Malware "Tyupkin" to pull out all cash in ATM

Antivirus softwareKasperskyIt is the research institution ofGlobal Research and Analysis Team(GReAT) conducted a cyber crime investigation upon request from a financial institution, it was possible to withdraw the entire contents of a banknote cassette by adding a manual operation to the ATM, "TyupkinA malware called "It was discovered.
Tyupkin: Manipulating ATM Machines with Malware - Securelist
https://securelist.com/blog/research/66988/tyupkin-manipulating-atm-machines-with-malware/
A demonstration in which Tyupkin is actually withdrawing cash from ATM can be seen in the following movie.
Infected ATMs give away millions of dollars without credit cards - YouTube
First, press "Enter" on ATM's numeric input button.

Then the operation screen that was hidden by the hidden malware was displayed on the ATM display.
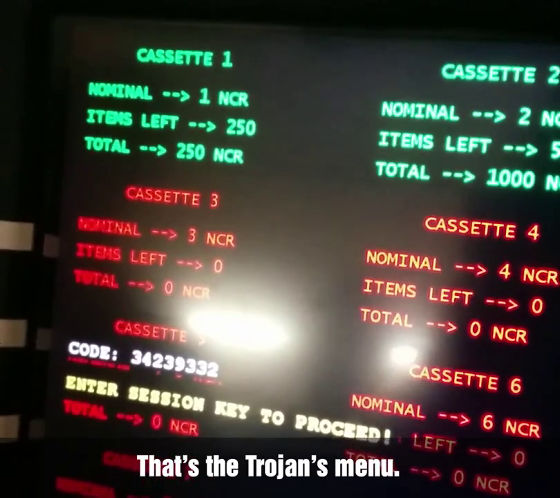
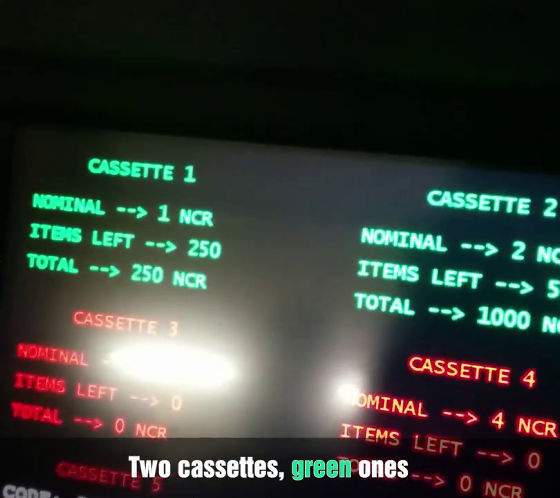
In a banknote cassette that is displayed in green, it means "there is cash", and the cassette displayed in red is not used. The balance of each cassette is also displayed.
The password "CODE: 34239332" is displayed to clear out cash.
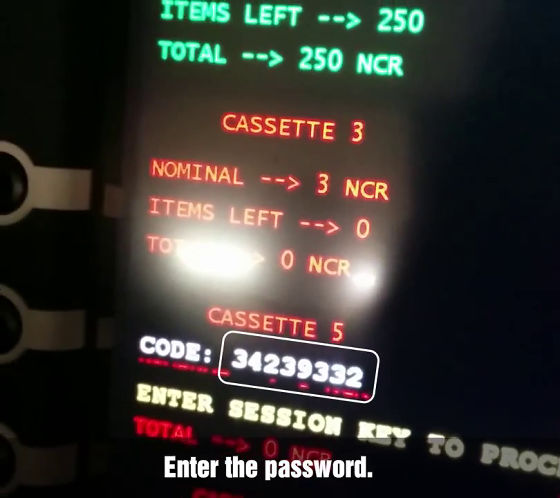
This is typed with a number input button.

It seems to have succeeded.

In addition, we typed in numbers "2, 0, 0, 4, 4, 2, 9".

Press enter.

Then select the number of the cassette you want to withdraw cash and press enter.

"Which do you want to be the first one?"

Select "Cassette 1" and press enter ... ....

What, Gossori and 40 paper bundles came out from the takeout opening. There are 40 banknotes to be taken out at a time, but if it repeats, we will be able to withdraw cash until the banknote cassette is empty.

This malware has been confirmed in more than 50 financial institutions in Eastern Europe, and the infection is spreading to the United States, India, and China. Analysis of the infected ATM surveillance camera showed that malware installationBootable CDIt was used. In addition to activating only for a specific time in the midnight, all sessions can not be executed without typing keys based on pseudo-random numbers in order to avoid perception.

It seems that 32-bit version of Windows based ATM is affected, and the latest version called "Version.D" implements the debugging and emulation technology countermeasure function, and has the function to make McAfee unusable And that. Although infection in Japan has not been confirmed, Kaspersky Lab has "[email protected]" as a point of contact for those who wish to confirm.
Related Posts:







