Cloudflare publishes analysis showing that 20% of the world's TCP connections are not normal

Cloudflare processes 60 million HTTP requests per second, of which about 70% are TCP connections and about 30% are UDP/QUIC connections. Of these, only about 80% of data exchanges are actually completed after a TCP connection is started. Cloudflare has summarized its analysis of why TCP connections are dropped.
Bringing insights into TCP resets and timeouts to Cloudflare Radar
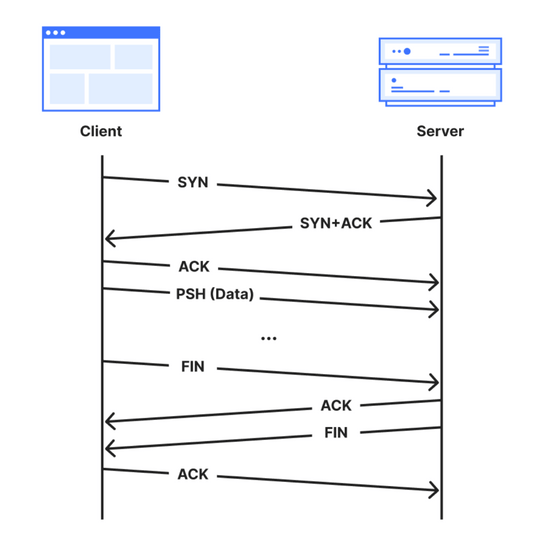
The interaction between a client and a server in a TCP connection proceeds as shown in the diagram below. First, the client starts the handshake by sending a packet with the 'SYN' flag, the server responds with 'SYN + ACK', and then the client sends 'ACK', completing the handshake and allowing data to be sent. In addition, when terminating the connection, a FIN handshake is performed in which both parties send 'FIN' and 'ACK' to each other.
TCP connections that have been started are often interrupted for various reasons, such as network errors and malicious attacks, and Cloudflare is trying to improve the reliability of its network by monitoring the status of connections and understanding the scale and reason for the anomaly. In the analysis, an important clue is 'at what point in the connection process the anomaly occurred,' so Cloudflare classified the connection data where an anomaly occurred into the following four types.
・Post SYN
This is the case when the server receives a SYN packet from the client, then sends 'SYN + ACK', but the client does not send an 'ACK'. Packets are often spoofed, and the location information is unreliable.
・Post ACK
This is the case when the handshake is complete and the connection is established, but no data is sent and the connection is reset or times out.
・Post PSH
This is the case when the initial data is received only once, but then the connection is reset or times out. The PSH flag indicates that the TCP packet contains data for the application.
Later
This is the case when data was successfully received multiple times, but a reset or timeout occurred within 10 attempts.
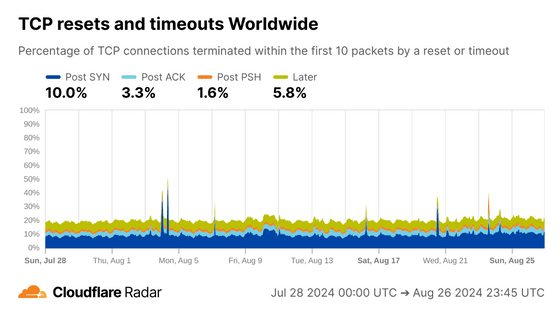
The graph below shows the status of TCP connections around the world. On average, about 20% of TCP connections are reset or timed out before receiving 10 data packets from the client. If you want to check the data for a new date, you can view it on
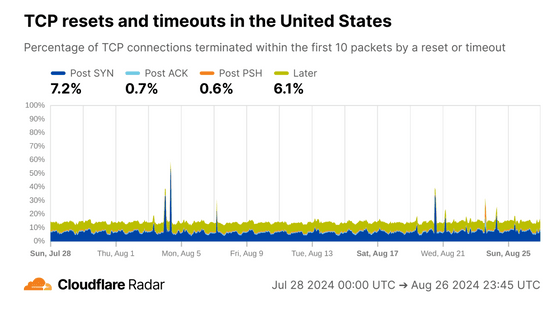
The data for the US looks like this. The high proportion of Post SYNs is due to network scans, while Later corresponds to cases where a tab is opened in a browser but then immediately closed.
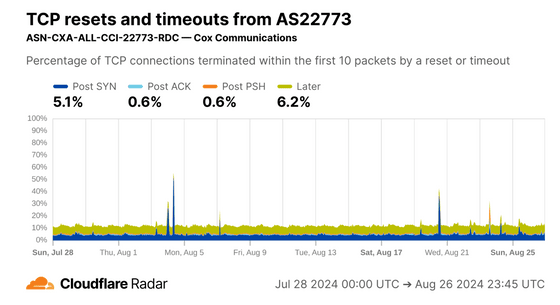
When looking only at residential ISPs in the United States, the Post SYN ratio has declined slightly.
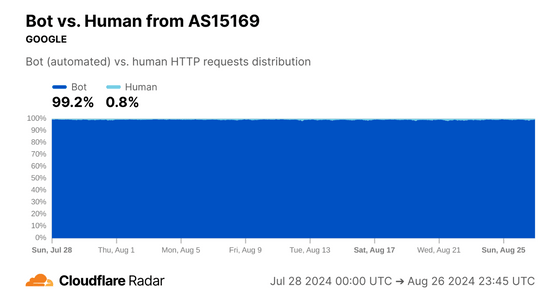
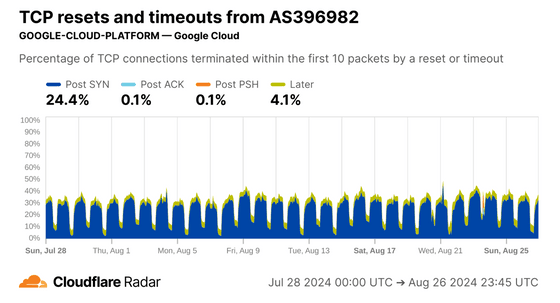
On the other hand, the AS used by Google had almost no disconnections at Later, suggesting that there were fewer human connections.
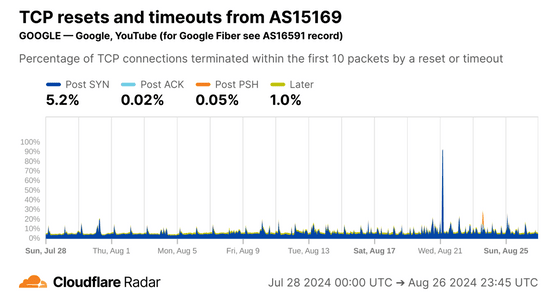
In fact, Cloudflare's bot detection system identified 99.2% of connections as being from bots, which is consistent with the analysis above.
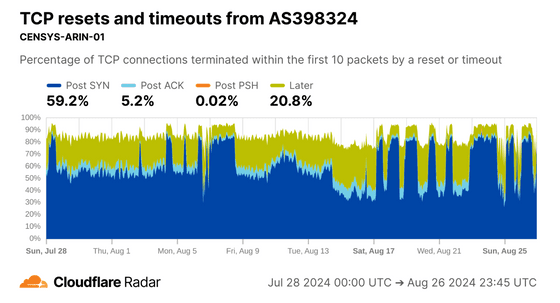
The Post SYN rate skyrockets in ASs used by Internet scanning companies.
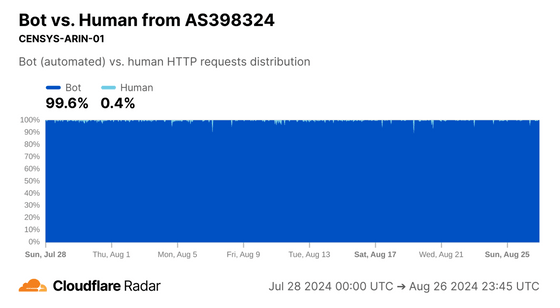
Here too, the bot detection system determined that most of the connections were made by bots.
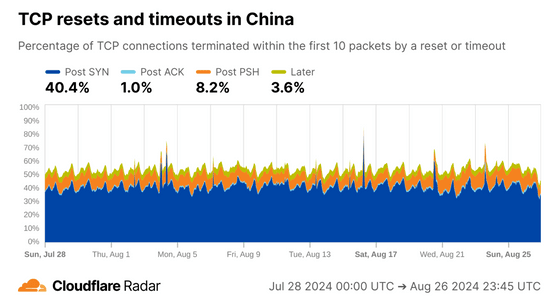
China operates a censorship system called the Great Firewall, which forcibly drops connections to prohibited addresses, causing the Post SYN rate to skyrocket.
The UK data shows a distinct pattern of a daily increase in Post SYN values at 6pm.
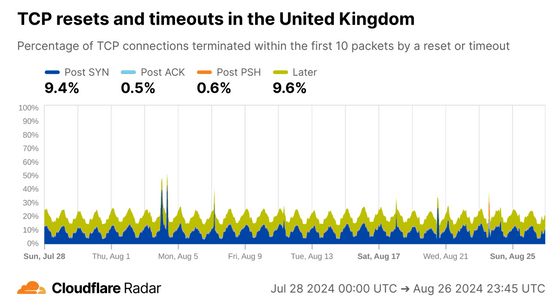
Cloudflare's investigation revealed that this cycle was a scan of all IP addresses by
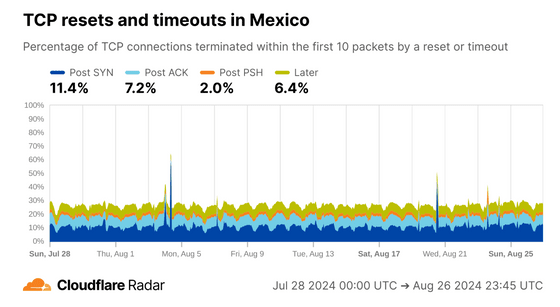
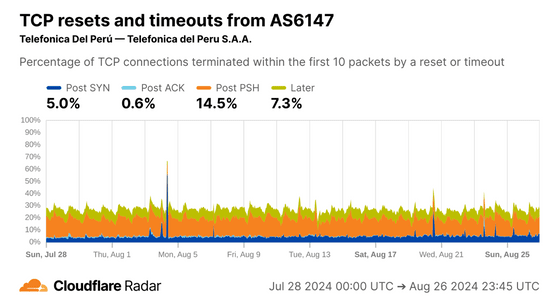
Mexico has higher Post ACK and Post PSH numbers than the global average, and according to Cloudflare, Post ACK and Post PSH anomalies are often related to connection tampering.
In the Mexico issue, the AS in the figure below has a high Post ACK value. According to Cloudflare's analysis, when mobile phone carriers apply
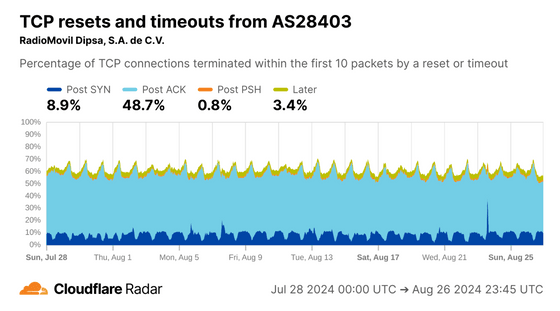
The same trend was observed in a Peruvian subsidiary of the same telecommunications company, suggesting that it is operating under the same rules.
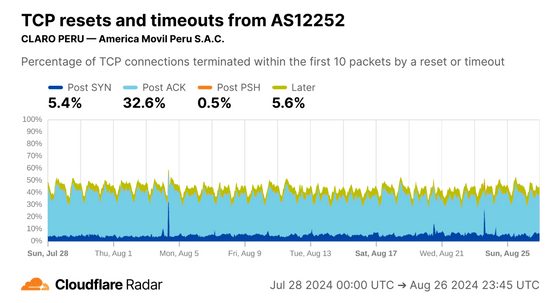
Even if the same rules are applied, depending on the method used, a disconnection may occur post-PSH.
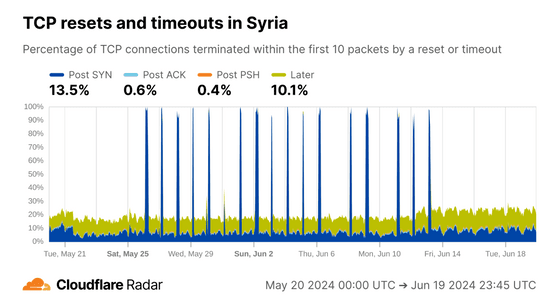
On the other hand, in Algeria, where the internet was also cut off during the test, the proportion of Post ACKs increased, suggesting that only certain connections were targeted for disconnection.
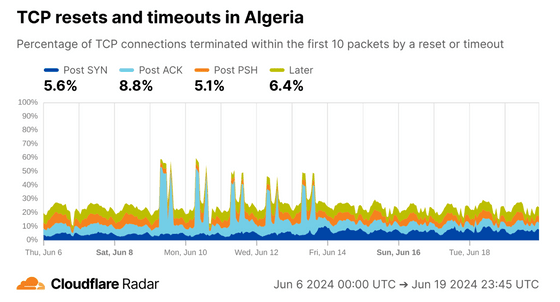
This country and AS data is freely available to view on Cloudflare Radar , so if you're interested, check it out.
Related Posts:
in Web Service, Posted by log1d_ts