There is also a demo video of ``iLeakage'' that steals passwords and emails from all iPhone models and Macs from 2020 onwards, which actually works.

A research team at the Georgia Institute of Technology has discovered an attack method called iLeakage that targets all iPhones and iPads, as well as Apple Silicon-equipped Macs released after 2020. If you access a website that exploits iLeakage, your information such as web service passwords and emails will be stolen.
iLeakage
iLeakage is a type of attack that exploits speculative execution , a technology that improves CPU performance by performing processing that may be necessary in advance. Valid for M series chips installed in some iPads. Therefore, all iPhones and iPads, as well as Macs released after 2020, can be targeted by iLeakage.
iLeakage executes an attack by ``installing malicious code on a website, tracking the actions of users who access the website, and stealing information.'' Below is a movie that records how Instagram ID and password are actually stolen through a website using iLeakage.
iLeakage Demo 1: Attacking Instagram and LastPass - YouTube
The movie shows a MacBook with Safari running, and a ``website using iLeakage'' is open in Safari. This ``website using iLeakage'' has a built-in function that ``Click inside the window to open Instagram in a new tab.''
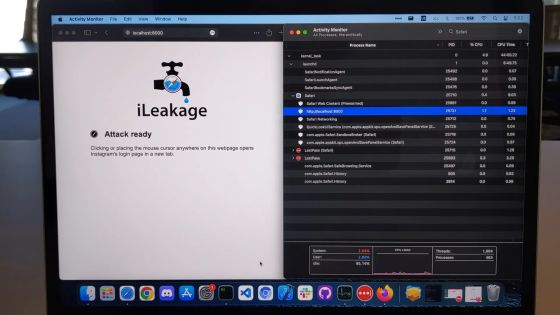
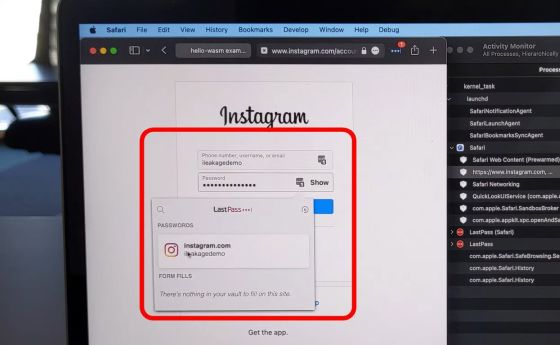
When a user clicks in the window, Instagram opens in a new tab, and the password manager automatically fills in their ID and password.
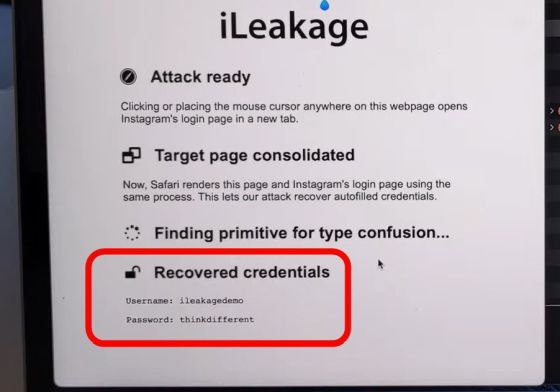
After waiting for a while, the Instagram ID and password were displayed on 'Website using iLeakage'. In the demo movie, only the ID and password are displayed on the screen, but if this attack is exploited, the attacker can steal the ID and password as is.
The following movie records how the subject of an email received in Gmail is stolen by opening a ``website using iLeakage'' in Safari on the iPad.
iLeakage Demo 2: Gmail Inbox on Mobile Safari - YouTube
iLeakage exploits a behavior specific to Safari's JavaScript engine. Therefore, on macOS, you can prevent iLeakage attacks by using web browsers other than Safari, such as Chrome or Firefox. However, since the iOS versions of Chrome and Firefox are fundamentally built using Safari, all browsers that can be used on iPhones and iPads are subject to iLeakage attacks. In the demo movie below, you can see how a ``website using iLeakage'' steals YouTube viewing history displayed on Chrome on an iPad.
iLeakage Demo 3: YouTube Watch History on iOS Chrome - YouTube
The research team reported the existence of iLeakage to Apple on September 12, 2022, and at the time of writing, Apple has released attack mitigation measures for macOS. However, Apple's attack mitigations are not enabled by default and must be explicitly enabled by the user. For macOS Sonoma, you can enable the mitigation by running the following command:
[code]defaults write com.apple.Safari IncludeInternalDebugMenu 1[/code]
If you are using an OS prior to macOS Ventura, the research team recommends updating to macOS Sonoma. Also, at the time of article creation, mitigation measures for iPhone have not been released.
Related Posts:
in Security, Posted by log1o_hf