3 million iOS and macOS apps exposed to powerful supply chain attack

It has been revealed that vulnerabilities have existed for the past 10 years in
3 million iOS and macOS apps were exposed to potent supply-chain attacks | Ars Technica
https://arstechnica.com/security/2024/07/3-million-ios-and-macos-apps-were-exposed-to-potent-supply-chain-attacks/
Millions of iOS apps were exposed due to CocoaPods security breach
https://9to5mac.com/2024/07/02/ios-apps-security-breach-cocoapods/
The vulnerability was reported by a research group at security firm EVA Information Security . When changes are made to 'pods,' which are individual code packages, apps that use CocoaPods are usually designed to automatically incorporate the changes through app updates, without the need for end-user intervention.
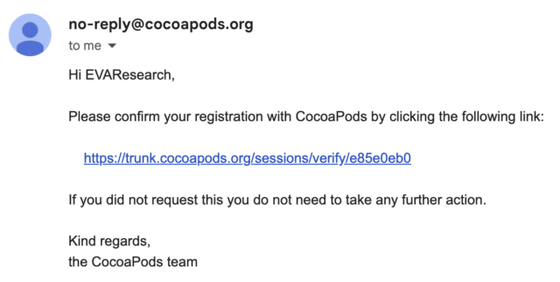
EVA Information Security discovered three vulnerabilities in CocoaPods due to an insecure verification email mechanism used to authenticate the developer of an individual pod: the developer would enter an email address associated with the pod, and the trunk server would respond by sending a link to that email address. When the user clicked on this link, they were able to access their account.
Regular verification email sent by CocoaPods
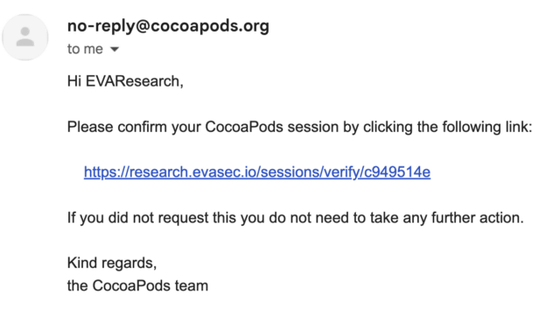
However, the researchers noted that the attackers were able to send a link to a server they controlled, disguised as a response email from a trunk server. The server accepted the forged XFH as an HTTP header to identify the target host specified in the HTTP request. 'The forged XFH could be used to construct any URL,' EVA Information Security researchers noted.
Researcher forged verification email
The three vulnerabilities discovered by EVA Information Security are as follows:
・
・CVE-2024-38368
・CVE-2024-38366
By exploiting this feature and injecting malicious code into the app, attackers could gain access to users' personal information, such as credit card information and medical records, to launch ransomware attacks or conduct corporate espionage. 'Attackers can access users' personal information and use it for almost any malicious purpose imaginable, including ransomware, fraud, blackmail, and corporate espionage. In the process, companies could be exposed to significant legal liability and reputational risk,' the EVA Information Security research team said.
CocoaPods maintainers disclosed these vulnerabilities in October 2023 and distributed fixes. At the time of patch distribution, the maintainers said, 'Being able to execute arbitrary shell commands on the server gives an attacker the ability to read environment variables, write to the CocoaPods/Specs repository, and read the trunk database.' 'By tricking a user into clicking a link and directing them to a third-party site, they could steal the session key. We don't know if this happened, but we want to be on the safe side.'
'The worst-case scenario is that an attacker could use this technique to obtain a session key, gain access to an app developer account, and connect authenticated users to a pod,' said a CocoaPods maintainer. After privately notifying CocoaPods developers of the vulnerability, EVA Information Security researchers erased all session keys to ensure that no one can access the account unless they control the registered email address.

In addition, CocoaPods has added new steps to recover old orphaned pods, which require contacting the maintainer directly. No action is required on the part of app developers or users of the apps, but EVA Information Security researchers are advising 'app developers who used CocoaPods before October 2023' to follow the steps below.
Syncs the podfile.lock file with all CocoaPods developers to ensure that everyone is using the same versions of packages. This prevents developers from automatically updating when new, potentially harmful updates are committed.
If you are using pods that were developed in-house and are only hosted on CocoaPods for mass distribution, developers should run CRC (checksum) verification on what they download from the CocoaPods trunk server to ensure it is the same as what was developed in-house.
- Implement a thorough security review of any third-party code used in your application.
Check your CocoaPods dependencies and make sure you're not using any orphaned pods.
-Make sure you use third-party dependencies that are actively maintained and have clear ownership.
- Regularly run security code scans to detect malicious code in all external libraries, especially CocoaPods.
Be careful with highly widely used dependencies as they may represent a more attractive target for potential attackers.
'The potential code changes could affect millions of Apple devices worldwide, including iPhones, Macs, Apple TVs and Apple Watch devices,' researchers at EVA Information Security said.
Related Posts:







