Summary of the big trouble by announcement of CTS Labs "AMD CPU has serious vulnerability"

Israeli security company CTS Labs announced that there are 13 vulnerabilities in AMD's CPU "Ryzen" and server CPU "EPYC". However, there are criticisms on the method of disclosing vulnerability information without giving AMD a solution to it, there are opinions as to whether there is a realistic threat in the first place or an opinion that "Is it not only if you are hoping for a decline in stock prices?" A voice is also rising.
AMDFLAWS
https://amdflaws.com/
Emerging security company CTS Labs has released information on the vulnerability inherent in AMD's CPU. According to CTS Labs, vulnerabilities are largely classified into four categories, named "RYZENFALL" "FALLOUT" "CHIMERA" "MASTERKEY" respectively.
RYZENFALL accesses the protected memory area to acquire AMD Secure Processor privileges. There is a possibility to bypass the Windows Credential Guard and steal network credentials and populate the Secure Processor with malware.

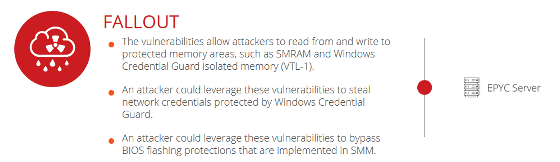
FALLOUT is a vulnerability similar to RYZENFALL and targeted for server CPU "EPYC".
CHIMERA concerns hidden backdoor inherent in chipset firmware and ASIC. I installed malware on the chipset and can attack the OS with Direct Memory Access (DMA). Specifically, ASMedia chips are listed as targets.

MASTERKEY is vulnerable to Secure Processor firmware, it can enter the Secure Processor. It can tamper with Secure Encrypted Virtualization (SEV) and Firmware Trust Platform Module (fTPM), bypassing Windows Credential Guard to make it easier to steal network credentials.

The list of target systems in the above four categories is as follows.
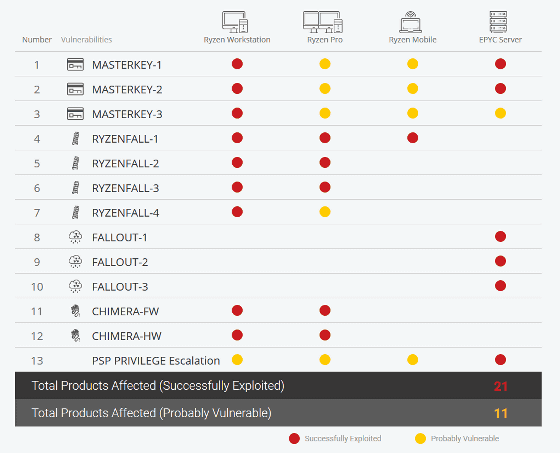
It should be noted that the prerequisite to exploit the above vulnerability is the condition "obtain manager's privileges on the local machine". However, it is pointed out that "If attacker is deprived of managerial authority in the first place, it is all you want to do and it is not necessary to investigate vulnerability?", He said, "Is not it a problem not limited to AMD processors?" There was an opinion that there is no reality in the opinion.
Linus Torvalds, the creator of Linux,Google+I criticized the announcement of CTS Labs as follows.
When was the last time you saw a security advisory that was basically 'if you replace the BIOS or the CPU microcode with an evil version, you might have a security problem?' Yeah
(CTS Labs' announcement) have you seen such as a security recommendation that "Security problems may occur if BIOS or CPU microcode is replaced with an evil version?" It is
CTS Labs released a special page "AMDFLAWS" for publicizing a total of 13 vulnerabilities based on the above four categories on March 14, 2018. In addition, white papers are attached to special page, but technical details are not written. Although disclosure of vulnerability information by CTS Labs was made within 24 hours from the provision of information to AMD, disclosure of vulnerability information that could cause major damage gives a delay to take measures such as security patches It is customary. For example, Google's Project Zero who discovered "Spectre" and "Meltdown" has set a grace of 90 days from discovery to publication. AMD, which was given almost no time delay, was at most about notifying announcing that it was conducting survey and analysis about 3 hours after the release of CTS Labs as follows.
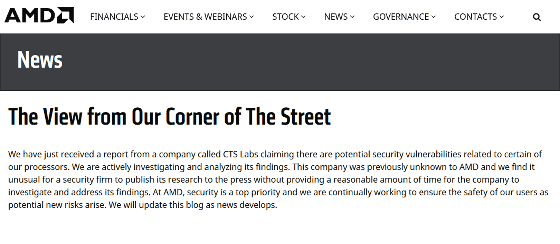
This company was previously unknown to AMD and we find it unusual for a security firm we have actively investigating and analyzing its findings. At publication. The AMD, security is a top priority and we are continually working to ensure the safety of our users as potential new risks arise. We will update this blog as news develops.
(We just received a report saying that there is a potential vulnerability to our processor from a company called CTS Labs and we are currently investigating and analyzing the discovery. I did not know that it is not a common practice to announce it without giving an appropriate time grace to investigate and analyze the problem Security is a top priority for AMD We constantly tried to ensure the safety of users every time potential hazards arise, we will update this blog as soon as new developments)
For CTS Labs, which released vulnerability information not in accordance with this general procedure, a questionable voice burst out from security experts. CTS Labs asked AnandTech why it announced in a way that could announce the vulnerability information immediately after notifying AMD, "What AMD should release patches to fix problems We can predict that it will take months and we do not have the merit of keeping 90 day rule.Rather, by disclosing vulnerability information immediately, let the customer recognize the risk of the product and judge whether to purchase it I judged that it was a responsible response "answerdoing.
Our Interesting Call with CTS-Labs
https://www.anandtech.com/show/12536/our-interesting-call-with-cts-labs
A company called CTS Labs suspects that it is suspicious that security experts have created and published a completely unnamed, suddenly elaborate dedicated website or movie, "Who is CTS Labs? "Reddit and others acted vigorously. Some people advocated conspiracy theory "There is Intel behind!", But a number of opinions have been gathered saying, "Have you aimed for a stock price fall?"
First of all, the question was cast in the following movie published by CTS Labs.
AMD Flaws Interview - YouTube
Describing the threat of AMD processor's vulnerability The above movie is a background synthesized interior photos of famous sites,RedditIt was discovered immediately by volunteers.
How "CTS Labs" created their offices out of thin air: Amd
https://www.reddit.com/r/Amd/comments/846gpm/how_cts_labs_created_their_offices_out_of_thin_air/
Why did you composite the background with movies, the reason is unknown at the time of article creation.

In addition, it was found that the domain of the CTS Labs site was registered on June 25, 2017, the registration of AMDFLAWS.com was 22 February 2018, that the YouTube channel was created only a few days ago It is.
In addition, a report titled "AMD-The Obituary (AMD, Death)" issued by a research company named Viceroy Research was discovered.
AMD-The Obituary
(PDF file)https://viceroyresearch.files.wordpress.com/2018/03/amd-the-obituary-13-mar-2018.pdf
This report inquires about AMDFLAWS.com "Although this vulnerability triggered AMD's management seems to be in a crisis situation", what is the content from PDF meta information to disclosure from AMDFLAWS.com It turns out that the report was issued only 2 hours and 50 minutes later.
33-page Viceroy research paper seems to be created (as in, metadata of the PDF creation date) 2h 50 after CTS-Labs went live.
- Ian Cutress (@ IanCutress)March 13, 2018
And we receive information that "Viceroy Research is basically a" short seller ".
Actually, I'll do it in the open. Adding@ryanshrout,@ JoshDWalrath, and@ AMDViceroy Research is basically a short - seller. They release information that's bogus, or close enough to bogus, or laced with just enough truth to alter the target stock price.
- Wesley Fick (@ cataclysmza)March 13, 2018
Viceroy Research is proud of the technique of raising profits by selling shares shortly in line with company scandals. In January 2018 I also issued a report that criticizes Capitec Bank as "Loan shark"Stock price of Capitec Bank plummeted by 20%It turns out that the event of happening was happening. In response to the disclosure of information on AMD's vulnerability, it was questioned whether it would be possible to write a 25 page report after 2 hours 50 minutes, and Viceroy Research and CTS Labs are connected There is also the voice of doubt that it is raised.
Whether the announcement by CTS Labs is aimed at the fall of AMD shares is not clear at the time of writing the article. However, even after the announcement of CTS Labs this time AMD's stock price plummeted, not the expansion, the stock market seemed calm. Rather, it may be that it is turning his eyes to a fuss about the media.
Related Posts: