What is the perfect system for information control and spy discovery held by North Korean tablet "Woolim"?
In North Korea where people's traffic is restricted and information control is severe, it is difficult to obtain foreign information. The team of Florian Grunow and others has made it clear that the tablet terminal that is distributed within North Korea has its own system built for information control and spy discovery.
Mr. Grunow made a presentation about North Korean tablet "Woolim" in the information security related annual conference Chaos Communication Congress. The state of Mr. Grunow's presentation can be seen in the following movie.
C3TV - Woolim - Lifting the Fog on DPRK's Latest Tablet PC
https://media.ccc.de/v/33c3-8143-woolim_lifting_the_fog_on_dprk_s_latest_tablet_pc#video&t=3766
This time, we analyze the tablet "Woolim" sold in North Korea

Until now, it was discovered that a system that tracks the flow of media files such as images is working in the North Korean OS "Red Star OS", but it is said that the same mechanism is installed in Woolim about.

There are at least four tablets on North Korea, Woolim is one of them. Woolim is a tablet equipped with Android 4.4.2, equipped with Chinese semiconductor manufacturer Allwinner's Cortex A7 based SoC "A33", Hynix 8GB flash memory in storage. Android OS is customized for North Korea.

In fact it is quick to look at it, so we will look at Woolim's TV commercial broadcasted in North Korea.

Woolim

Woolim is a router and ...

Connectable to TV tuner.

Clear TV images can be played.

It can also be mounted on the car.

If you set up the antenna of the TV tuner you connected via USB ......

You can watch television broadcast even while you are on the move.

Because it is a digital tuner, it is a vivid picture unlike analog.

Broadcast waves are encrypted, so you can completely block other broadcast waves.

Through a LAN cable using a USB hub ......

Internet is also possible.

You can also make a wireless connection via Wi-Fi. However, since the Wi-Fi module is not built in the tablet, it is necessary to connect the wireless LAN adapter via the cable.

Because it is wireless, it does not choose to use it.

Batteries last for 4 to 5 hours.

To the emergency trouble, free rushing guarantee service is attached.

It was confirmed that Android 4.4.2 was loaded from the actual machine of Woolim obtained from its own route, and the application such as camera, education, game, browser, etc. was preinstalled.

So I started demonstration at the venue.

This is Woolim's home screen.

The application list looks something like this.

Tap on the browser's favorite ......

There are network restrictions, and the page can not be displayed.

Launch the game application.

You can play games that seems to have remodeled applications on Google Play.

Educational application.

It was typing application to practice key input operation.

It also has its own app that can open Microsoft's Office suite.

Other dictionary applications ......

North Korea version Sim City etc was preinstalled.

And, by running an application called "Red Flag" in the background, a mechanism for tracking user's behavior is incorporated.

A screenshot taken every time you launch the application. The image data can never be deleted.

In addition, browser browsing history is also recorded, but this data can not be deleted. It is likely that the intention is to warn that "I am constantly monitoring" by daringly displaying screenshots and browsing history that can not be deleted.

You can see the description of Angry Birds and Robo Defense in the list of allowed applications. Note that installation of APK file and use of recovery mode are not allowed.

And, similar to Red Star OS, Woolim adopts a mechanism to grasp the movement route of the media file by the electronic watermark function.

The figure below compares binary data when moving certain image data between Woolim terminals via SD card. Every time you move, you can see that serial information has been added.

Each time a media file is moved, unique information of the terminal is added.

When the government agency confirms the media file that circulates eventually ......

By tracing the digital watermark information added to the media file, it is a mechanism to specify the source of information.

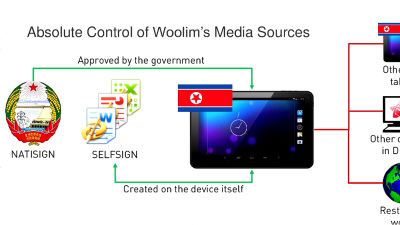
With this mechanism, the Pyongyang government can fully grasp the flow of the movement of media files, and from that route to the user's connection and relationship can be made naked.

In addition, Woolim is checking two signatures such as signature by North Korean government and signature by terminal.

Since data other than data created at the Woolim terminal is refused to open without signing by the North Korean government, a mechanism is adopted so that the North Korean government can completely control the source of media data.

Related Posts:
in Video, Hardware, Software, Smartphone, Security, Posted by darkhorse_log