Online shopping sites infected with malware that steals information such as credit cards continue to increase

by
It is a variant of the crime ' skimming ' that steals data recorded in credit cards etc., and 'card skimming malware' that steals customer information from online shopping sites etc. is steadily increasing, and it is infected even at major shopping sites. It has been reported that there are cases in which
A new rash of highly covert card-skimming malware infects ecommerce sites | Ars Technica
https://arstechnica.com/information-technology/2019/03/a-new-rash-of-highly-covert-card-skimming-malware-infects-ecommerce-sites/
According to Russia-based cyber security company ' Group-IB ', more than 500,000 a month each such as Fila.co.uk/jungleeny.com/forshaw.com/absolutenewyork.com/cajungrocer.com/getrxd.com/sharbor.com. Seven online shopping sites boasting a high number of accesses have been infected with common card skimming malware. Of these, Fila.co.uk successfully removed card skimming malware, but the remaining six remain infected. In fact, access to getrxd.com, which is an infected site, has been denied by anti-virus software.
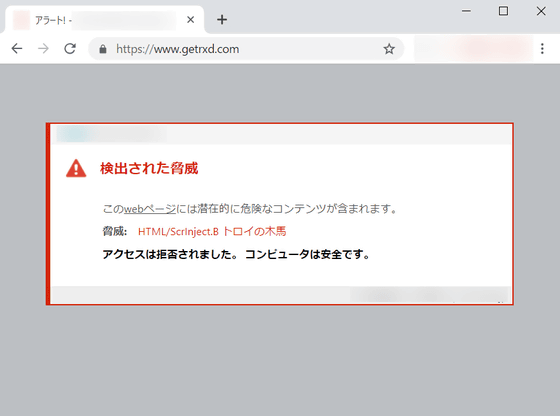
Group-IB named this card skimming malware 'GMO'. GMO is believed to have been manually infected in May 2018 on a site dealing with an e-commerce platform called Magento e-commerce. GMO is said to have the ability to impersonate sleeping if Firebug, Google Developer Tools, etc. are activated on the PC.
There are various types of card skimming malware as well as this GMO. Group-IB

by stokkete
For many electronic payment cards, fraudulent use of the card is the responsibility of the dealer, but it is unclear whether all dealers will guarantee in all cases. In addition, credit cards and debit cards are supposed to compensate for illegal use , but in some cases they may not be eligible for compensation, or even if they can get compensation, it is quite time-consuming to replace the card. It takes In order to detect such abuse, card users should check their usage details etc. themselves.
Related Posts:
in Security, Posted by darkhorse_log







