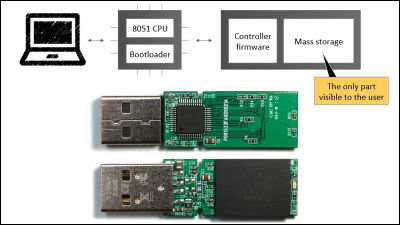
It has been demonstrated that it is possible to hack a laptop's webcam to secretly take pictures without turning on the LED

Linux kernel security engineer Andrey Konovalov has demonstrated that the LED of the ThinkPad X230 webcam can be controlled by code, allowing malware to take pictures using the webcam without turning on the LED and without the user's knowledge.
GitHub - xairy/lights-out: Tools for controlling webcam LED on ThinkPad X230
https://github.com/xairy/lights-out
2024, PoC: Lights Out: Covertly turning off the ThinkPad webcam LED indicator
(PDF file)
https://powerofcommunity.net/poc2024/Andrey%20Konovalov,%20Lights%20Out%20-%20Covertly%20turning%20off%20the%20ThinkPad%20webcam%20LED%20indicator.pdf
At the annual International Security Hacking Conference POC held in Korea, Konovalov gave a talk on 'How I manipulated the ThinkPad's webcam LED.' In addition, he created a tool called 'Lights Out' that actually manipulates the ThinkPad's LED and released it on GitHub.
The ThinkPad X230 webcam is internally connected to the PC via USB. Lights Out works by rewriting the firmware of the webcam via USB, so it can work without physical access to the PC. If it is exploited by malware, there is a risk of violating the user's privacy without the user's knowledge.
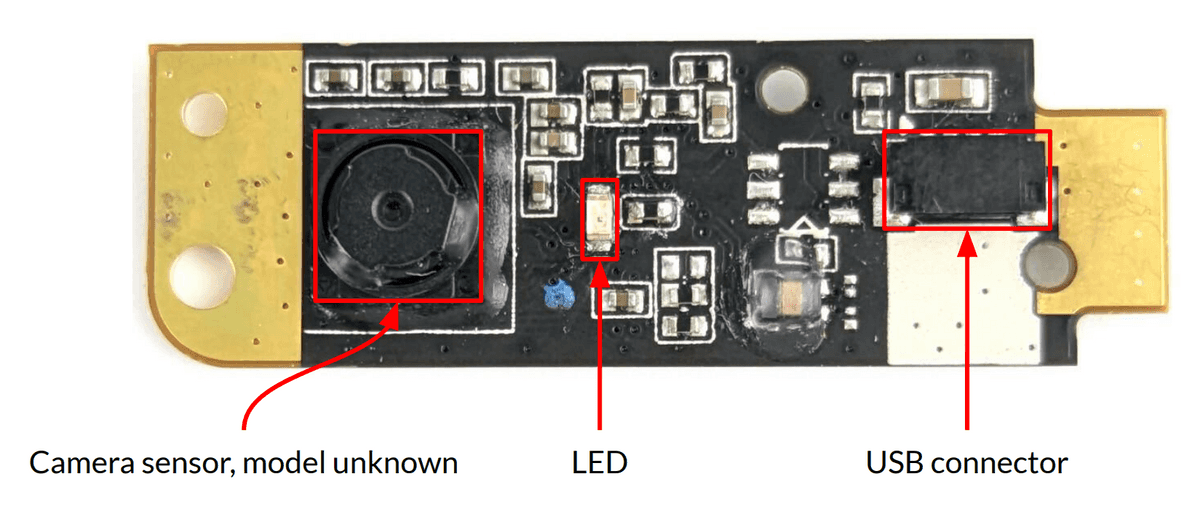
In addition, although Konovalov demonstrated the technique on a ThinkPad X230, many laptops have webcams connected via USB, just like the ThinkPad X230, and the firmware can be rewritten, so it is possible that the same technique could be applied to many laptops.
The specific methods are as follows:
The ThinkPad x230 uses a Ricoh R5U8710 USB camera controller, and the GPIO B1 pin of the R5U8710 is connected to an LED that indicates whether the webcam is in use. The GPIO B port is mapped to the 0x80 address in the XDATA memory of the R5U8710, and by rewriting the 0x80 address, the LED state can be changed regardless of the webcam state.
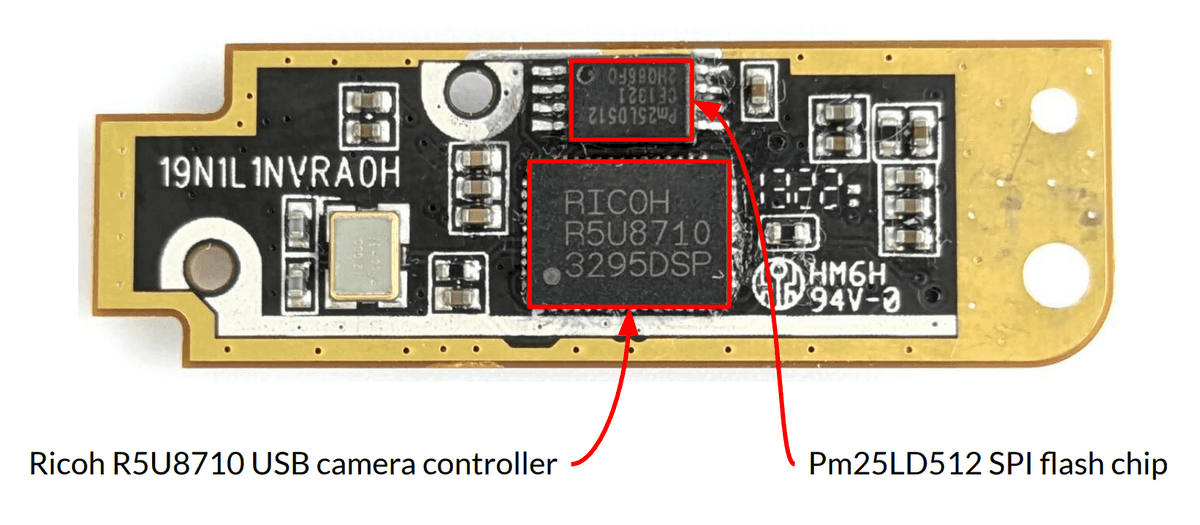
Konovalov wrote custom firmware into the SPI chip on the webcam board, allowing him to rewrite data at any address in the XDATA memory space. By rewriting the data at address 0x80, he could control the LED regardless of whether the camera was in use or not.
The code used by Konovalov was published on GitHub, but it came with a warning: 'Use with caution as it may cause your webcam to stop working.'
Related Posts: