10 ways to protect your Windows PC from Ransomware
ByChristiaan Colen
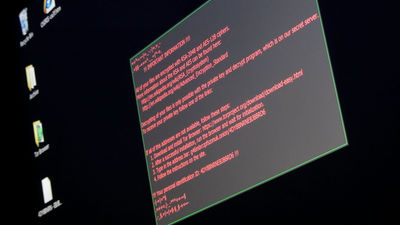
As long as you use the Internet, there are a lot of risks of being subjected to cyber attacks.It turned out that attacks using Ransomware accounted for more than 50% of all cyber attacksHowever, TechRepublic of IT related news site introduces ten ways to help protect your own Windows PC from this Ransomware.
10 ways to protect your Windows computers against ransomware - TechRepublic
http://www.techrepublic.com/article/protecting-your-windows-computers-against-ransomware/
◆ 01: Client and server patch management
Keeping your PC up to date with Windows Update is an essential action to counter known threats. In the case of zero day vulnerability, there is no way to deal with it, but Ransomware wound up in 150 countries around the world "Wanna CryIn case of patch that had been released more than two months before it appeared it did not hurt.
Patch management plays a very important role in continuous system protection. Therefore, in the case of tools used within the organization, updating stops being a big problem. Windows Server andSCCMIncluded in the serviceWindows Server Update ServicesIs a server application for update application control provided by Microsoft which enables you to manage applications in the PC including third party ones.
◆ 02: Update security software and hardware appliances
Organizations have different needs and resources to maximize network and data management. Organizations have commonalities such as "firewalls" and "intrusion prevention systems" that filter traffic at the entrances of the network, but along with firmware updates and signatures, they can be manually Security related settings can also be made.
It is also important to update the configuration to meet the needs of the network and to actively monitor the health of the device, which will strengthen the security of the network and protect you from external attacks . This does not necessarily apply only to Windows-based terminals, it can be a means to protect you from unauthorized network intrusions and attacks.
ByAlex roberts
◆ 03: Device securityHardeningTo do
Enhancing the security of clients and servers is an essential element to limit internal and external attacks. For Windows clients and Windows servers, the process will be different even if you want to enhance security aspects.
Also, correctly evaluating "which terminal to use?" Will lead to organization of the terminal. This is a useful behavior even from a security standpoint. This is because there is a possibility that a terminal that is not required or deprecated, or a terminal connected to the Internet, or even Internet, can be abused at least not much.
Note that Microsoft will conduct vulnerability assessment of devices running on devices and devices "Microsoft Baseline Security Analyzer(MBSA) ", which is available on both client and server.
◆ 04: Management of backup data
Let's back up your data. The data in the computer is as reliable as the behavior that is happening on the computer. However, once the data is corrupted or infected, it will not be reliable at once.
The best defense against Ransomware is to build an excellent backup system. In fact, there are several excellent backup systems. Back up data to multiple different media at the same time, drive local drivesIncremental backupOr keeping backups constantly on the cloud storage, even if the data is taken hostage by the rantamware, you can restore the system by choosing the best one from the three backups Is possible.
Windows The default backup and restore utility is a suitable tool for saving backups to multiple media. There is also a way to use OneDrive to leverage outstanding cloud backup features. In addition, since third-party software is released from multiple providers to manage data backups centrally or across clouds, this makes it easier to manage backup data.

ByCWCS Managed Hosting
◆ 05: Data encryption
Even if the entire data is encrypted, it can not prevent the computer from being infected with the Ranthermware. Also, if the device is infected with a virus, it can not prevent encrypted data from being further encrypted. Thus, you can use an application to sandbox encrypted data using one form of containerization, so that processes outside the API of the container application will not be able to completely read the data Can. This is an effective way to keep stored data secure, because it can prevent external access unless it is via the specified application.
However, these methods can not be used for data to be normally used or data transferred via the network. It is used in such casesVPN, You can always protect your data as if you were creating a tunnel in the data transmission and reception path.

ByMarkus Spiske
◆ 06: Configuring Secure Network Infrastructure
Unfortunately the network is often set up during the installation of new hardware, and often it remains unchecked until something goes wrong. Network equipment such as routers, switches, wireless access points etc. requires the latest firmware and appropriate settings, and proactive monitoring is needed to deal with the problem before the problem becomes full-scale.
As part of the configuration process, the optimized networkVLANOr for segment traffic and must be managed so that you can retrieve data in as efficient way as possible. Another security advantage of VLANs is that it is possible to logically isolate malicious traffic and infected hosts and prevent infection from spreading to other devices and networks. This allows administrators to deal with infected hosts without the risk of spreading the infection and can also isolate the device from the Internet until the complete VLAN is shut down and repair is complete.

BySean MacEntee
◆ 07: Policy on Network Security · Terms of Service · Data Recovery etc.
Policies are for enforcing employee compliance with rules and regulations and are essential in large organizations. However, in addition to serving as a "document for prescribing work rules," the policy will serve as a "survival guideline for end users" as well.
Although policies do not inherently prevent malware at the technical level, if properly written, address known problems and concerns about data security and provide useful information to prevent the spread of infection I will. Also, if you describe in policy so as to provide feedback on IT support, it will lead to finding problems before growing.
As technology is dynamic and changing, effective policies need to change as well. Also, keep in mind the restrictions and regulations that apply to your field, and depending on the type of industry, the preparation policy may become complicated, so you need to be prepared to handle the management team for accuracy and compliance.
◆ 08: Change of management document
As with policy settings, between documentation of the change management process (or recording all changes to the client / server, patch deployment, software upgrade, baseline analysis, etc.) and complete prevention of the randomnessware There is no direct correlation to.
However, as with other previously listed measures, the details of changes to the system configuration can have a significant impact on the ability of IT to positively or reactively respond to threats. In addition, all changes made to the system can adequately test and measure the results on the availability of services and uptime provided. Finally, the administrator, contractor, and other support staff will review and record changes (along with the results) to identify the causes of some problems and address future recurrences Offers.
You need to create and manage effective and easy document management processes from various support teams such as system administrators, help desk personnel, administrators, etc.
◆ 09: Training end users
Security measures are not necessarily to be addressed only by engineers working in IT companies. The end user gains knowledge about malware and training on security not only aims to identify malware attacks but also trains users to prevent or alleviate virus infection by themselves You should.

ByEric Schwartzman
◆ 10: Risk Management Assessment
The purpose of the risk assessment and risk management process is to identify internal and external threats and the equipment and services affected by it and analyze the potential impact. For risk assessment management, it is necessary to prioritize data assessment and risks, and to establish the best action plan to mitigate risk.
Risk assessment and risk management processes identify problems and help plan on an ongoing basis so that the problem does not adversely affect the organization. At the risk assessment and risk management process, at the very least, the IT department will be able to concentrate on efforts to coordinate the problematic device and company resources, such as mission critical systems, when infected with malware.
Related Posts:
in Security, Posted by logu_ii