A story about a server being hacked and forced to mine cryptocurrency without permission is becoming a hot topic

Software engineer
I got hacked, my server started mining Monero this morning. | Unfinished Side Projects
https://blog.jakesaunders.dev/my-server-started-mining-monero-this-morning/
Sanders had contracted a server with German-based hosting company Hetzner and published his blog and website. However, on December 17, 2025, he received an email from Hetzner stating, 'We have detected signs of an attack,' and 'If we are unable to determine the cause of the problem and what action to take, your server may be blocked.' The email also contained an attached log showing unauthorized access from Thailand.
To investigate the server's status, Sanders ran the 'ps aux' command, which displays process information. As a result, it was discovered that the CPU was under a massive load of 819%. The process name was the name of the Monero mining tool xmrig, and it became clear that someone had illegally accessed Sanders' server and mined Monero for 10 days from December 7, 2025.
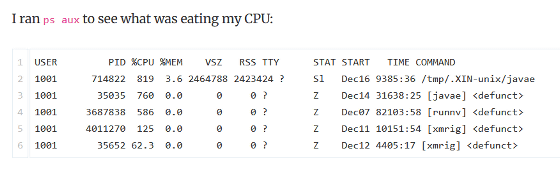
Further investigation revealed that the mining process was running within the container of the analytics tool ' umami .' The unauthorized access was caused by a vulnerability in Next.js reported as ' CVE-2025-66478 .'
In early December, Sanders saw a post from someone claiming that a vulnerability in Next.js had led to a server being hacked and used to mine Monero, but he didn't take any precautions, thinking, 'I don't use Next.js, so I'm fine.' However, Umami is built with Next.js, and the vulnerability was exploited, leading to unauthorized access.
I've been hacked
— Eduardo Borges (@duborges) December 6, 2025
and traced the malware's wallet to see how much money they actually made from this new exploit
(if you use Next.js/React, READ THIS!)
I woke up to a terrifying email from Hetzner: 'Netscan Detected.'
my server was blocked and a botnet was using my IP to… pic.twitter.com/CbyjNB93at
After identifying the cause of the problem, Sanders took action, contacted Hetzner, and was able to continue using the server. Sanders said the unauthorized access taught him the lesson of 'carefully checking the dependencies of the software you use.' He said he will continue to use Umami by updating it to the latest version.
There have also been reports in Japan of servers being hacked and used for Monero mining. The following link explains how an EC2 server contracted for personal development was used for Monero mining and what to do about it.
A story about a personal EC2 server being hijacked and mining Monero [CVE-2025-55182] | Nekoroko
https://note.com/nekoroko/n/n729421e1cf8d
Related Posts:
in Security, Posted by log1o_hf