An engineer with extensive experience in mobile communications explains how eSIM works
A SIM card is a card that stores subscriber information required for communication on a smartphone. Traditionally, physical cards have been used as SIM cards, but in 2016, 'eSIM' appeared as a virtual SIM card, and it became possible to immediately use the line by simply signing up online.
media.ccc.de - Demystifying eSIM Technology
https://media.ccc.de/v/camp2023-57190-demystifying_esim_technology
Harald Welte is a man deeply involved in mobile communications, having founded Osmocom , an open source software project that implements various mobile communications standards.

The first SIM card appeared in 1991 with GSM, one of the 2G communication standards. SIMs at that time were designed specifically for a single standard, GSM, and were smart cards from the beginning. A smart card is an IC card that has a processor and an operating system, rather than just memory.
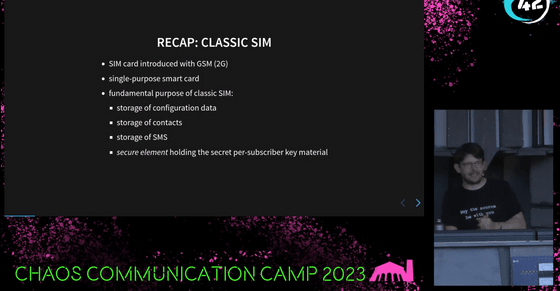
Around 2000, the 3G communication standard UMTS was introduced along with a new app for that standard called 'USIM'. At the same time, a new card that supported multiple apps called 'UICC' was also introduced so that a single SIM card could be equipped with both a conventional SIM app and a USIM app at the same time. When the transition to the 4G communication standard VoLTE was made, an additional app called 'ISIM' was installed on top of the UICC.

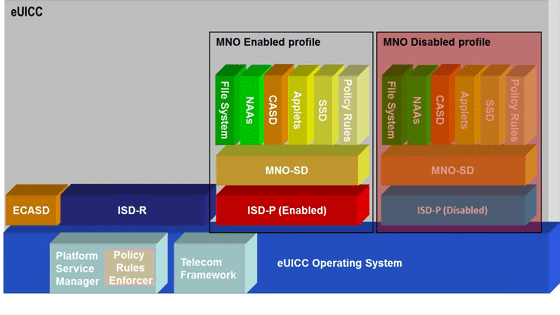
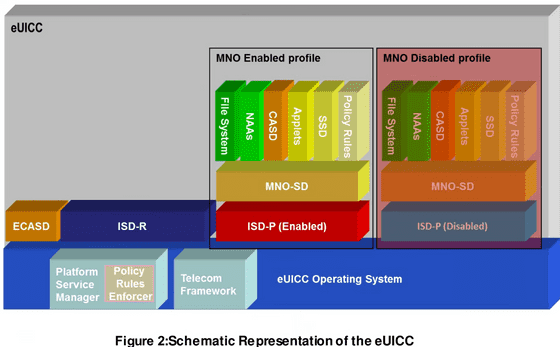
While a USIM can only hold one SIM profile, which consists of data such as contract details and authentication keys, an eSIM, a virtual USIM, separates the SIM profile from the physical chip and can hold multiple SIM profiles. The chip that can hold an eSIM is called an eUICC.

The contents of the eUICC look like this. At the bottom there is an OS called 'eUICC Operating System', and above that there is an enabled profile called 'MNO Enabled profile' and a disabled profile called 'MNO Disabled profile'. Two profiles are stored in this eUICC, one of which is enabled. The eUICC can store many profiles, but they cannot be enabled at the same time, and when one profile is enabled, the other profiles are disabled.
Because eUICC needs to update and store contract details and authentication keys without relying on a physical 'card,' it requires much higher security than conventional SIM and UICC cards.

There are three types of eSIM: M2M eSIM, Consumer eSIM, and IoT eSIM. According to Verte, the reason these three types share the name 'eSIM' is simply for marketing purposes, and the contents are quite different.

M2M stands for machine to machine, and is a server-driven mechanism that allows the owner of the machine to set a new profile remotely. In addition to the eUICC, the diagram also shows EUM (eUICC manufacturer), CI (authentication infrastructure), SM-SR (secure router), SM-DP (data preparation), and MNO (mobile network operator).
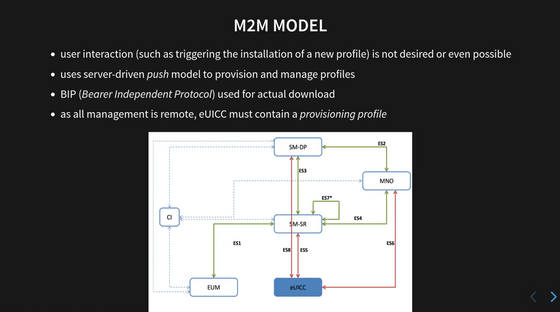
The SM-DP's job is to collect, authenticate and protect the data required to configure the SIM profile.

SM-SR is an application that manages the profile state of the eUICC, and there is one SM-SR for each eUICC.

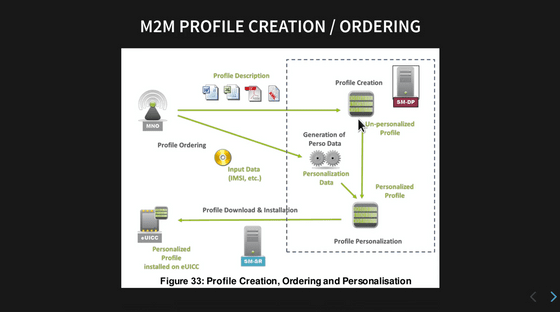
The creation of an M2M profile proceeds as shown in the diagram below. First, the MNO in the upper left sends the data required to configure the profile to the SM-DP, and creates a profile that does not include individual information in 'Profile Creation'. After that, a profile for each eUICC is created by combining the individual information, and the SM-SR downloads and installs the profile.
Consumer eSIM is an eSIM for general users, and it is this Consumer eSIM that is built into smartphones and other devices. While M2M eSIM is a server-driven 'push model,' the Consumer model is a device-driven 'pull model.' Therefore, the Consumer model does not have an SM-SR that operates the device's profile, and instead has an LPA that manages profiles on the device and an SM-DS that searches for profiles.
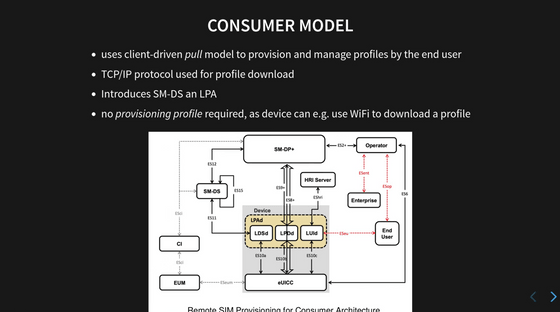
LPA is an abbreviation for 'Local Profile Assistant' and is an app that provides the UI required for managing profiles. An LPA built into an eUICC is called an 'LPAe,' and an LPA installed on a terminal is called an 'LPAd.'

The 'SM-DP+' in the Consumer model performs some of the functions of the SM-SR in addition to the functions of the SM-DP in the M2M model, which is why it has a '+' at the end of its name.
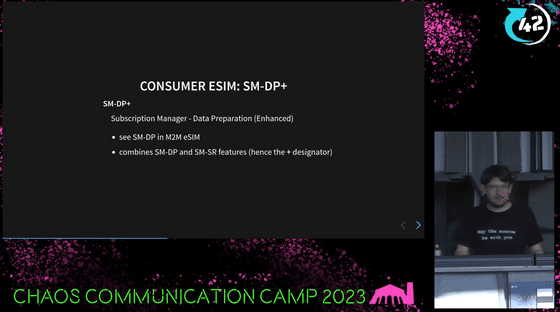
The functions of SM-DP+ are as follows: It not only generates profiles, but also stores, distributes, and manages remote profiles.
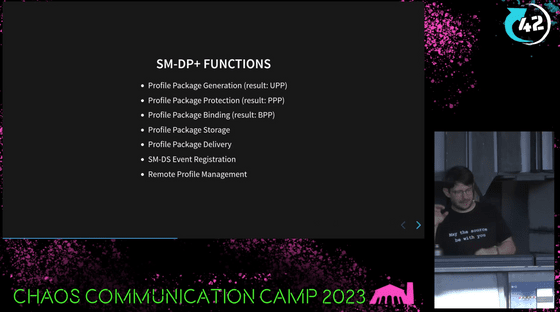
In addition to LPA, the Consumer model also includes SM-DS, which acts like a smartphone notification center, delivering notifications from SM-DP+ regardless of which network the eUICC is connected to.

The eUICC security domain is divided into three: 'ECASD' as the overall authentication infrastructure, 'ISD-R' in charge of SM-SR, and 'ISD-P' in charge of SM-DP.
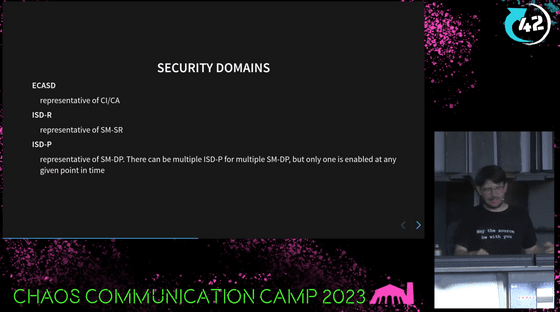
As you can see, one eUICC only has one ECASD and one ISD-R, but it may have multiple ISD-Ps depending on the number of profiles stored.

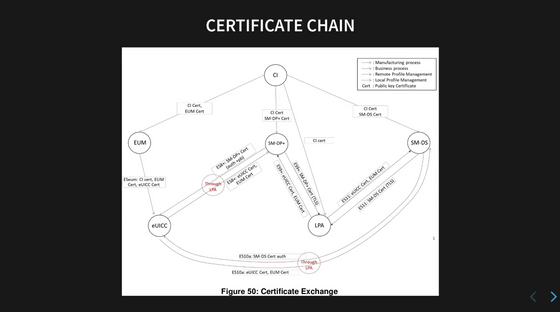
The diagram of the authentication chain looks like this. It is difficult to interpret in detail, but the GSMA, an industry association for mobile carriers, acts as the root certification authority and issues certificates for each element.
When using a Consumer eSIM, you must first go through a procedure called 'download initiation.' In this procedure, the operator (the seller of the eSIM) requests SM-DP+ to issue an ICCID, a number unique to the SIM card, and collects information such as the SM-DP+ address and matching ID required for downloading, and shares it with the user.
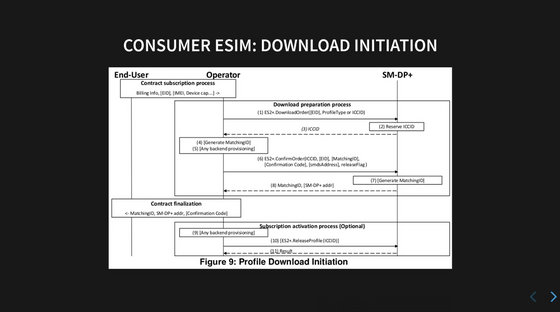
Then it is downloaded and installed. This is where the ratio of interaction between LPAd and eUICC increases.
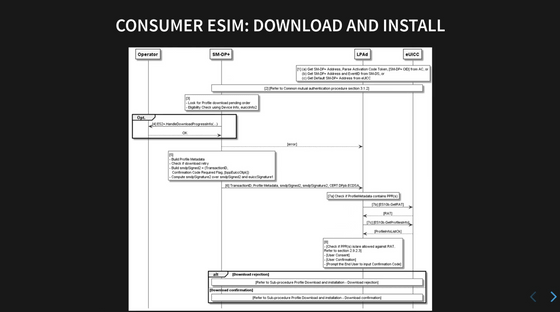
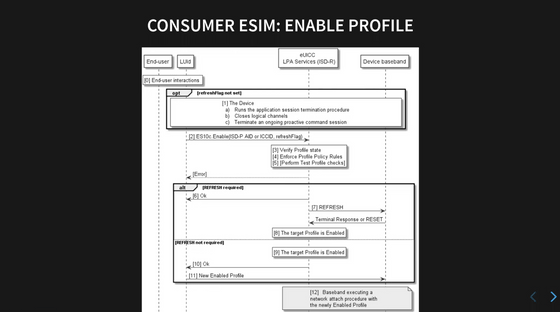
After installing a profile, you must enable it before you can use it.
The architecture and requirements specifications for the eSIM 'IoT model' were just finalized in April 2022, and the technical specifications were finalized in May 2023. The specifications are intended to overcome the problems of the M2M model, and it seems fair to think of it as a consumer model eSIM that can be operated remotely.
The architecture of the IoT model is as shown in the diagram below. It includes SM-DP+ and SM-DS, and is certainly structured like the Consumer model.
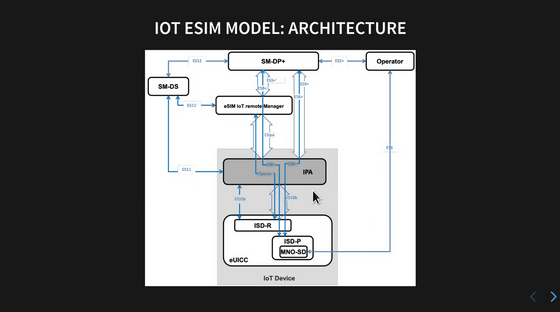
The Consumer model has an 'eSIM IoT remote manager (eIM)' added to its structure, and it is possible to trigger the download of an eSIM profile remotely through this interface.

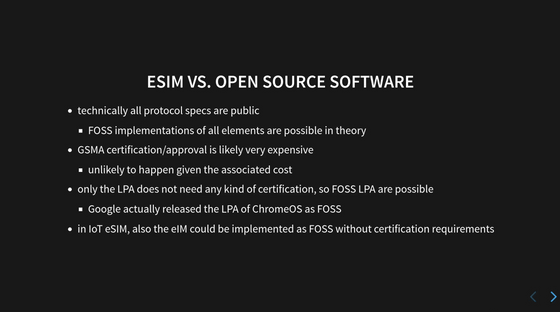
Mr. Welte is a person who places importance on the principles of FOSS (free and open source software), and in his explanation he also pointed out that eSIM can be implemented in an open source manner.
Related Posts: