How did I crack a ZIP file that I couldn't open because I lost the password after 30 years?

Cloudflare CTO John Graham-Cumming has successfully cracked and decrypted a 30-year-old ZIP file, and has written a blog post about how he did it.
John Graham-Cumming's blog: Cracking an old ZIP file to help open source the ANC's 'Operation Vula' secret crypto code
Tim Jenkin, an anti-apartheid activist in South Africa, once built an encrypted communications system for the African National Congress (ANC) . The source code for the system was stored in a password-protected ZIP file, but Jenkin forgot the password.
'I thought I would never forget the password, but when I tried to decode it a few years later, I couldn't remember it,' Jenkins said. 'If I can decode the source code for the encrypted communications system, I would like to make it open source. I have tried several times to decode the code, but so far I have not been successful,' he said, asking Cloudflare CTO Cummings to decode it.
The two files in question are 'ALLBAS.ZIP' and 'CODMAY93.ZIP'. Both were created with an early version of PKZIP . Fortunately, the encryption method used in early versions of PKZIP, ZipCrypt, is known to be vulnerable to known plaintext attacks.
A known plaintext attack is a method of determining the password that protects the entire ZIP file by comparing the encrypted data with the pre-encryption data, if any part of the contents of the encrypted ZIP file is known. To perform a known plaintext attack, Cumming decided to predict which part of the data in the ZIP file contains known data.
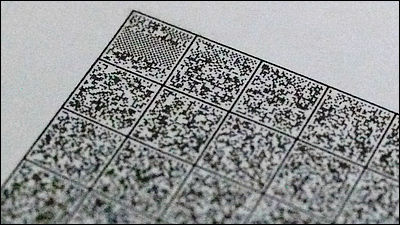
The contents of the ZIP file look like this. Some of the '.BAS' files contained in the file were in unencrypted form, so Cumming tried to use the data to perform a known plaintext attack, but the data was different from the contents of the ZIP file and the decryption failed.
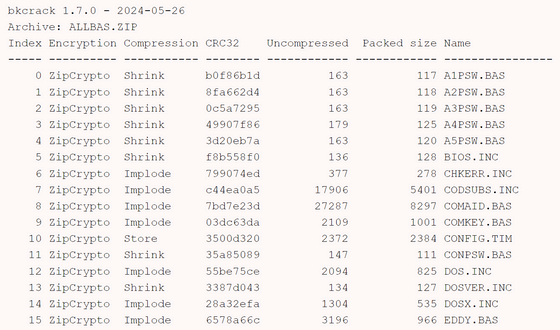
Next, Cumming focused on uncompressed 'Store' data. Files that are already compressed or binary files that are not worth compressing, such as ZIP files and executable files, are stored in the ZIP file in the Store state, and such data is easy to handle when predicting the contents and location of the data because it is not compressed.
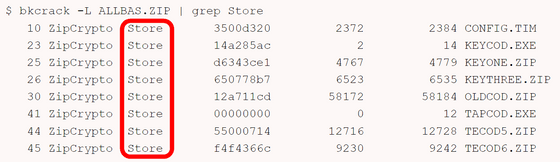
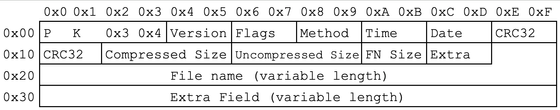
Fortunately, Jenkins had saved a ZIP file called 'OLDCOD.ZIP' contained in the encrypted ZIP file 'ALLBAS.ZIP' in another location, and it was discovered that the first file in OLDCOD.ZIP was named 'COMKEY.BAS'. Based on the ZIP header structure shown below, Cumming predicted the location of the file name that would match 'COMKEY.BAS' and attempted to decrypt it using
About 23 minutes after the start of the decryption, the key for the ALLBAS.ZIP file was generated and successfully decrypted. The other encrypted ZIP file, CODMAY93.ZIP, was also decrypted with the same key. Cumming said, 'If you need to do something similar, it's worth taking the time to think about the plaintext.'
The encrypted communications system used by the ANC around 1990, which was stored in this ZIP file, is available in a GitHub repository by Tim Jenkin .
Related Posts: