Confidential documents from Chinese government hacker company I-Soon uploaded to GitHub, experts say ``the most detailed and important leak ever''

On February 16, 2024, a large amount of data purported to belong to a private hacking company called I-Soon in China was uploaded to GitHub. Internal documents show that the company engaged in hacking and intelligence gathering across a wide range of regions, both domestically and internationally, and security experts believe this is an important part of understanding China's cyber espionage efforts. I think it's a document.
Unmasking I-Soon | The Leak That Revealed China's Cyber Operations - SentinelOne
Chinese hacking documents offer glimpse into state surveillance | AP News
https://apnews.com/article/china-cybersecurity-leak-document-dump-spying-aac38c75f268b72910a94881ccbb77cb
Shadow Ops Exposed: Inside the Leak of China's i-Soon Cyber Espionage Empire - SOCRadar® Cyber Intelligence Inc.
https://socradar.io/shadow-ops-exposed-inside-the-leak-of-chinas-i-soon-cyber-espionage-empire/
Chinese firm's leaked files show vast international hacking effort - The Washington Post
https://www.washingtonpost.com/world/2024/02/21/china-hacking-leak-documents-isoon/
I-Soon is officially a security company based in Sichuan Province, China, but in reality it is said to be an Advanced Persistent Threat (APT) group that operates hacking services based in Shanghai. It is known to do business with many Chinese government agencies, including the People's Liberation Army and the Ministry of State Security, and its official website lists more than 50 local public security authorities as customers, including the Ministry of Public Security, a police organization. However, the official website went down after the leak was discovered.

The leak occurred on February 16, 2024, when a Taiwanese researcher discovered a large amount of I-Soon's confidential data on GitHub and reported it on SNS. The account that uploaded the data to GitHub was an account registered with the email address '[email protected]' on January 15, about one month before the leak.
Please note that the
The details of the leak are unknown, but two I-Soon employees contacted by The Associated Press on condition of anonymity have confirmed the contents, as well as a senior analyst at Mandiant Intelligence, a cybersecurity company owned by Google Cloud. One John Hultquist said: 'There is good reason to believe that this is genuine data leaked from contractors supporting China's domestic and international cyber espionage operations.'
What was leaked this time was a total of approximately 190MB of internal data, including more than 570 document files, images, and chat logs, as well as records of WeChat conversations between I-SOON employees and customers, and records of conversations between I-SOON employees and customers. This included a list of employees, contracts, marketing materials, product manuals, and more.
The targets of I-Soon's espionage activities are mainly in areas with active anti-establishment movements within China, such as Hong Kong and the Uighur Autonomous Region, but the leaked materials also target organizations around the world, including Asia, the Middle East, and Europe. It is written.
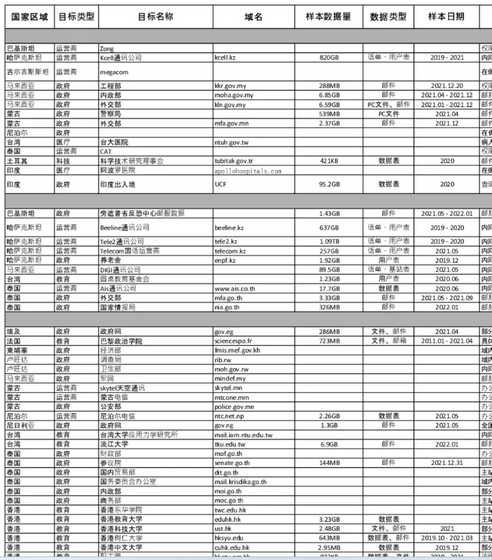
According to The Washington Post, some of the data showed that I-Soon provided customers with 459GB of geographic data about Taiwan's transportation network. Such data could be useful in China's invasion of Taiwan, national security experts say.
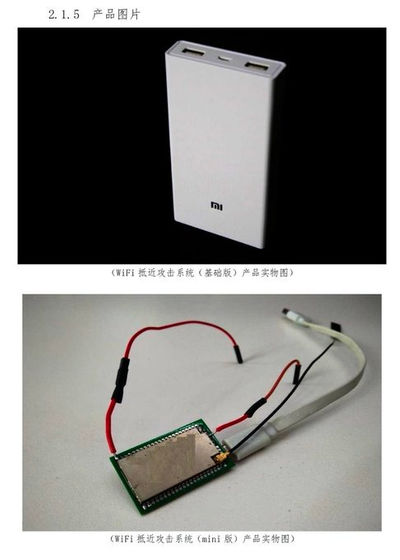
The technical documents also included photos of custom-made eavesdropping devices.
In addition, the leaked data includes conversation records showing that I-Soon was in contact with an APT group called 'APT 41,' complaints from employees complaining about low pay, and reports of coronavirus infection. It is said that it included exchanges regarding the impact it had on the company's management.
John Condra, an analyst at cybersecurity firm Recorded Future, said, ``This breach is related to a company suspected of providing cyber espionage and targeted intrusion services for Chinese security services. This is the most important leak ever.'
Related Posts:
in Security, Posted by log1l_ks