Possibility that a fake mobile phone base station is intercepting smaho's communication

ByMatt Karp
Mobile phone base stations that communicate wirelessly with mobile terminals such as mobile phones and smart phones are located all over the world, but in the United States there are fake items in the cell phone base stations installed, and the citizens use it The possibility of collecting information from smartphones is pointed out.
Mysterious Phony Cell Towers Could Be Intercepting Your Calls | Popular Science
http://www.popsci.com/article/technology/mysterious-phony-cell-towers-could-be-intercepting-your-calls
Mr. Edward SnowdenExposing NSA's monitoring programIn America, the number of users worried about the security of the device to be used is increasing. Receiving the voice of those usersESD AmericaCompany called Samsung ElectronicsGalaxy SIIISmartphone developed based on "CryptoPhone 500"Has been released. CryptoPhone 500 is equipped with Android which the company independently customized and improved security. According to Les Goldsmith, CEO of ESD America, it is CryptoPhone 500 that removed 468 vulnerabilities from Android installed on a typical smartphone.
This is CryptoPhone 500. Although it is more expensive than a typical smartphone, it features enhanced security over regular Android devices, such as encrypting calls and messages.

Goldsmith asserts that "there is something that CryptoPhone 500 can not do with a usable Android terminal." that is"InterceptorTo be able to detect fake cell phone base stations named " The map created by the company and CryptoPhone 500 users using this terminal clearly states the location of 17 interceptors.
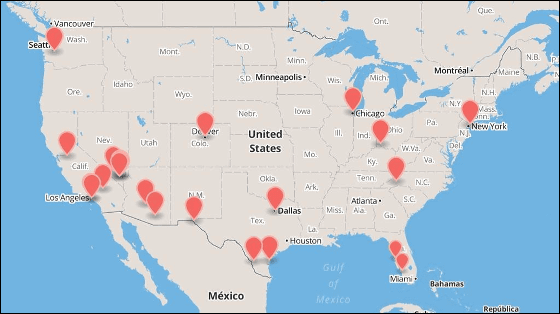
According to Goldsmith, the interceptor is the same as an ordinary mobile phone base station, but when the smartphone is connected to the interceptor, it becomes possible to attack eavesdropping of calls and spyware on the terminal via wireless communication It is said to be.
Mr. Goldsmith said, "I do not know what was clear about the organizations that set up the interceptor and the purpose of construction, but as to whom we are setting up a cell phone base station that will enable cyber attacks for whatever purpose, It has been found that all the positions of the interceptors found are within the US military base, and it is usually thought that the US government has set up an interceptor in the base, but the possibility that other countries have established can not be ruled out Speaking.
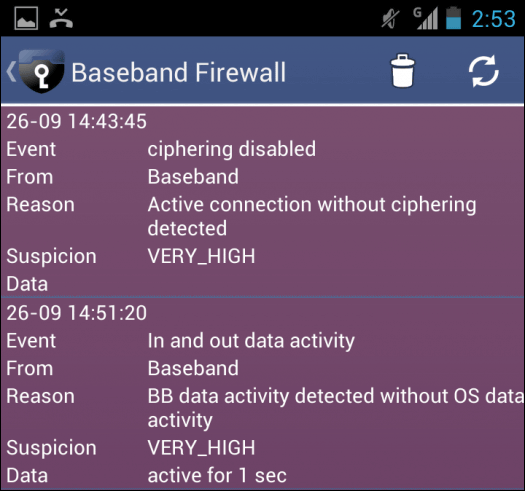
Interceptors are like PCs with software that can break through encryption using a special cellular network protocol. For all devices equipped with Android and iOS, it is called the second OSRTOS(Real-time operation system) is built in, RTOS is a smartphone'sBaseband processorIt operates on a semiconductor integrated circuit. The baseband processor is like a relay point between the main OS and mobile phone base station, and the interceptor performs eavesdropping of speech and spyware attack through the baseband processor.
The ESD America security team investigated the firewall of the usual Android terminal and it turned out that 80 to 90 data leaks occurred every hour, and as a result of tracking the signal, the existence of the interceptor is obvious became. "CryptoPhone 500 has a specially enhanced security OS with a baseband attack detection feature that allows you to locate interceptors," Goldsmith says.
In the United StatesNSA was eavesdropping 5 billion mobile phones all over the world in one dayIt is unknown whether or not it is the same as the mobile base station found this time, but it will pretend to be a mobile phone base station and gather information from smartphoneThe police conducted an investigation called "Stingray"It is clear in the trial that the interceptor claimed by Goldsmith is a hard to believe story, but even if it is true there is no question.
Related Posts: