What kind of technology is QR code and what are the dangers?
The COVID-19 pandemic that hit the world in 2020 has led to the rapid adoption of contactless technologies such as touch payments. Scott Ruotie, an assistant professor in the Department of Computer Science at the University of Tennessee and an expert in encryption protocols, explains
How QR codes work and what makes them dangerous – a computer scientist explains
https://theconversation.com/how-qr-codes-work-and-what-makes-them-dangerous-a-computer-scientist-explains-177217
QR codes are a technology developed in 1994 by DENSO , an auto parts manufacturer belonging to the Toyota Group. At the time, DENSO's manufacturing plants managed various parts with barcodes, but in response to complaints from the field that 'it was time-consuming to have to read multiple barcodes just to do one task,' Masahiro Hara of the development department developed a QR code that 'carries information vertically and horizontally,' as opposed to barcodes, which only carry information horizontally. Based on the philosophy of 'spreading it first,' the QR code was made available as open source, and it quickly spread beyond the boundaries of the automotive industry.
History of QRcode - YouTube
According to Assistant Professor Ruoti, a QR code is made up of four elements: 1) data, 2) a marker for positioning, 3) white space, and 4) a logo.

QR code data is recorded in a pattern of black and white square 'cells,' and roughly speaking, it stores information such as URLs in a binary system where white is 1 and black is 0. The cell capacity that can be recorded in one QR code ranges from 21 x 21 cells to 177 x 177 cells, and the maximum data capacity is 7,089 numbers, 4,296 alphanumeric characters, and 1,817 kanji characters. As mentioned above, most cells are black and white squares, but Assistant Professor Ruoti says, 'Actually, there are no specifications for color or shape.'
The positioning markers are the squares in the upper left, upper right, and lower left corners of the QR code, which allow devices such as smartphone cameras to correctly determine the orientation of the QR code. The blank areas allow computers to correctly recognize the recording range of the QR code. The logo is a space for writing company information, and it is okay to have it or not.
Assistant Professor Ruotie points out that one of the features of logo-related QR codes is their 'error correction function.' The error correction function allows the code itself to recover data even if part of the QR code is unreadable due to damage or dirt, and at the highest setting, data can be restored even if 30% of the code is unreadable. This error correction function means that QR codes can be used without problems even if part of them is obscured by a logo.
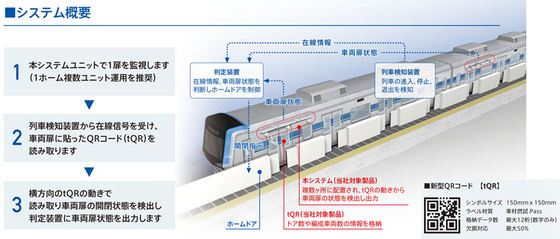
In 2019, DENSO WAVE, a company spun out of DENSO's development division, developed a new QR code that can function even if 50% of the code cannot be read. In 2020, a demonstration experiment was conducted on an automatic platform door opening and closing system incorporating this new QR code.
DENSO WAVE begins demonstration testing of new QR code-based platform door opening and closing control system at JR Kanayama Station | DENSO WAVE
As mentioned above, QR codes are a technology for storing character string information such as URLs, and are not inherently dangerous. However, just as there are security issues with clicking on a URL in an email, there are also security issues with accessing a URL in a QR code.
According to Assistant Professor Ruoti, if you access a URL listed in a QR code, you may be at risk of falling victim to phishing scams that imitate legitimate sites to steal your account information. Therefore, even if the QR code has a familiar company logo on it, Assistant Professor Ruoti says you should thoroughly verify the security of the URL before accessing it.
In addition, there have been cases where QR code scanning apps have had a vulnerability that allows devices to be hijacked when a malicious QR code is read. This vulnerability does not hijack a device when the URL in the malicious QR code is accessed, but rather the moment the malicious QR code is read. Assistant Professor Ruoti commented, 'Please use the QR code reading app and functions provided by the device manufacturer.'
Related Posts:
in Free Member, Note, Posted by darkhorse_log