account and sync 2FA secrets across their iOS and Android devices.… pic.twitter.com/a8hhelupZR
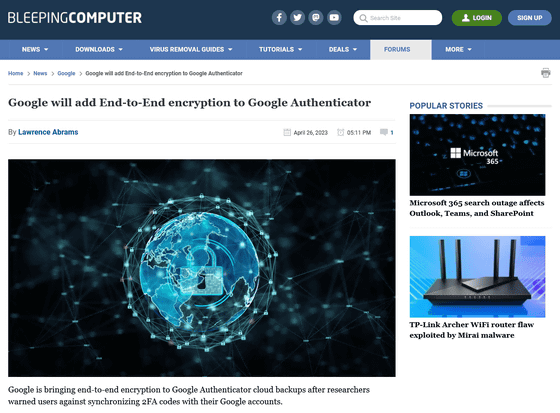
Google will add End-to-End encryption to Google Authenticator
https://www.bleepingcomputer.com/news/google/google-will-add-end-to-end-encryption-to-google-authenticator/
This service, which is provided under the name of 'Google Authenticator' on the App Store and 'Google Authenticator' on Google Play, is a one-time password issuing application that can be used for two-factor authentication. Other companies' one-time password issuing applications such as '
Experience story that the backup code of Google's two-factor authentication application could not be generated by breaking the smartphone, this is the backup method - GIGAZINE

That's where cloud synchronization via your Google account comes in. As a result, even if you lose your device, you can now check the one-time password on another device as long as you can log in with your Google account.

However, researchers at security firm Mysk discovered that Google Authenticator did not E2E encrypt the login information when it was uploaded to the cloud. The lack of E2E encryption means that unauthorized users may be able to access the data Google Authenticator sends to Google's servers.
The two-factor authentication QR code contains a key and seed for generating a one-time password, and if someone obtains this key or seed, they will generate the same one-time password to break the two-factor authentication. I can do it.
For this reason, Mysk simply called out, 'Don't use Google Authenticator's cloud sync.'
In response to this reaction, Christian Brand, a group product manager at Google, revealed plans to provide E2E encryption for Google Authenticator in the future. The timing of the offer has not been clarified.
(1/4) We're always focused on the safety and security of @Google users, and the newest updates to Google Authenticator was no exception. Our goal is to offer features that protect users, BUT are useful and convenient.
—Christiaan Brand (@christiaanbrand) April 26, 2023
Related Posts: