It turns out that the operator of the web service performing DDoS attack is working at FBI

By[Martin]
According to a survey conducted by journalist Brian Krebs, a web service performing DDoS attackRagebooter.netIt turns out that the operator of FBI is working. Not only did FBI admit the existence of web services, it turned out that they actually accessed the service.
Ragebooter: 'Legit' DDoS Service, or Fed Backdoor? - Krebs on Security
https://krebsonsecurity.com/2013/05/ragebooter-legit-ddos-service-or-fed-backdoor/
Ragebooter.net is a web service that floods communication traffic, and its way is to perform DNS reflector attacks. In other words, by misrepresenting the source IP address sending the lookup request and reflecting it to the open DNS server, it generates 50 times the original data and floods the target traffic.

ByMarsmet 481
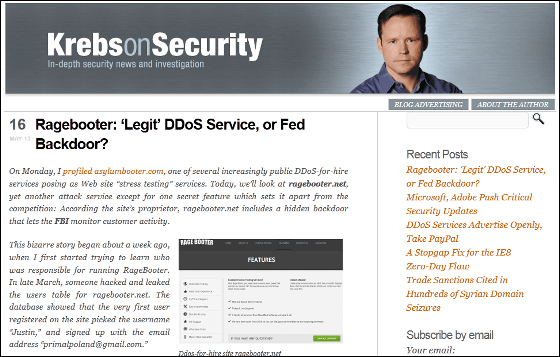
Journalist Brian Krebs investigated this service and found out that the service is managed by Justin Poland (22) living in the United States · Memphis USA and interviewed it.
According to Poland, "This service is a public service, it is not illegal." According to Krebs' interview, he said, "It is not illegal to misrepresent the sender's IP address, and if the root user of the server does not want to do that, they can easily make DNS server recursive queries It is possible to set not to accept it.The service is a legal pilot service and the use is due to individual risk and responsibility.I advertise this service or recommend illegal usage method I have submitted a 7-day log based on the law. "
Below is a website "RAGE BOOTER" operated by Poland
RAGE BOOTER - Index Page
http://ragebooter.net/
In addition, Poland works at FBI every Tuesday, but FBI admits Poland 's business, and he actually accesses the service. Also, when actually using the service to monitor the activity of online users, when logging in, it seems that the IP logger records the user's IP. Furthermore, FBI has not commented on this matter yet.

ByGruntzooki
Security researchers have found the user name of Ragebooter.net from the data of the website that was the target of attack, and in March someone hacked Ragebooter.net, leaked the User table, User name, e-mail address, etc. are leaked. Ragebooter.net is believed to be attacking more than 400 attacks a day, and this list contains a lot of data.
Related Posts:
in Note, Web Service, Posted by darkhorse_log