The way to survive the Internet age "What can be done not to be hacked" Summary

In the information society, information itself has value, and information gathers to create new value. Of course, there is no one who is trying to steal information, and it is imperative to prepare for attacks from hackers, as long as you use the Internet, to live in an internet society. Technology siteMotherboardHowever, self defense technique in the Net age "The Motherboard Guide to Not Getting Hacked"The latest edition of 2017 is on sale. From the common sense of commonality, from the eyes to the technique of the uroko, it is presented exhaustively.
The Motherboard Guide to Not Getting Hacked - Motherboard
https://motherboard.vice.com/en_us/article/d3devm/motherboard-guide-to-not-getting-hacked-online-safety-guide
◆ Threat modeling
In order to prevent being attacked in the net world, the thing to consider first is "threat modeling". Thinking about what kind of attacks will cause bad results and who is the obstacle to prevent it? It is called the first step of countermeasures against hackers That's it.
Motherboard was created by the Electronic Frontier FoundationRisk assessmentWe are recommending 5 questions to appear in "
· What do you want to protect?
· Who do you want to protect from?
· Is there a need to protect?
· If you fail to keep it, how much bad results will you bring?
· What is the problem that prevents prevention?
By answering these five questions you will see what to do.
◆ Software update
The most fundamental and most important thing to protect yourself is to "update your software to the latest version". Maintaining the latest version of OS as well as individual applications is very important. Of course, even if it is not the latest OS, it is possible to keep the OS in a safe state as long as the security update program is available. Investigation of OS and software vulnerabilities is the hacker's top priority because it is the least resistant as a hacking method and it can attack extensively. So software updates are a top priority.
◆ Password management
If you steal your password, you not only get all the information stored in the service, it may be hijacked by the account itself. At the same time as making passwords complicated and making it difficult to crack, it is the iron rule that not to use at multiple sites. It is important to zero the risk of breaking the service to the ceremonial expression.
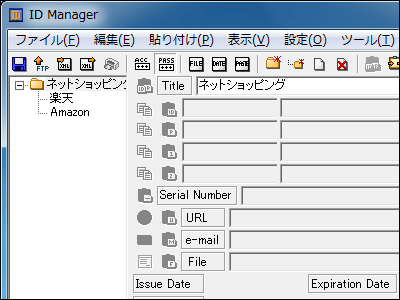
It is impossible to manage complicated passwords with "head". What I should use is password management software. If you keep even the key master password, there is no way to not use password management software that strong security promises.
"ID Manager" free software that can easily manage a bothersome ID and password bothering your head at once - GIGAZINE

There is also a service that manages the password on the cloud, but the possibility that the service provider will be attacked is not zero. However, if the type of service that encrypts and stores the password on the cloud itself, the security of the password can be maintained even if the service side is hacked. For example,LastPassI've been hacked twice before but I heard that the user's password was not stolen.
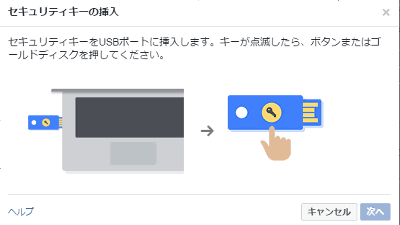
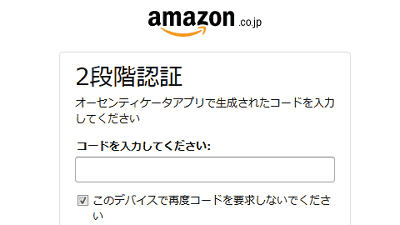
Two-step authentication
If the password is the first wall, it is "two-step verification" to act as the second wall. A service that seeks additional authentication by one-time password sent to SMS, etc. will become a breakwater in the event of a breakthrough of the password, so it will make the security striking.
There are various types of two-step verification tools such as assisting with two-step authentication with software and assisting with hardware such as USB memory, so it is recommended to utilize it when service is compatible.
"Authy" application that allows anyone to easily perform offline 2-step verification such as Gmail for free - GIGAZINE

I tried it because Facebook supported 2-step authentication with USB security key - GIGAZINE
◆ Flash prohibition
Motherboard Saying that, Adobe Flash is "one of the least secure software in computer history" "software with more holes than Swiss cheese" "hacker love software". Although it is said to be spoiled, it is certain that security is uneasy as there are browsers that have already been treated as out of support such as Google Chrome and Firefox.
Google Chrome's "Flash exclusion" moves further progress - GIGAZINE

Firefox gradually eliminates Flash, announced to disable it by default in 2017 - GIGAZINE

Microsoft also blocking Flash at Edge, blocking automatic playback - GIGAZINE

It is the end time that Adobe established for head office2020It is safe to leave Flash without waiting for it.
◆ Using antivirus software
Use of antivirus software is the basis of security measures. Antivirus software is still effective, unless it is being targeted at a national level organization or an extremely advanced hacker, even though there are frequent occurrences that can question the reliability of antivirus software.
Russian hacker knocked out NSA's confidential information using Kaspersky antivirus software - GIGAZINE

Kaspersky publishes anti-virus software source code to show its transparency - GIGAZINE

◆ Utilizing plug-ins for security
There are cases where an advertisement banner is misused to lead a fraudulent website or send malware. In order to prevent this, the ad blocking software is effective.
Usable "ad block extension" 10 selections - GIGAZINE
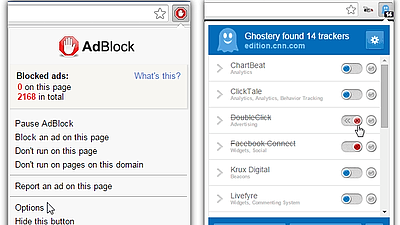
Also, a service that encrypts the connection to the service "HTTPS EverywhereI also recommend it.
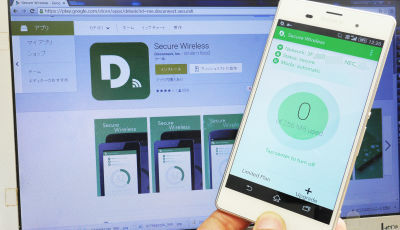
◆ Using VPN
When using a public Wi - Fi line where insecurity is unavoidable in terms of security,Virtual Private Network (VPN)It is effective to utilize.
Application for making Android Wi-Fi VPN connection for free "Secure Wireless" - GIGAZINE

However, since VPN service is cobblestone, it is recommended to check in advance which one is excellent VPN service. Motherboard is "Freedome"Private Internet Access"To the technician"Algo"Is recommended.
◆ Disable Macro
"Distributing malware using macros in Microsoft Office documents" is a classic hacking method that Microsoft has also taken measures, recently as new macro exploit hacks are discovered It is getting. If you respect security aspects, you should stop using macros.
Please be aware that hacking techniques that function without macro execution "PowerPoint Attachment Attack" are also shown as follows.
New PowerPoint Attachment Attack to Infect Malware "Tinba" Stealing Bank Account Information without Macro Execution Discovered - GIGAZINE
◆ File backup
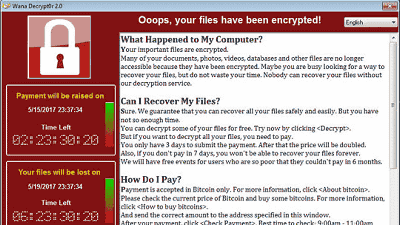
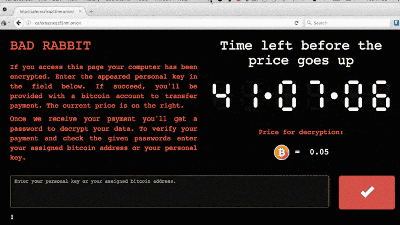
The importance of backing up important files is the same in any era. Even today in the cloud storage development, it is effective to save to cold storage blocked from a network such as an external HDD.
With only the backup, you can recover the following data even if the hostage takes damage.
File encryption · ransom request "Wanna Cry" is a worldwide pandemic and urgent patch is distributed to Windows XP, it is entering an abnormal situation, present situation & countermeasure summary - GIGAZINE

◆ Avoid excessive exposure
It is not recommended to disclose personal information with SNS. You should avoid uploading not only credit card information but also photos of airline tickets. With published information alone, you can be surprisingly exposed to information.
How to make the activity base of 'Islamic country (ISIS)' all-around with Google Earth - GIGAZINE

Opening of face photographs is also dangerous.
"Your Face Is Big Data" to identify SNS from photographs taken on the subway and compared with profile photos - GIGAZINE

Depending on the person it may be a fatal thing ......
Identification by "Face Recognition" from pictures uploading SNS to women as adult video experience - GIGAZINE

◆ Do not open attachments unnecessarily
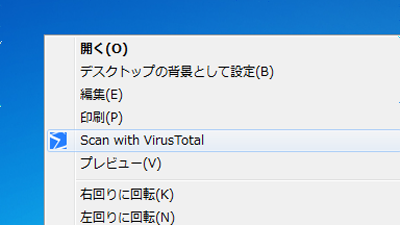
Hiding malware in attachments such as Word documents and PDFs is a classic and iron plate hacking technique that has been abused for decades. It is iron rule that you do not open suspicious files unnecessarily.
VirusTotal Uploader free software to check virus by sending file to VirusTotal with one right mouse click - GIGAZINE
As a means of checking files while keeping the local environment safe, there is also a technique called "Always save the file in Google Drive and open it in Drive". Because the files are deployed on Google's cloud, the local environment is protected.
◆ Using the iPhone
Mobile OS is a stronger system of Android and iOS, but Motherboard says it should use iOS if you value security. A big reason is that there is a digital signature called "code-signing" that guarantees that the check is more strict until the application is registered in the App Store, only by Apple, and access to other applications We point out the superiority in terms of environment such as restricted sandboxing. Also, accessibility to the latest version including security updates is also advantageous over iOS 's Android.
Approximately 80% of iOS devices are the latest "iOS 10", while "Android 7.0" has only 1% - GIGAZINE

On top of that, Motherboard says that it's better to be a Google brand smartphone such as the Nexus series or Pixel series guaranteed upgrade path to the latest OS for people who say "Android is good" by all means.
Related Posts:
in Software, Web Service, Security, Posted by darkhorse_log