What was the result of analyzing the code that emerged from hacking an electric toothbrush?
Some commercially available electric toothbrushes have a feature that recognizes when the brush head is attached and notifies you when it's time to replace it. Engineer
Here is the full Philips Sonicare Head NFC Password Calculation ????
— atc1441 (@atc1441) June 9, 2023
How I got there you can find in this Thread.
1/N pic.twitter.com/ooy1v2mBEe
Hacking the Philips Sonicare NFC Password - YouTube
The Philips Sonicare electric toothbrush has a function that communicates between the brush head and the handle, and notifies the user when it is time to replace the head when it gets old. This function is password protected, and it is possible to unlock the function and freely change the brush head usage time using special equipment or software, but Christopher is trying to realize this by analyzing the algorithm for calculating the password and unlocking the function change.
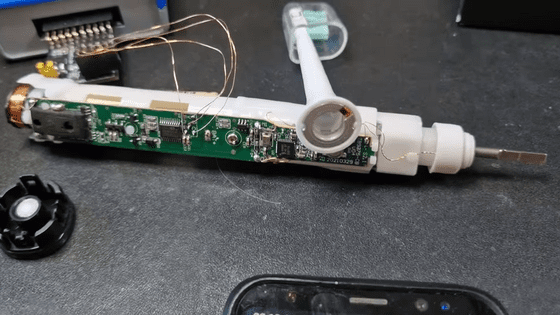
To hack the electric toothbrush, Christopher bought an NFC-enabled Sonicare for 40 euros (about 6,700 yen) and immediately began disassembling it.
Since lately the RF sniffing of the NFC Password was blogged by Cyrill Künzi https://t.co/xHZNb7yScJ I couldn't stop thinking on how to crack it.
— atc1441 (@atc1441) June 9, 2023
So this afternoon I bought the cheapest available Toothbrush with the NFC feature (40€) and opened it up.
Quite simple to open! pic.twitter.com/gaOO7LVIMG
Examining the board reveals that it is equipped with an NFC reader 'MFRC630', a MindMotion 'MM32F001 Cortex M0' SoC, 16KB of flash memory, 2KB of RAM, and the debug pins are clearly labeled.
Inside this version we can find an
— atc1441 (@atc1441) June 9, 2023
NXP NFC Reader MFRC630
and a MindMotion MM32F001 Cortex M0 SoC
16Kb Flash and 2Kb RAM
Plus nicely labeled Debug Pins...
Ok how much on the bet that it will be locked... but lets see... pic.twitter.com/9q9YDDcFSO
When I connected the board to a PC and the flasher, the information on the SoC, RAM, etc. was displayed without any problems. In addition, a mysterious code '28 06 00 20 C9 00 00 08' was also detected.
Very unusual, after hitting connect I was greeted by a happily connected SWD Flasher which was able to read the full flash without problems ????
— atc1441 (@atc1441) June 9, 2023
wonder who slept there at Philips... pic.twitter.com/SSCmYtAinV
Using the program analysis tool IDA, the code was found to be the NFC password used on the brush head and the electric toothbrush itself. 'The code is in the user identifier in the NFC tag, and we were able to easily analyze it by looking at the manufacturing string printed on the brush head,' Christopher said.
After an exiting reverse engineering session in IDA everything came together and the NFC Password calculation was found.
— atc1441 (@atc1441) June 9, 2023
And as shown already its a very simple CRC Calculation over the NFC Tag UID and the Manufacturing String that is in NFC Tag and also printed on the Brush Head pic.twitter.com/lmCkpISgTZ
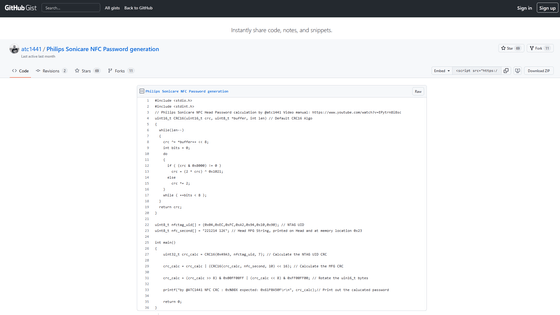
Christopher has published the NFC password he discovered on GitHub.
Philips Sonicare NFC Password generation · GitHub
https://gist.github.com/atc1441/41af75048e4c22af1f5f0d4c1d94bb56
Christopher revealed that he was inspired to try hacking a toothbrush after fellow engineer Cyril Kunj hacked a Philips Sonicare electric toothbrush.
Hacking the brush head of an electric toothbrush can rewrite the usage time - GIGAZINE

Related Posts:






