A vulnerability that can accurately determine the location information of the pilot was discovered in the DJI drone, but the officials explained that it was 'as expected'
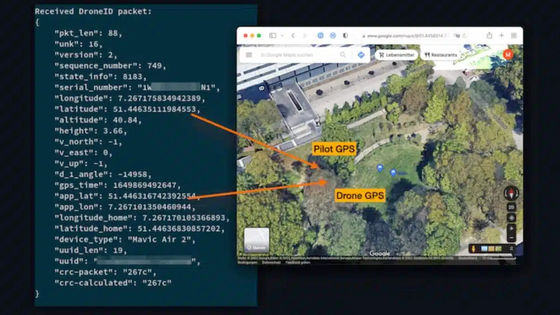
A security researcher team revealed that it is possible to accurately determine the position of a person who operates a DJI drone by intercepting and
Drone Security and the Mysterious Case of DJI's DroneID
(PDF file) https://www.ndss-symposium.org/wp-content/uploads/2023/02/ndss2023_f217_paper.pdf
DJI Drone Operator's Location Can Easily Be Intercepted
https://dronexl.co/2023/03/02/dji-drone-operators-location-intercepted/
DroneID is generally provided as AeroScope , a drone detection system for identifying suspicious drones flying around important facilities such as government facilities such as airports and nuclear power plants and infrastructure development facilities.

During the international conference in the field of security,
The research team has developed a prototype tool for receiving and decoding DroneID data and has published it on GitHub . In addition, the research team pointed out the vulnerability of DroneID, saying, ``A total of 16 vulnerabilities, from denial of service to arbitrary code execution, were found. Abuse such as crashing drones in flight from the device is possible.'
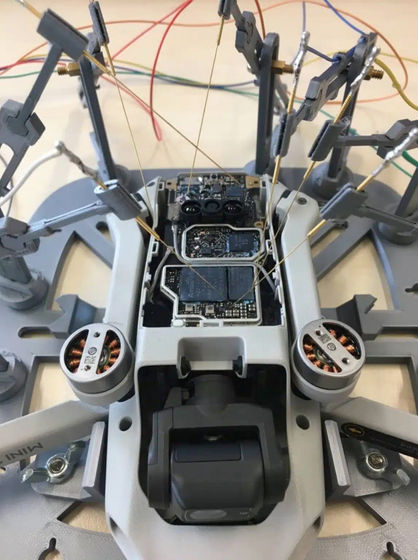
The research team revealed the vulnerability of DroneID by studying the firmware such as DJI Mini 2 and the latest DJI Mavic 3 , the drone body, and the wireless signal between the controller.
On the other hand, Brendan Shulman, former vice president of DJI, said, ``DroneID was developed with the intention of the current operation method.DJI originally developed DroneID because the US government created a system for tracking drones. 'The system can easily send the pilot's location and drone identifier to anyone who requested it.'
Furthermore, Shulman said, ``The requirements of the Federal Aviation Administration not only required that the drone's remote ID was not encrypted, but also that it was accessible to everyone in the vicinity, such as a smartphone.'' .
Within the industry, it's clear that the ASTM standard will be the means of compliance (ie Bluetooth and WiFi protocols). https://t.co/YN93onbg3s
— Brendan Schulman (@dronelaws) April 29, 2022
FAA rule is clear that Remote ID must be openly receivable by the public via commonly available devices. https://t.co/ymroaQlvHZ pic.twitter.com/Rlllurycv7
The problem isn't limited to DJI drones, and if the Federal Aviation Administration mandates remote ID requirements similar to DJI's for all consumer drones, similar problems could arise with any manufacturer. is high,” Shulman points out. However, Shulman declined to comment on the fact that consumers are not informed that DJI drones continue to transmit information about the pilot's location.
Drone news media DroneXL said that identifying the location of the pilot by intercepting DroneID is not only a concern for the privacy of general users, but also in the conflict between Ukraine and Russia by operating DJI drones for reconnaissance. It points out that it leads to endangering the safety of soldiers who do. As such, we speculate that it could have a significant impact on how drones are used in conflict zones and other war zones.
Related Posts: