The vulnerability sent to Apple's vulnerability bounty program turned out to be unfixed for half a year, the discoverer disclosed a zero-day vulnerability as'disappointed'
Many companies, including
Disclosure: Another macOS privacy protections bypass
https://lapcatsoftware.com/articles/disclosure2.html
The vulnerability that Johnson reported to Apple was about the security framework 'Transparency Consent and Control (TCC)' installed in macOS, and it was discovered in September 2019. TCC is used in macOS Mojave and later macOS, which has enhanced privacy protection functions, and enables users to manage access privileges to data.
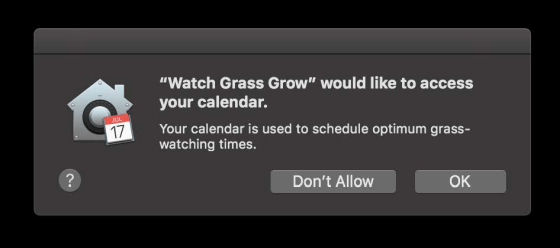
The vulnerability discovered by Mr. Johnson is due to TCC's application verification flow. With TCC, apps that are allowed to access the data are recorded in a database file named 'TCC.db', but the contents are based on the bundle identifier rather than the file path. Johnson said the vulnerabilities were only due to the superficial checking of code signatures. This application verification flow mechanism allows an attacker to access data even with a duplicate application that is a modification of a legitimate application.
For example, for access to '~/Library/Safari', only Safari and Finder have access permission by default. However, if you use the vulnerability discovered by Mr. Johnson, a duplicate version of Safari modified by a malicious third party can also access '~/Library/Safari'. Since Safari also grants access to the JavaScript that is executed on the application, the range that can be exploited will be large.

Mr. Johnson reported this vulnerability to Apple at the same time as the program started because Apple launched ' Apple Security Bounty ', which is a program to pay a bounty for bug reports on December 19, 2019. In January 2020, Apple replied, 'We plan to address this issue in April 2020,' but until June 2020, the vulnerability was not fixed. ``In this case, we're well beyond the'90 days', which is a typical time between reporting a problem to a vendor and disclosing a vulnerability, so wait for years for the bounty,'' he said. I'm not interested in,' and decided to disclose the vulnerability. 'The user has the right to know that the system that relies on privacy protection isn't really working,' he said. 'I was disappointed with Apple Security Bounty.'
The vulnerability is present in beta versions of macOS Mojave, Catalina , and Big Sur . Since OSs prior to High Sierra did not have such a privacy protection function in the first place, whether it is necessary to worry about this vulnerability depends on 'how you feel the privacy protection function of macOS' Johnson Mr. “The best security is to choose the software to install and be careful not to install the malware from scratch,” said Johnson.
Related Posts: