15-year-old boy develops zero-click attack that reveals target's location without being noticed

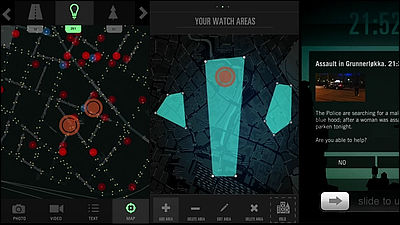
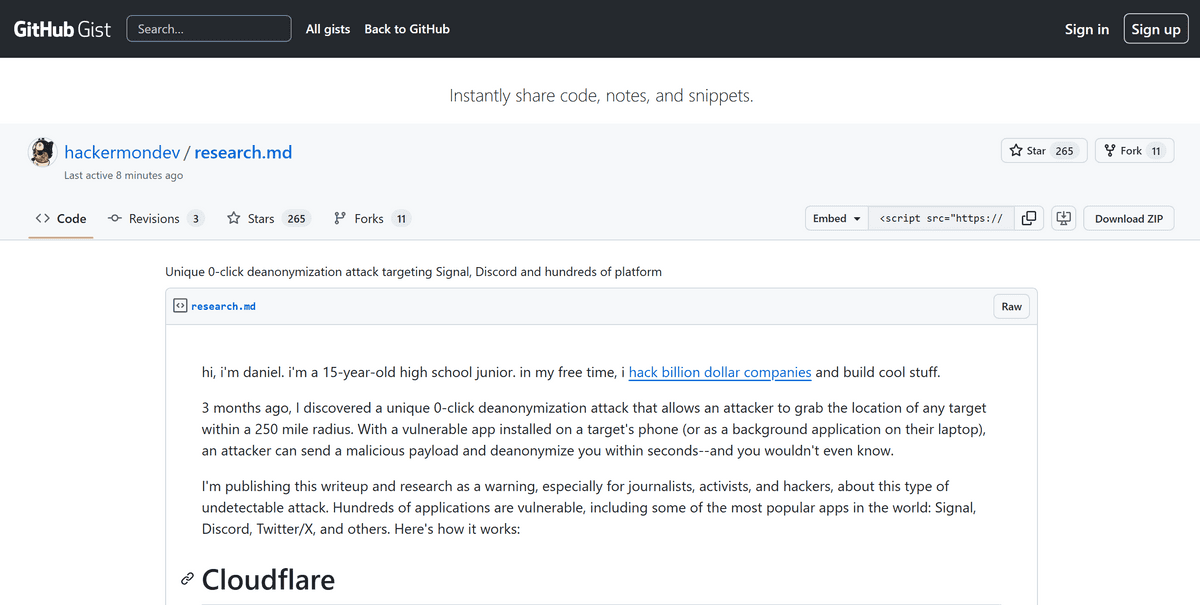
A 15-year-old high school senior who goes by the name 'Daniel' has developed an attack technique that uses a wide range of commonly used tools, including Signal, Discord, and X (formerly Twitter), to unwittingly obtain a target's approximate location.
Unique 0-click deanonymization attack targeting Signal, Discord and hundreds of platforms · GitHub
https://gist.github.com/hackermondev/45a3cdfa52246f1d1201c1e8cdef6117
Daniel's attack method takes advantage of the caching mechanism of Cloudflare's CDN service. When a user accesses a resource delivered by Cloudflare, Cloudflare directs the user to the nearest data center, and if the resource is cached in that data center, it returns the cached resource, and if not, it retrieves the resource from the origin server.
Cloudflare's data centers are located in over 330 cities in over 120 countries, each of which is assigned the airport code of the nearest airport. The response header of a resource retrieved through Cloudflare contains information about which data center it was passed through.
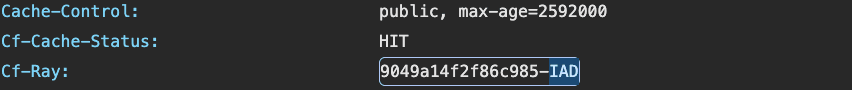
Although users cannot explicitly select the data center to route through, Daniel was able to specify the data center to route through by using Cloudflare Workers and using Cloudflare's internal IP. For a specific resource, it is now possible to know for each data center whether the resource is cached and how long it has been cached.
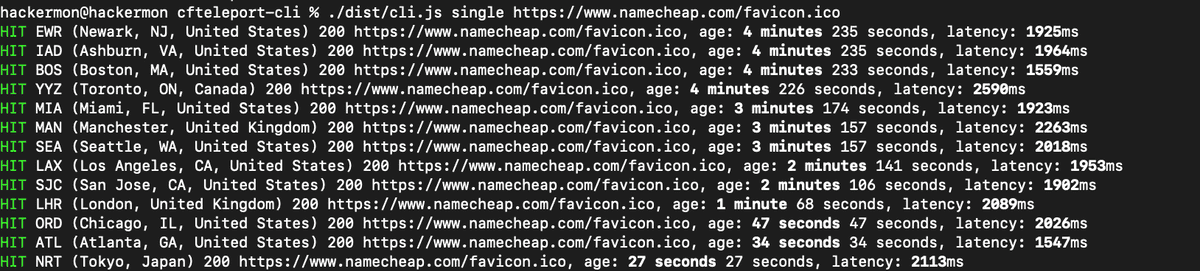
Daniel tested the attack using
Signal , a messaging app that boasts 'tight security.' When a user sends an image on Signal, it is delivered via Cloudflare.
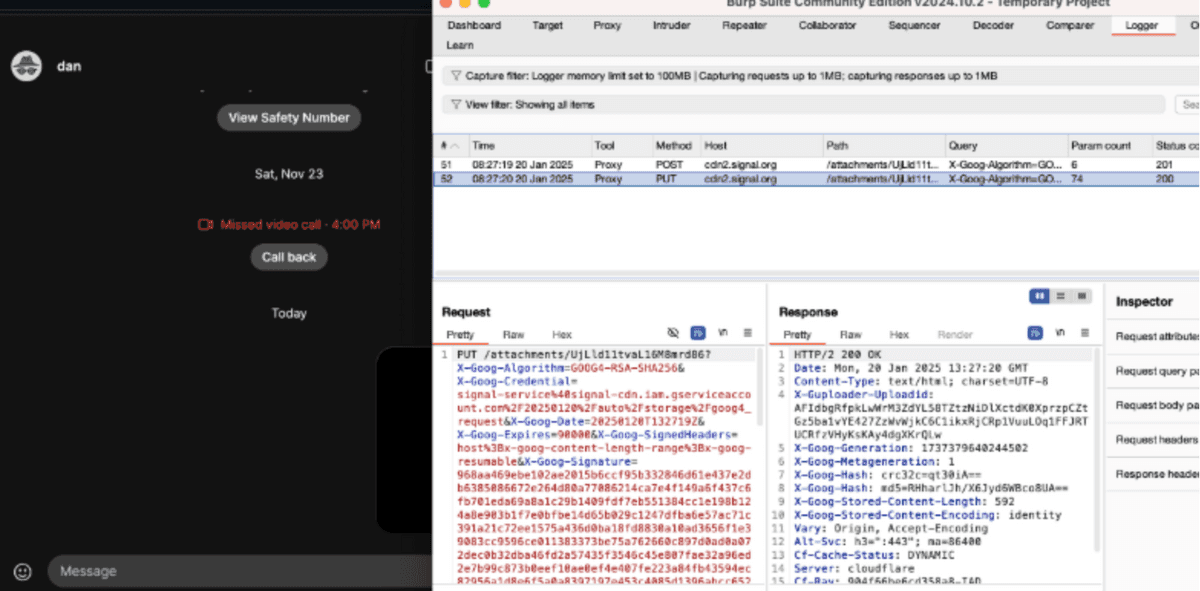
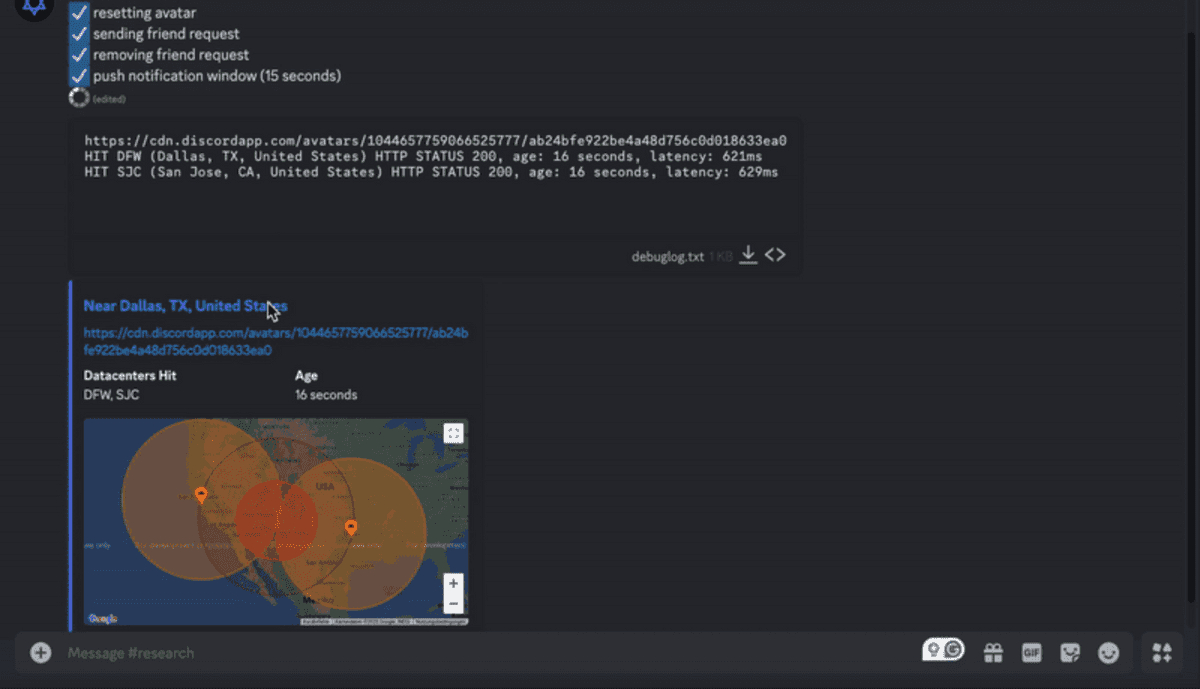
When the target opens the chat screen and checks the image, the image is cached in the data center nearest to the target. By checking the cache status of each data center, the attacker can confirm which data center the target lives near. In Signal's experiment, the cache was left in a data center in New Jersey, a state next to New York, where the target was actually located.
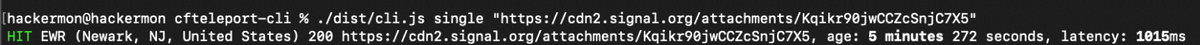
In the above example, the target needs to open the chat screen and view the image, but if the notification settings are set to notify the content, the attacker's general location will be revealed simply by sending an image.
Daniel also demonstrated that the attack can be carried out on the chat and calling service Discord. After creating a Discord account, when you send a friend request to the target, the target will receive a notification with a profile picture.

Since Discord profile images are distributed by Cloudflare, by checking the cache status of the profile image, you can find out which data center you live near.
Cloudflare fixed the bug that allowed users to specify a specific data center and access it after receiving Daniel's report. However, Daniel said that the problem was not fundamentally solved because users could effectively specify the data center by using a VPN. Ultimately, Cloudflare stated that it does not consider this attack to be a vulnerability in the Cloudflare system and that it is the user's responsibility to disable the cache for resources that need protection. Meanwhile, Discord, a user, said that it was a Cloudflare issue because other users were also affected.
Daniel summarized the attack, saying, 'While CDNs improve performance and scalability, they also inadvertently introduce risks that can be exploited in new ways.'
Related Posts:
in Software, Web Service, Security, , Posted by log1d_ts