A super cheap device is created that instantly captures the BitLocker recovery key

Higher editions of Windows such as Windows 10 Pro and Windows 11 Pro are equipped with the storage encryption function ``
Breaking Bitlocker - Bypassing the Windows Disk Encryption - YouTube
◆Example of stealing BitLocker recovery key
The following is a Lenovo notebook PC with storage encryption using BitLocker.

Mr. stacksmashing starts removing the cover of the notebook PC.

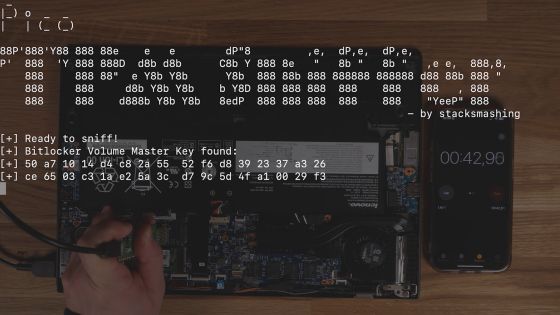
After removing the cover, place the recovery key capture device against the terminal on the board.

When I touched the device to the terminal, the recovery key was read instantly. It took only 42.9 seconds from the time they started disassembling the laptop to the time they retrieved the recovery key.
◆Mechanism to capture the recovery key
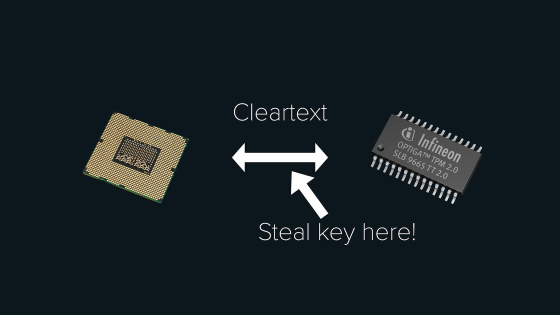
The Lenovo laptop that stacksmashing tried to steal the recovery key from was equipped with a security chip called a TPM .

The BitLocker recovery key is stored in an encrypted state in the TPM. The TPM checks the health of the hardware when the system starts, decrypts the recovery key, and sends it to the CPU, but communication between the TPM and the CPU is performed without encryption. Mr. stacksmashing noticed that the communication between the TPM and the CPU was not encrypted, and devised a method to capture the recovery key by analyzing the communication passing through the LPC bus.
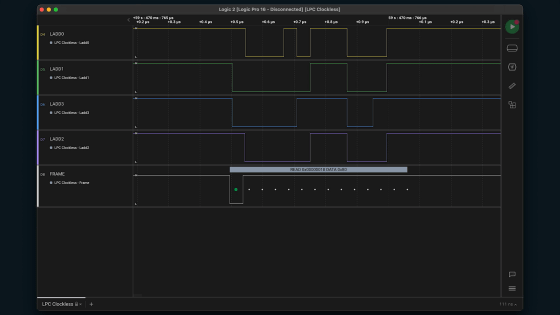
There was a connector with nothing mounted on the board of the Lenovo notebook PC used for the test, so I connected an electrode to the connector.

By analyzing the content of the communication, we succeeded in capturing the recovery key.
The above method requires operations such as ``connecting the electrode to the connector'' and ``analyzing the communication content and deriving the recovery key.'' To simplify these operations, stacksmashing designed a device equipped with a Raspberry Pi Pico and a connector to process the communication content.
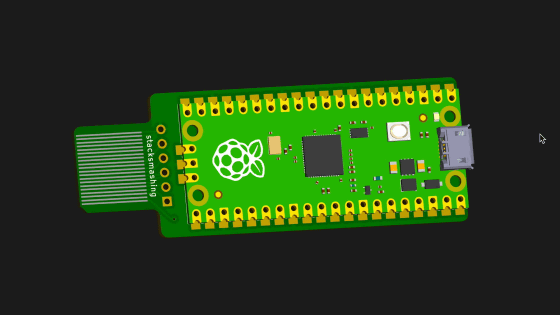
The completed device looks like this. The name of the device is 'Pico TPM Sniffer' and the total cost is about 10 dollars (about 1500 yen).

Raspberry Pi Pico is installed on the other side.

It also includes a connector, which eliminates the hassle of carefully connecting electrodes.

By using Pico TPM Sniffer, they were able to capture the recovery key in 42.9 seconds.
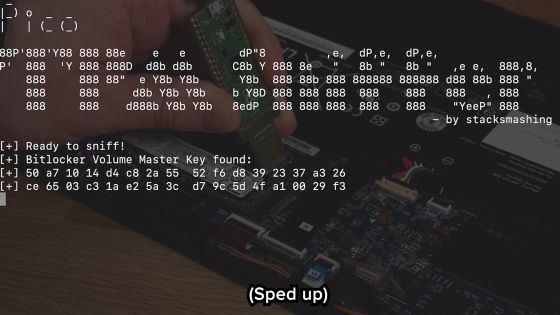
Once you have the recovery key, you can view the contents of the storage by simply removing the storage, connecting it to another machine, and decrypting it using the recovery key.

stacksmashing actually succeeded in decrypting BitLocker encrypted storage.
In addition, many recent CPUs have a built-in TPM, and the number of notebook PCs equipped with a dedicated TPM chip, such as the Lenovo notebook PC used in this test, is decreasing. However, for some models, it is still possible to obtain the recovery key using the same method.
Mr. stacksmashing has published the blueprint of Pico TPM Sniffer at the following link.
GitHub - stacksmashing/pico-tpmsniffer: A simple, very experimental TPM sniffer for LPC bus
https://github.com/stacksmashing/pico-tpmsniffer
Related Posts: