An attack method ``BrutePrint'' that can execute fingerprint authentication of smartphones unlimited times and mechanically will be developed, the material cost is only 2000 yen, and Android is excellently effective, but iPhone can defend

Researchers from Tencent and Zhejiang University have developed a system ' BrutePrint ' that breaks through smartphone fingerprint authentication. The material cost of the device used in BrutePrint is $ 15 (about 2000 yen), and like a password brute force attack (brute force attack), you can try fingerprint authentication mechanically and unlimited times to break through fingerprint authentication.
BrutePrint: Expose Smartphone Fingerprint Authentication to Brute-force Attack
BrutePrint breaks through fingerprint authentication by attaching a ``device with a huge amount of fingerprint information'' to a smartphone and ``sending a huge amount of fingerprint images in order while misrecognising that the fingerprint has been scanned''. In a typical fingerprint authentication system, authentication cannot be performed if authentication fails multiple times, but the research team also built a mechanism that allows fingerprint authentication to be performed an unlimited number of times, realizing a brute force attack. Details of the various technologies included in BrutePrint are as follows.
◆Device
The device used for BrutePrint is divided into an 'operating board' and an 'attack board', and it is possible to make the smartphone's fingerprint authentication sensor mistakenly recognize 'finger detected' and 'fingerprint scanned'. The device consists of easy-to-obtain parts such as an SD card that stores fingerprint images, a microcontroller ' STM32F412 ', an analog switch ' RS2117 ', etc. The total price of each part is about 15 dollars (about 2000 yen).
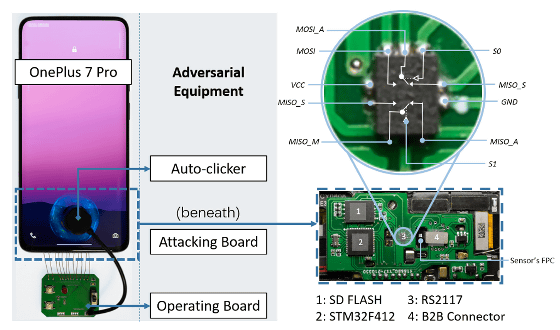
◆Fingerprint collection
The research team collected ``
◆ Fingerprint optimization
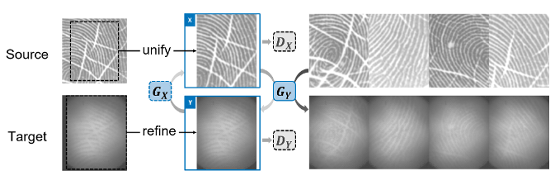
The fingerprints registered in the fingerprint database are clear, but the image of the fingerprint read by the fingerprint sensor is blurred. Therefore, BrutePrint emulates the reading performance of the fingerprint sensor and converts a 'clear image' into a 'blurry image read by the fingerprint sensor'.
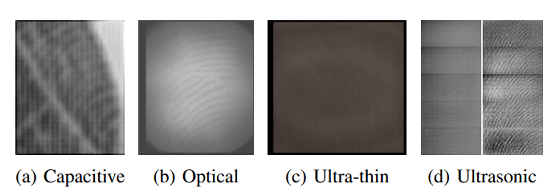
There are `` capacitive method '', `` optical method '', `` ultrasonic method '', etc. for the reading method of the fingerprint sensor, and the reading method adopted by the smartphone is different. BrutePrint is designed to send a processed fingerprint image according to the attack target's reading method.
◆Breaking through the number limit
If the smartphone fingerprint authentication fails multiple times, the authentication will be terminated, and you will be able to unlock it only with an authentication method other than fingerprint authentication, such as a passcode. The research team succeeded in changing the signal 'fingerprint authentication failed' to 'fingerprint authentication was canceled in the middle' by exploiting the vulnerability of the smartphone. This makes it possible to attempt fingerprint authentication an unlimited number of times.
◆ Verification result
The research team is 'Xiaomi Mi 11 Ultra' 'Vivo X60 Pro' 'OnePlus 7 Pro' 'OPPO Reno Ace' 'Samsung Galaxy S10 +' 'OnePlus 5T' 'HUAWEI Mate30 Pro 5G' 'HUAWEI P40' 'Apple iPhone SE' 'Apple We verified BrutePrint's ability to break through fingerprint authentication for iPhone 7. As a result, smartphones other than 'Apple iPhone SE' and 'Apple iPhone 7' succeeded in breaking through by performing fingerprint authentication unlimited times. On the other hand, in 'Apple iPhone SE' and 'Apple iPhone 7', authentication was interrupted after 15 attempts despite exploiting the vulnerability.
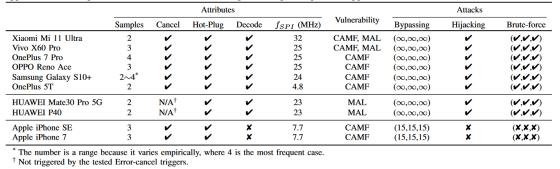
According to the research team, even if the information on the owner of the smartphone is unknown, BrutePrint can break through fingerprint authentication in as little as 40 minutes. In addition, password authentication requires an 'exact match', but fingerprint authentication can break through authentication if it exceeds a set 'threshold'. Shortening is also possible.
Related Posts: