Apple releases documents on 'Private Cloud Compute (PCC)' that supports cloud processing of Apple Intelligence, and also sets new reward of up to 150 million yen
On October 24, 2024 local time,
Blog - Security research on Private Cloud Compute - Apple Security Research
https://security.apple.com/blog/pcc-security-research/
Apple Shares Private Cloud Compute Virtual Research Environment, Provides Bounties for Vulnerabilities - MacRumors
https://www.macrumors.com/2024/10/24/apple-private-cloud-compute-security-info/
Apple creates Private Cloud Compute VM to let researchers find bugs
https://www.bleepingcomputer.com/news/apple/apple-creates-private-cloud-compute-vm-to-let-researchers-find-bugs/
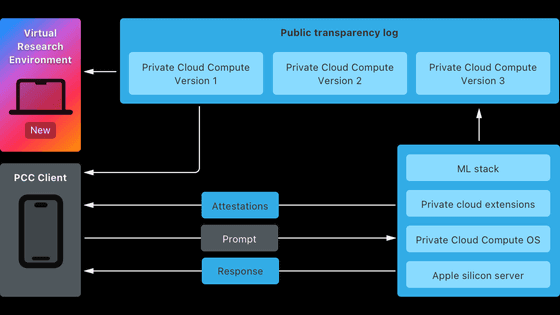
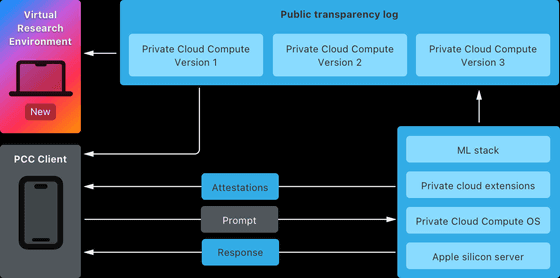
PCC brings the industry-leading device security model to the cloud, delivering groundbreaking privacy and security protections while meeting the computationally intensive demands of Apple Intelligence. PCC has taken the extra step of enabling security and privacy researchers to examine and verify its end-to-end security and privacy promises, and as such, Apple has provided third-party auditors and select security researchers early access to resources that enable them to examine and verify PCC.
On October 24, 2024 local time, Apple made its PCC resources available to the public, enabling security and privacy researchers and anyone with an interested and technical curiosity to learn about PCC and independently examine Apple's system.
Resources related to PCC are published on the following pages, and are divided into three categories: 'Security Guide,' 'Virtual Research Environment,' and 'Source Code.'
Private Cloud Compute Security Guide | Documentation
https://security.apple.com/documentation/private-cloud-compute/
◆Security Guide
The Security Guide was created to help you understand how PCC is architected and how it meets each of its core requirements. It provides comprehensive technical details about each component of PCC and how they work together to deliver breakthrough levels of privacy for AI processing in the cloud.
The Security Guide covers a variety of topics, including how PCC attestations are built on an immutable foundation of hardware-implemented capabilities, how PCC requests are authenticated and routed to provide non-targetability, how we can technically ensure that software running in Apple data centers can be inspected, and how the privacy and security properties of PCC are maintained under various attack scenarios.
◆Virtual Research Environment
Additionally, Apple has created a Virtual Research Environment (VRE) for its platforms, a set of tools that allows developers to run their own PCC security analysis directly from their Macs, to gain a deeper understanding of the platform's security capabilities.
VRE runs PCC node software in a virtual machine with only minor modifications. User space software runs exactly like PCC node, and the boot process and kernel are adapted for virtualization. VRE includes a virtual Secure Enclave Processor (SEP), which for the first time enables security research on this component, and allows inference using the paravirtualized graphics support built into macOS.
With VRE you can:
- PCC software release list and inspection
- Check for consistency in transparency logs
・Download the binaries for each release
・Run the release in a virtualized environment
・Run inference on the demo model
Modify and debug PCC software to allow deeper investigation
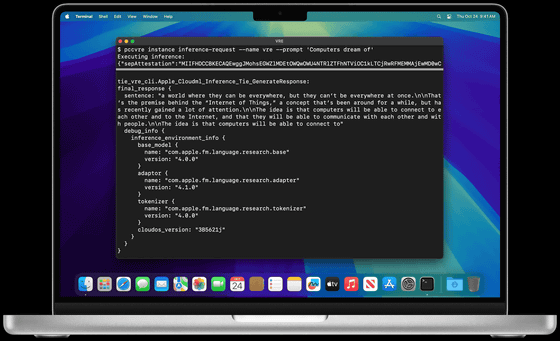
VRE is available in the macOS Sequoia 15.1 Developer Preview and requires a Mac with Apple silicon and at least 16GB of unified memory.
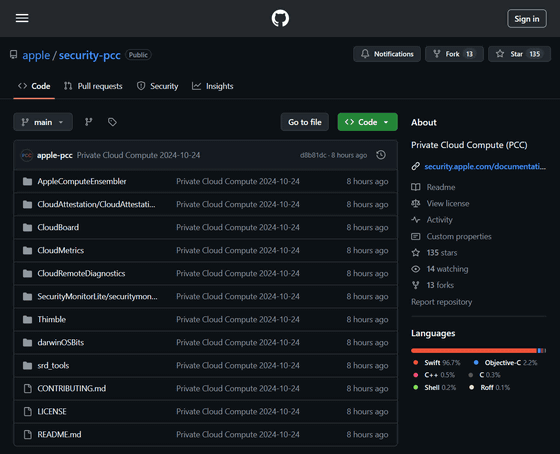
◆PCC source code
The source code for certain key components of PCC that help implement security and privacy requirements has also been made publicly available, and is provided under a limited use license agreement to enable more detailed analysis of PCC to be performed.
The released source code covers the following areas:
CloudAttestation Project : Project responsible for building and verifying the certificates of PCC nodes
Thimble Project : A project that runs on user devices and uses CloudAttestation to enforce verifiable transparency. Includes the PCC daemon.
splunkloggingd daemon : Filters logs output from PCC nodes to prevent accidental data leakage.
The srd_tools project contains the VRE tools that can be used to understand how the VRE enables the execution of PCC code.
The source code for PCC is available on GitHub.
GitHub - apple/security-pcc: Private Cloud Compute (PCC)
https://github.com/apple/security-pcc
In conjunction with making the PCC resources publicly available, Apple also announced that it is expanding its security bounty program to include the PCC, and will offer significant rewards for reporting security and privacy claims. The PCC-related security bounty program will offer rewards of up to $1 million.
You can also submit security and privacy reports at the following page:
Bounty - Apple Security Research
https://security.apple.com/bounty
Related Posts:
in Software, Smartphone, Security, Posted by logu_ii