Pixnapping, a cyber attack that can steal two-factor authentication codes from Android devices in under 30 seconds
Pixnapping , a new cyber attack that allows malicious Android apps to secretly leak information displayed in other Android apps or on any website, was reported by researchers at the University of California, the University of Washington, and Carnegie Mellon University.
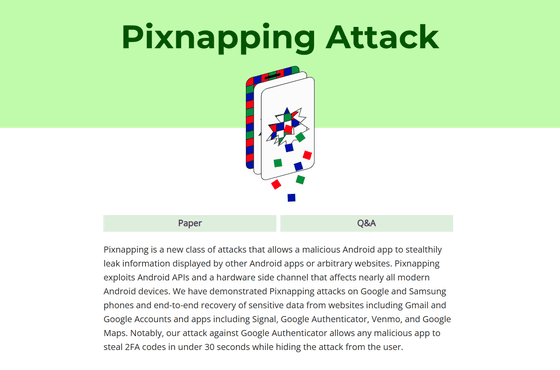
Pixnapping Attack
Hackers can steal 2FA codes and private messages from Android phones - Ars Technica
https://arstechnica.com/security/2025/10/no-fix-yet-for-attack-that-lets-hackers-pluck-2fa-codes-from-android-phones/
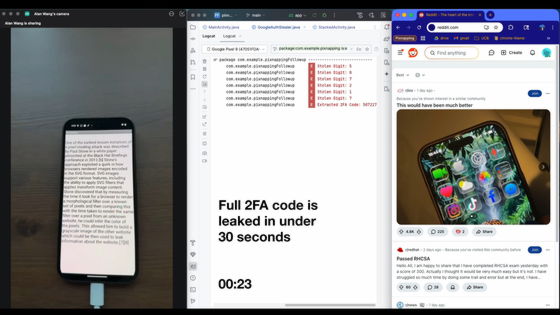
Pixnapping is a cyberattack that exploits Android APIs and hardware side-channel attacks that affect nearly all modern Android devices. By exploiting Google and Samsung smartphones, Pixnapping can recover sensitive data end-to-end from websites like Gmail and Google Accounts, and apps like Signal, Google Authenticator , Venmo, and Google Maps. Specifically, Pixnapping can steal two-factor authentication (2FA) codes from Google Authenticator, a two-factor authentication app developed by Google, in under 30 seconds while remaining concealed.
Google Authenticator updates its two-factor authentication code every 30 seconds. Pixnapping launches Google Authenticator and records the two-factor authentication code pixel by pixel, then uses optical character recognition (OCR) to recognize it. The developers explain that 'conceptually, it's like taking a screenshot of screen content that a malicious app shouldn't have access to.'
Pixnapping apparently works by forcing pixels into the rendering pipeline and overlaying a semi-transparent activity on top of those pixels via an Android intent. To direct graphics operations to those pixels, the instantiation uses Android's window blur API . Pixnapping also relies on a GPU.zip side channel to leak the pixels.
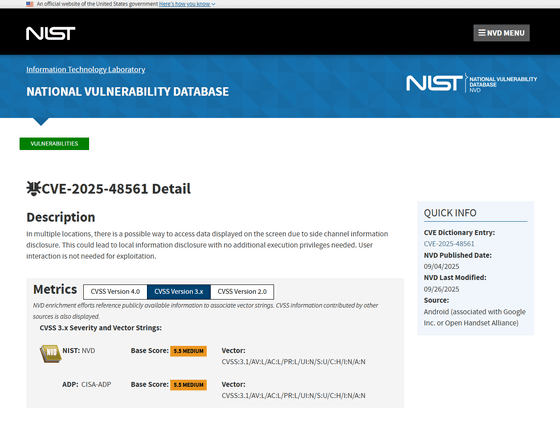
Pixnapping is tracked in
NVD - CVE-2025-48561
https://nvd.nist.gov/vuln/detail/CVE-2025-48561
The research team demonstrated a proof-of-concept for Pixnapping on Pixel 6, Pixel 7, Pixel 8, Pixel 9, and Galaxy S25 devices running Android 13-16. However, it has not been confirmed whether other Android devices are affected by Pixnapping. However, the developers point out that the core mechanism that enables the attack 'is present in all Android devices.'
Pixnapping can carry out this attack even without permission (no permissions specified in the manifest file). Everything you see when you open a target app can be stolen by a malicious app using Pixnapping, so chat messages, two-factor authentication codes, emails, etc. are all vulnerable. This means that information hidden from the app (such as a private key that is stored but not displayed on the screen) is safe from Pixnapping.
The developers say they are 'unclear' about the possibility of Pixnapping being exploited in real life, and recommend that Android users 'install the patch as soon as it becomes available.' Google is attempting to limit Pixnapping's functionality by limiting the number of activities that the window blur API can perform. However, the developers have discovered a bypass method that allows Pixnapping to work even when restrictions are imposed on the window blur API.

For Android app developers, the company said, 'We are not currently aware of any mitigation measures to protect apps from Pixnapping. If you have knowledge of any mitigation measures, please let us know.'
The research paper on Pixnapping will be presented at ACM CCS 2025, which will be held in Taiwan from October 13, 2025.
Related Posts:
in Free Member, Software, Smartphone, Security, Posted by logu_ii