Hackers hit the vulnerability to be able to board an airplane free of charge, encounter surprising response from airlines

A 20 - year - old hacker living in India discovered a bug on several Indian airline 's sites one day. By using this vulnerability, it seems that it was in a condition that it is possible to get tickets to favorite airports around the world virtually for free.
How I could have traveled the World for Free - Kanishk Sajnani - Medium
https://medium.com/@kanishksajnani/how-i-could-have-travelled-the-world-for-free-5bb10ac46ae5
I discovered this vulnerability because the crabs and surge men who live in India (Kanishk Sajnani). Sarginani, who is concerned about computer security, said he was aware of this problem when he was researching vulnerabilities of several websites and mobile applications around 2015.
◆ Case 1: Air India
It is in 2015 that Mr. Sajinani discovered vulnerability at the site of Air India, India's leading flag carrier. On November 4 of the same year, I sent a mail directly to Mr. Ashwani · Rohani who is CEO of the company and told the existence of the problem.

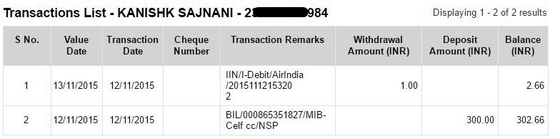
Then, about one week later on November 12, the director of the accounting department suddenly called and he was asked to reproduce the problem. In response, Sarineni actually reserved the international flight ticket from Delhi to San Francisco at a very small fee and sent back the screen.
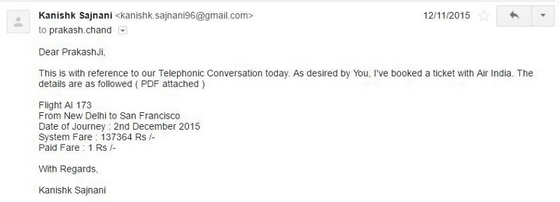
This is the screen after reservation. We booked AI 173 on December 2, 2015 in business class, and the fee stated on the screen is about 140,000 rupees (about 240,000 yen) ......
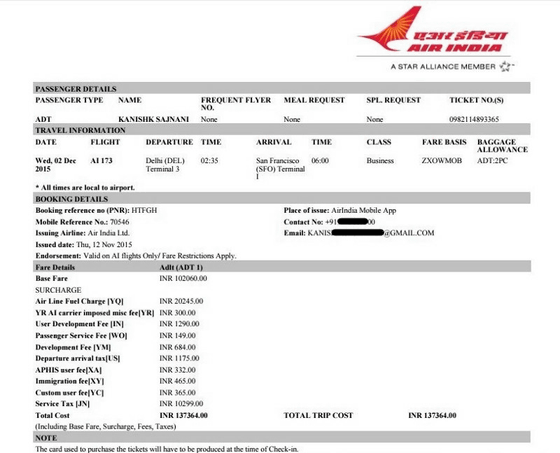
Database of reservation system · "PNR(Passenger Name Record) ", the total amount is displayed as 302.66 rupees (about 520 yen). In fact, Mr. Surge Nani has succeeded in making a reservation without paying hundreds of thousands of rupees.
Air India's chief executive who was shown the movie that recorded this reply, technical details, and proof of concept got involved in solving the problem, and then it was dissolved. In addition, he said that he returned a reply saying that he also acknowledged Ms. Saji Nani's internship at Air India, which was written at the end of the mail at the beginning.
◆ Case 2: Spice Jet
It is a cheap airline company in IndiaSpice JetMr. Surge Nani who discovered the vulnerability also in the mobile application of the company tried to contact the company's window.
The flight from Ahmedabad (AMD) to Goa State (GOI) was 4028 rupees (about 7000 yen) ......

It seems that it was in a state where only the records of about before and after were recorded, about 340 rupees about 580 yen for the record of the database.

Sarinnani who contacted SpiceJet as in the case of Airind received that he received a surprise reply. Whether it responded to the internship written at the end of Ms. Sajinani, in the received e-mail, "Please send your resume to the relevant department? Please send it to recruitment" It was written that it was written.

Sarinani finally found out the address of the person responsible for the reservation and sent the mail directly. In the reply, it says that it sent me the same content as the mail sent first, and it was written.

Mr. Sarijini responded according to the contents sent, but expectation that reply from the other side was from a person not involved in the previous exchange, and that the content which was exchanged so far is attached. It was of a form which did not exist.

Even at this stage, the ticket with the spice jet that got almost free is still valid. Since it can not be helped, Mr. Surinani said he canceled his / her reservation one month before the flight.

But at that time I was asked to refund the deposit or leave it to my account. After calling the inquiry window and confirming it, it seems that Suri Nani has the right to receive a refund of 2000 rupees (about 3400 yen).
◆ Case 3: Clear Trip
Clear trip to book air tickets and hotels (Cleartrip.com) Found a similar vulnerability. We were able to reserve all kinds of services such as airline tickets and hotel reservations that can be booked on the site, restaurants, massages, cultural events etc for free.
Mr. Surge Nani sent a mail directly to the co-founder of the company.

Then I got a reply saying "I want to call you at once" from department manager.

However, Ms. Sajinani, who had the idea of leaving a record, hopes to exchange with e-mail for the moment. Then from the other side, I heard that you received an email saying that if you can get confirmation you will prepare "appropriate compensation".

Mr. Surge Nani tells the person in charge to summarize the problem details and upload it to Google Drive and confirm it

This is the actual reservation screen

And when I canceled my reservation, I got a refund of 1199 rupees (about 2100 yen).

However, after sending out this details, the contact from the person in charge was suspended plainly. Mr. Sarginani who thought that "I guess he must have been busy" kept waiting for a while, but I thought that this is strange, I send a mail to the first co-founder's email again, It was told that "I will contact you, but after taught the details I have not heard back."

As a hacker, Sarineni wrote these three examples and got the following lessons learned.
1. Indian companies are not paying attention to security on their products
2. There are no completely secure applications or websites. Even at this point, there should be people who exploit the vulnerability without being noticed and misuse them.
3. It is when a company receives social contrition to know the importance of a bug incentive program. When hacking is received, how to minimize damage is important to the company.
Four. I can hardly appreciate "ethical hacking"
Five. It takes a long time to do the verification, but the tradeoff is small.
And what we have to change is listed as follows.
1. Development and maintenance are not all. Companies need to prepare for every possible hacking. The leakage of personal information is a major litigation risk.
2. Large companies and startups should either prepare a bug incentive program or set a responsible disclosure policy.
3. We need to thank people who taught us that there are holes in the system thanks.
Four. The cycle of analysis, reward from bug notification must be as short as possible
Five. Companies that do not hire security engineers in their own companies are also one way to use external vendors.
Related Posts:
in Web Service, Security, Posted by darkhorse_log