A former hacker explains the details of the method of leaking a large amount of nude images via iCloud and how to deal with it

By
In a mass leak of nude images of Hollywood actresses, singers, and models, Apple admitted that the images were stolen from the company's cloud service iCloud, but multiple media reported at the beginning of the incident. He denied the possibility of ' hacking into iCloud ' or ' brute force attack with the vulnerability of Find My iPhone developed by the company'. So , how did the image stored in iCloud leak out, and details of the method, entrepreneur who was involved in many startups such as Techcrunch and Omnidrive, but with the title of hacker, security related article Published by Nik Cubrilovic, who has written many articles.
Nik Cubrilovic> Notes on the Celebrity Data Theft
https://nikcub.me/posts/notes-on-the-celebrity-data-theft
The statement released by Apple about the image leak is as follows, admitting that the image leaked from iCloud, but denying that there was a hack on iCloud itself or an attack using the vulnerability of Find My iPhone. Regarding the cause of the image leak, he stated that 'it was illegally accessed by a cyber attack targeting the iCloud user name and password registered by the targeted Hollywood actress, singer, and model.'
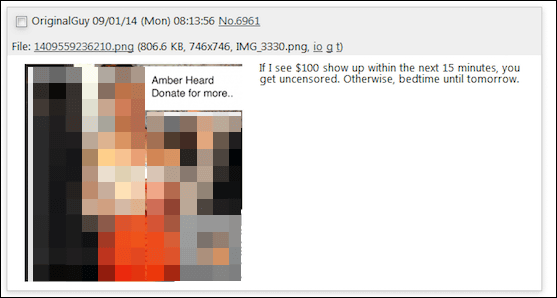
According to Mr. Cubrilovic, who independently investigated the image leak incident, the leaked image was posted on the bulletin board a week before the incident was discovered, but the image was mosaicked. Since the mechanism was such that only the user who paid the fee could obtain the original image, the bulletin board did not become a festive event. However, the image was spread explosively as the user who purchased the original image posted it on the bulletin board.
There are many unique communities and networks on the Internet where many hackers exchange information and data, and these stolen images are being traded in those places. 'Hacker communities and networks have separate roles in conducting cyber attacks and exchange information using tools such as email and instant messenger,' Cubrilovic explains how cyber attacks work. ..
Hackers who collect all kinds of information from SNS such as Facebook and Twitter are the basis of cyber attacks. We do not choose any means for collecting information, and we also collect data and credit card information stored in public institutions using paid services. It seems that it may create a fake target account from the collected information and approach the target's friends etc. to collect information that may be a hint for passwords and secret answers.
There are other hackers who use the data collected by the hackers mentioned above to derive answers to their target usernames, passwords, and secret questions. These hackers may
Then, using the analyzed user name, password, secret question, unauthorized login to the cloud service, unlocking the password protection, software that allows free access to the disk and system, pirated version of
In this image leak incident, users of Apple's iCloud were targeted by hackers because the backup of the camera roll that automatically synchronizes with iCloud is turned 'ON' by default. There seems to be. Of course, Windows Phone and Android devices can also be targeted, but since both OSs do not back up to the cloud by default, it is easiest for hackers to target iPhone users who have not changed the initial settings.
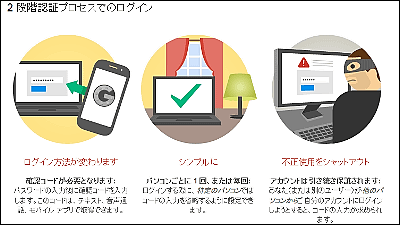
Cubrilovic said, 'Set passwords to complex ones', 'Make secret questions long with random strings', and 'Perform two-step verification' as a defense against cyber attacks that anyone can execute. Is listed. However, there is no perfect defense, so you need to turn off automatic synchronization to cloud services to raise your security awareness on a regular basis.
Related Posts:
in Note, Posted by darkhorse_log