``PrintListener'', a technology that reproduces fingerprint information from swipe sound, has appeared, and authentication using partial fingerprints can exceed up to 28%

Fingerprint authentication, which is used to unlock smartphones and make bank transfers, is expected to have a market value of 100 billion yen by 2032. As technology becomes more widespread, some companies are starting to take precautions, such as not showing detailed photos of their hands to avoid fingerprint theft. It has become clear that fingerprint information can be reproduced from the fricative sounds generated.
PrintListener: Uncovering the Vulnerability of Fingerprint Authentication via the Finger Friction Sound
(PDF file)

Your fingerprints can be recreated from the sounds made when you swipe on a touchscreen — Chinese and US researchers show new side channel can reproduce fingerprints to enable attacks | Tom's Hardware
This study was a collaboration between researchers from Huazhong University of Science and Technology, Wuhan University, Tsinghua University, and the University of Colorado Denver. Researchers have dubbed the side-channel attack PrintListener .
The figure below shows how the 'PrintListener' attack is carried out. First, when a user performs a swipe operation on a smartphone, the sound is detected and analyzed to reproduce fingerprint information. The resulting fingerprint can then be used to gain access control, make payments, and extract personal information.
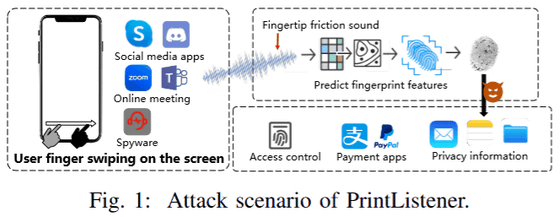
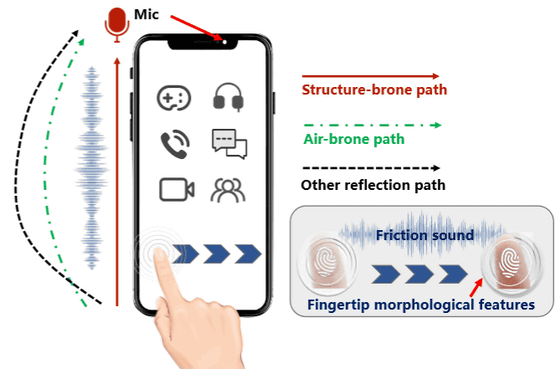
When you operate your smartphone, the sound travels through the device itself and is picked up by the microphone or transmitted as audible sound.
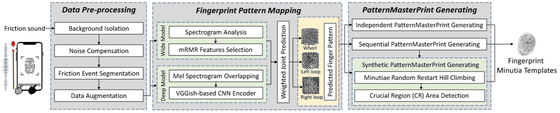
The captured sounds are first preprocessed to remove noise and background sounds and extract only the sounds generated by the swipe motion. Next, the fingerprint pattern is detected after performing spectrum analysis. Finding a fingerprint pattern is not the end; a 'pattern master fingerprint' is generated based on this information.
In biometric authentication, it is important to determine how accurately the person in question can be detected and approved, and how well attempts by others can be detected and rejected. According to researchers, using pattern master fingerprints created by PrintListener attacks, it is possible to break through a security setting with a false acceptance rate (FAR) of 0.01% by up to 27.9% for partial fingerprints and up to 9.3% for complete fingerprints. It is said that it was.
Related Posts:
in Security, Posted by logc_nt