51% "51 crypto" to understand vulnerable virtual currency
"Virtual currency" isBlock chain technology, And even if someone tries to conduct illegal transactions, it is a mechanism that allows multiple terminals to verify transactions all at once and thus can not fraud. However, if a terminal attached to a malicious user side occupies a majority, there is a risk that the illegal transaction is justified, and such an attack is called "51% attack" and the reliability of the virtual currency It is a cause of great loss of value and loss of value. "51Crypto"Shows 51% attack tolerance by showing how much you need to pay for a 51% attack against each virtual currency.
Cost of a 51% Attack for Different Cryptocurrencies | 51 Crypto
https://www.crypto51.app/
51% The approach to doing the attack is considered to be the virtual currencyMiningThere are two ways to prepare a large number of terminals to do and to obtain the computing capacity which accounts for a majority in the virtual currency network or to borrow a mining environment already existing. Since it is extremely difficult to construct the former physical computing environment on its own and create a computing environment that accounts for a majority in the network, 51 Crypto borrows existing mining environment and how long it takes 51% attack for 1 hour It is calculating whether it is necessary cost. The calculated amount is calculated based on the information of "Nicehash" of virtual currency mining service.
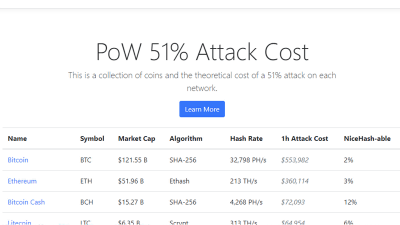
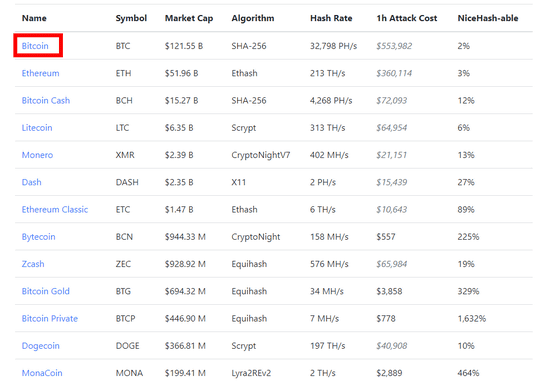
51CryptoWhen accessing, the following table is displayed. In this table, "Virtual currency name" "abbreviation" "market capitalization amount" "Hash algorithm"" Mining speed "" Cost per hour to do 51% attack "and" Percentage occupied by NiceHash service "are shown and are listed in order of market capitalization. Here, when you click "Bitcoin" at the market capitalization top at the time of article creation ... ...
Bitcoin (bit coin)The detailed info screen will be displayed. 51 Crypto displays the information when using the Nicehash service surrounded by a red frame besides the information in the table above.
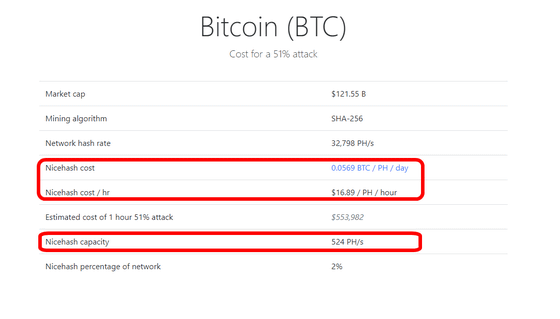
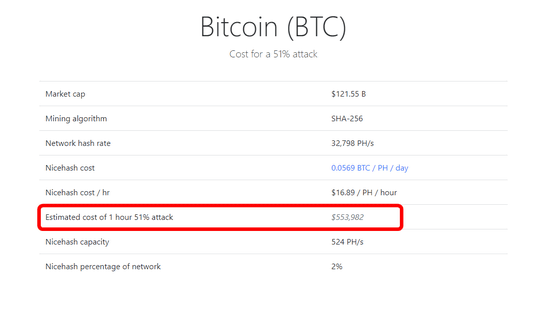
In the case of bit coin, you can see that it costs 553,982 dollars (about 60 million yen) per hour to do 51% attack.
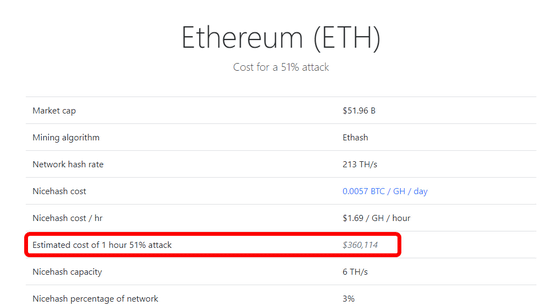
Next, with market capitalization second placeEthereumIf you look at it, you need 36,114 dollars (about 40 million yen) to attack an hour, which also seems to require a huge amount of money.
3rd placeBitcoin Cash (bit coin cache)It is $ 70,2093 (about 7.9 million yen).

4th placeLitecoin (light coin)Is about 60,4554 dollars (about 7.1 million yen), which has fallen to nearly one tenth of the price from the Ethariam.

5th placeMonero (Monero)In addition, the amount further dropped to about one third, and it was $ 21,111 (about 2.3 million yen).

After that, according to market capitalization, the amount decreases, but Bytecoin of the eighth which is declining greatly, the amount to do 51% attack for 1 hour is about 557 dollars (about 60,000 yen) And it receives a pretty cheap impression.

And in the 9th placeZcash (Gee Cash), The amount of money sharply increased to 65,584 dollars (about 7.2 million yen). Because the market capitalization is high, it seems that the 51% attack price will not rise.

The 10th place,The damage of about 2 billion yen caused 51% attackBitcoin Gold (Bitcoin Gold). The amount was 3858 dollars (about 430,000 yen).

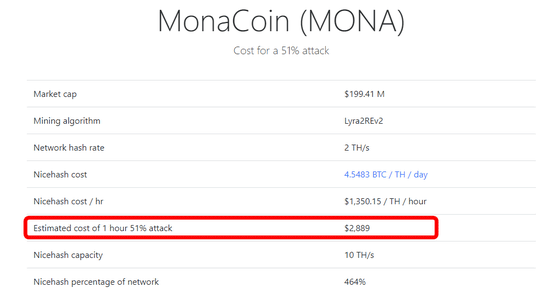
14th in 51's attack in the pastAbout 10 million yenI got hurtMonacoin (Monacoin). 51% It is said that you need 2889 dollars (about 320,000 yen) to do an attack for 1 hour.
The impression of affordable price is Mooncoin with market capitalization of 34th, and $ 51 per hour to do 51% attack (about 650 yen). Although it is thought that it is susceptible to 51% attack damage, it is doubtful whether it is possible to actually make an attack and generate profits.

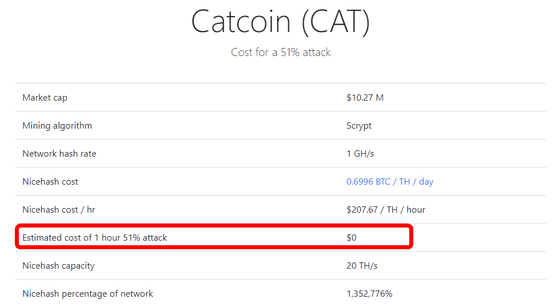
When it becomes 37th place Catcoin, it is 0 dollars (0 yen) ... ...
In the 38th Myriad, it seemed that the amount of money has changed significantly due to hash rate, etc., jumping up to about 235,061 dollars (about 26 million yen).

Related Posts:
in Software, Web Service, Security, Posted by darkhorse_log







