A case where Coinhive's URL shortening function was exploited and used for virtual currency mining via a hacker site was discovered
An administrator of the website exploits the mechanism of " Coinhive " to make visitors mining the virtual currency and receive the revenue, and the way that visitors do mining and notice the profits without noticing is investigated by security specialized companies It is clarified by.
Obfuscated Coinhive shortlink reveals larger mining operation - Malwarebytes Labs | Malwarebytes Labs
https://blog.malwarebytes.com/threat-analysis/2018/07/obfuscated-coinhive-shortlink-reveals-larger-mining-operation/
CoinHive URL Shortener Abused to Secretly Mine Cryptocurrency Using Hacked Sites
https://thehackernews.com/2018/07/coinhive-shortlink-crypto-mining.html
Coinhive is a mechanism that allows visitors to mineralize the virtual currency "Monero" by embedding dedicated JavaScript in the site. While there are people who find light in the possibility that site visitors will benefit the publisher even if they do not take special actions, there are still cases of misuse by some hackers , Security companies and antivirus related services take countermeasures and are crushing unauthorized use.
Meanwhile, an investigator of the security company "Malwarebytes Labs" said, "By exploiting the URL shortening feature of Coinhive to induce visitors to a site different from the original, you can use your own machine power We have found a new way to do mining for.
The mechanism of Coinhive's abbreviated URL generation function is to increase revenue by setting a wait time of a certain time when a page is loaded by clicking a shortened URL of a certain site and causing mining during that period. This mechanism allows publishers to use the Coinhive flow monetization method of providing site content when visitors flowing in from shortened URLs complete certain mining.
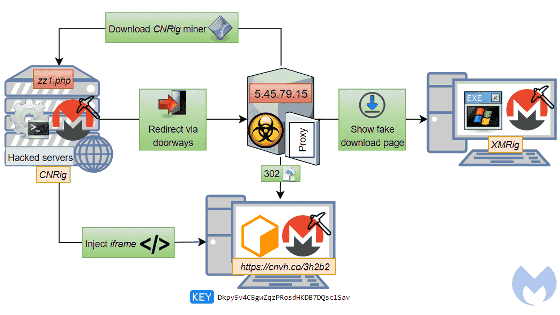
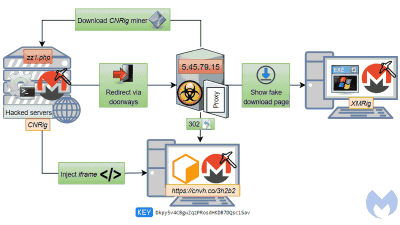
Malwarebytes Labs discovered that malicious hackers were forwarding users to their site and letting them mining by quietly sneaking in iframe tags into the HTML source of unrelated pages. The iframe tag is designed to display contents as large as 1 x 1 pixel and it is almost impossible to notice this in the usual way.
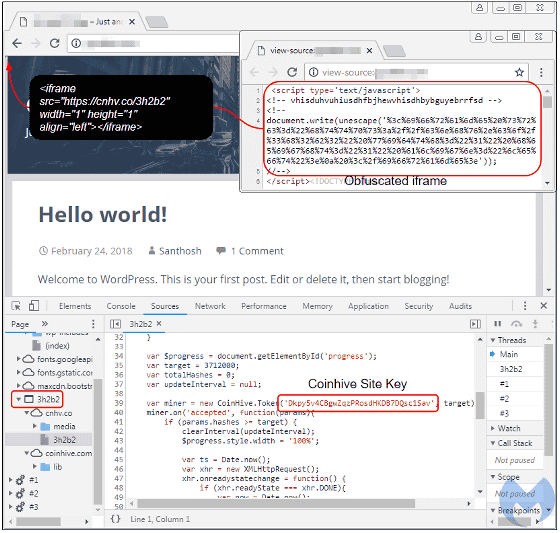
The following image shows how this mechanism is reproduced. When you open the page, you can see that the CPU power has increased to 100% during the wait time until the desired page is displayed.
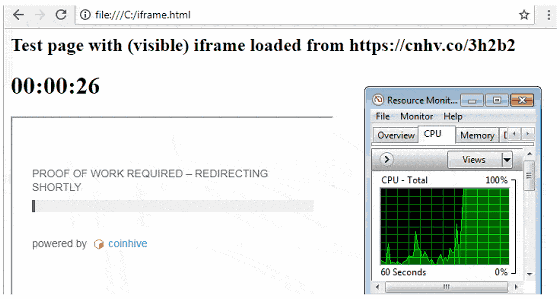
Furthermore, this "waiting time" can be changed freely by changing the hash value in Coinhive's setting. Normally it was 1024 hash, but there were also cases where 3,712,000 hashes were set.
In addition, it has also been confirmed that it is possible to minify again by having the specified hash value reached and loading the same page again when the page is loaded. At this time, the user who is not aware of this mechanism seems to think "that? The page was reloaded?", And it is the abnormal increase of the CPU power that I notice that the mining is done behind it It is about people who are aware of it.
With regard to Coinhive, both the pros and cons are arising from the viewpoint of "a new possibility of a virtual currency" to the criticism of "just malware". In Japan, it is a topic that the person who used Coinhive received investigation of the police 's house, furthermore that one case is reported in overseas media, and it is said that it is said that it attracts attention on the whole world net.
Talk about taking a house search with Virtual Currency Mining (Coinhive) - Enjoy the Web "Dokes"
https://doocts.com/3403
To avoid Coinhive's "CPU power just ride", there is also a way to introduce browser extension functions such as " MinerBlock " and " No Coin ".
Related Posts:
in Web Service, Security, Posted by darkhorse_log