Reported that the module 'TPM' that protects the PC can be hacked via hardware to access data
TPM sniffing – Sec Team Blog
https://blog.scrt.ch/2021/11/15/tpm-sniffing/
The TPM is a chip that is built directly into the motherboard or added separately to the CPU, making sure that the OS and firmware on the device have not been tampered with, and is responsible for securely storing the encryption key. .. BitLocker, which is a data encryption function of Windows, generally stores the volume master key inside the TPM, but the SCRT security team hacks the TPM to access protected data. I experimented.
The research team used Lenovo's ThinkPad L440 for the experiment. The TPM checks various system properties when the device boots to make sure the boot sequence has not changed, and if the verification is successful, it releases the volume master key and sends it to the CPU for disk encryption. It will be released and the OS will start loading.
In this process of 'sending the volume master key to the CPU,' the TPM sends signals using a bus that connects low-bandwidth devices such as the Low Pin Count bus (LPC bus) to the CPU. Due to the slow transmission speed of these buses, the research team claims that hacking the hardware can detect the signal of the volume master key and illegally decode the local tissue of the device.
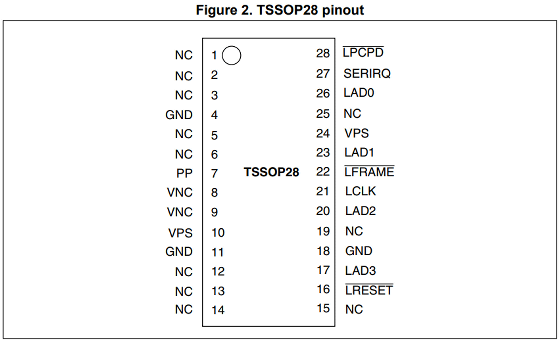
The research team first decided to manually find the TPM chip and uncovered the ThinkPad L440 to expose the motherboard. Then, I found a chip labeled 'P24JPVSP' near the bottom of the trackpad, and I guessed that this was a TPM chip called 'ST33TPM12LPC' that uses the LPC bus.

The pinout based on the ST33TPM12LPC data sheet is as follows. It seems that the signals of 'LAD0', 'LAD1', 'LAD2', 'LAD3', 'LFRAME', and 'LCLK' are required to acquire the volume master key, but the distance between each pin is only 0.65mm, so the signal It is quite difficult to directly solder the probe to measure. He also stated that there was a problem that the LCLK signal was missing.
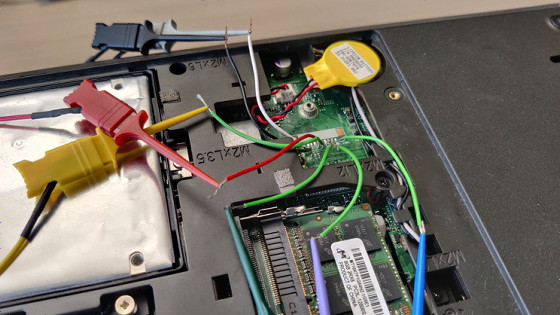
Fortunately, the research team was able to discover an LPC debug pad that was covered in black tape, making it easier to measure the signal than soldering it directly to the TPM chip. However, since the LCLK signal was not connected to the debug pad, the research team paid a fee to the website that sells the schematic of the motherboard online and obtained the schematic of the ThinkPad L440. As a result, it seems that there is a 'debug pad with nothing connected' and it is possible to send the LCLK signal to the debug pad by soldering.
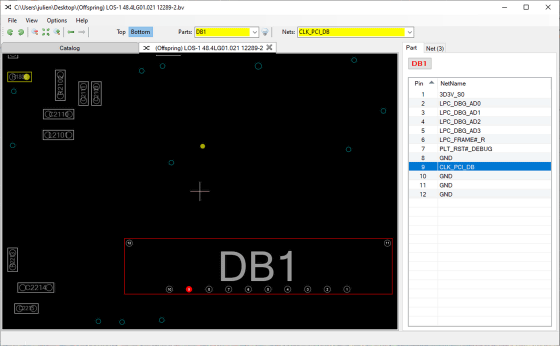
The research team soldered to send the LCLK signal to the debug pad ...

I soldered the probe to the appropriate debug pad.
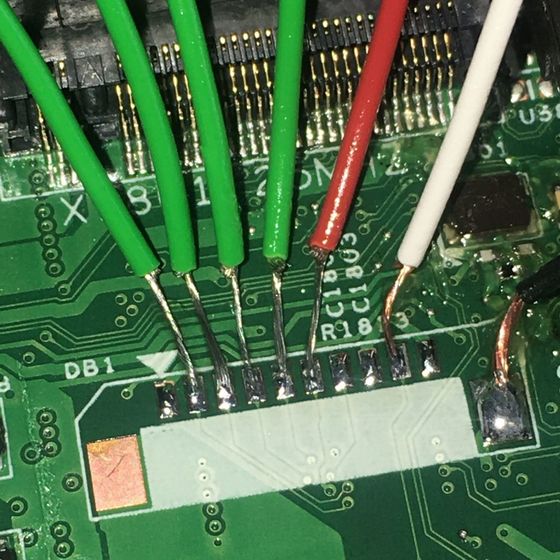
Then connect to the sniffer (left image), which is a device that steals LPC signals, start the device,

The research team states that the volume master key actually obtained can be used to bypass BitLocker protection and decrypt the local disk. As a result, operations such as 'accessing / tampering with saved files', 'stealing the database of local passwords', and 'creating a backdoor on the machine with malware' will be possible.
The attack can be carried out in just a few days, using tools available in the DIY store, without damaging the device. The latest Windows 11requirement , ' TPM 2.0, ' technically prevents TPM sniffing, but the researchers argued that there was still a risk of exposure to other physical attacks.
Related Posts: