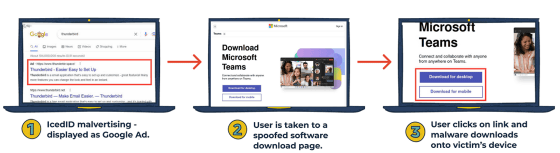
The number of cases where advertisements disguised as famous software such as Microsoft Teams and OBS and spreading malware are displayed in Google search results is increasing rapidly

Advertisements that disguise themselves as regular online advertisements and direct users to malicious websites for spreading malware are called '
A surge of malvertising across Google Ads is distributing dangerous malware - Spamhaus Technology
https://www.spamhaus.com/resource-center/a-surge-of-malvertising-across-google-ads-is-distributing-dangerous-malware/
Until further notice, think twice before using Google to download software | Ars Technica
https://arstechnica.com/information-technology/2023/02/until-further-notice-think-twice-before-using-google-to-download-software/
“Security threat researchers are used to seeing malvertising via Google ads to some degree,” said Sarah Miller, a researcher at Spamhaus Technology. 'We've seen a large-scale malvertising spike with multiple pieces of malware affecting well-known brands. This is not normal.'
According to Mr. Miller, malvertising , which has surged over the past few days, has confirmed the spread of many malware families such as AuroraStealer, IcedID , Meta Stealer , RedLine Stealer , Vidar , Formbook , and XLoader .
Traditionally, these malware families have been spread through phishing emails with document files containing malware and malicious spam emails. However, by the end of January, Miller explained that there was a sharp increase in the spread of these malware families through Google ads masquerading as popular software brands such as Adobe Reader , GIMP , Microsoft Teams , OBS , Slack , Tor , and Thunderbird . I'm here.
The series of malvertising is disguised as online advertisements that appear when you do a Google search for the name of the software. If you go to the site believing it's real and download the software as written on the site, your device will be infected with malware.
When the technology media Ars Technica actually searched for malvertising on Google search, the advertisement displayed at the top of the search for 'visual studio download' was a site called 'visual studio download[.]net'. included a link to
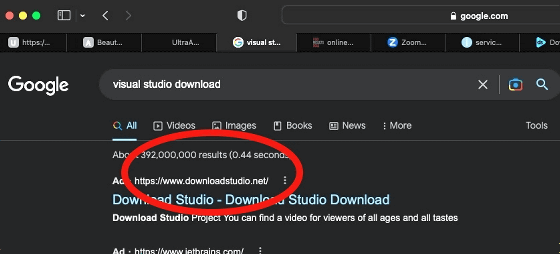
This 'visual studio download[.]net' has been certified as a malicious site by multiple anti-malware engines, and the software that can be installed contains malware. Ars Technica also states that it found malvertising when searching with Tor, Thunderbird, MSI Afterburner, Audacity, etc.
Of course Google takes various measures to combat malvertising, but these malvertising use obfuscation to evade endpoint protection and analysis, and use communication to multiple domains. It is said that the traffic of the C2 server is disguised.
A Google spokesperson declined to be interviewed by Ars Technica, but said through Ars Technica, ``Malicious actors often use sophisticated means to hide their identities and circumvent our policies and enforcement. To address this issue, over the past few years we have launched new authentication policies, enhanced advertiser verification, and improved our ability to detect and prevent coordinated fraud. We are aware of the recent increase in fraudulent advertising activity, addressing this issue is an important priority and we are working to resolve these issues as soon as possible. We are announcing a statement.
Spamhaus Technology says that the reason why malvertising has surged in Google ads is that it is likely that threat actors have started selling malvertising as SaaS on the dark web. Spamhaus Project domain expert Carel Bitter noted that the domains used in the malvertising were only recently created, and Google Ads approves ads that link to too-new domains. I questioned why.
Related Posts:
in Web Service, Security, Posted by log1h_ik