There was a case of accessing a fake site even though it was the correct URL
TREZOR, an online wallet service for cryptocurrencies such as Bitcoin, reported on its blog that 'traffic may be hijacked'.
[PSA] Phishing Alert: Fake Trezor Wallet website --TREZOR Blog
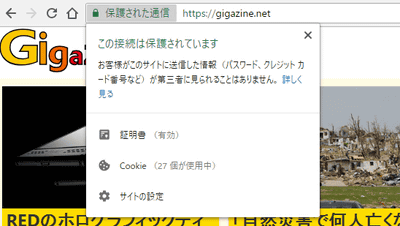
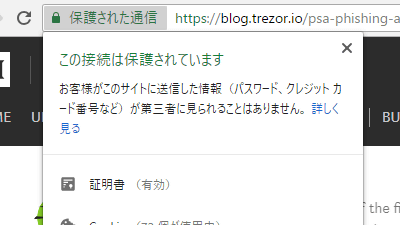
On July 2, 2018, TREZOR announced on its blog that its wallet service was being attacked. According to the blog, the TREZOR support team was discovered when a customer inquired about a fraudulent SSL certificate. The image when accessing the fake phishing site published by TREZOR is as follows, and the domain displayed in the URL is the same as the correct site 'wallet.trezor.io', but for https communication You can see that the SSL certificate you are using is incorrect and you see 'Not secure' in your browser's address bar.
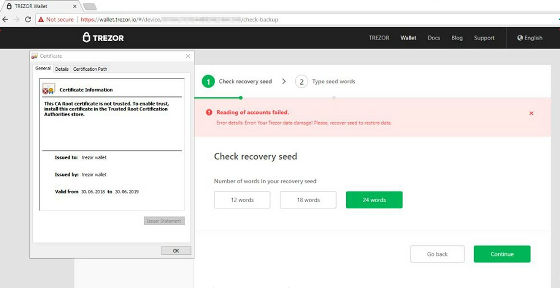
The method used for the attack is not yet known, but it is said that
Amazon's DNS service 'Route 53' is attacked and virtual currency with a market value of 16 million yen is robbed from users

Not only can you check if the URL of the website you are visiting is correct, but you can also check if the site you visited is really the site with that URL by using https (SSL) for communication. TREZOR has commented on twitter, 'Be sure to make sure that you are communicating with legitimate https.'
PSA: Phishing. We have encountered a clone of Trezor Wallet, tricking users to divulge their recovery seed. Always check for a valid https connection while using
https://t.co/rTfKn8bzIL .
Device Itself Can The Be Trusted;. Make Sure To Verify All Actions On The Trezor Screen Pic.Twitter.Com/or8Lw6M265 — TREZOR (@TREZOR) July 1, 2018
If you connect to the fake site via https, you will get a certificate error, but if you connect to http, you will not be able to notice that you have connected to the fake site. Google has announced a policy to make the Chrome browser display 'insecure' when connecting via http.
Google has a policy to clearly display sites that are not protected by HTTPS as 'insecure' in the Chrome browser --GIGAZINE

Related Posts:
in Web Service, Security, Posted by log1d_ts