It is clear that URLs for sharing confidential information are entered into analysis tools, leading to information leaks
Whether a URL is malicious or not, such as
You can not simply publicly access private secure links, can you? | Vin01's Blog
https://vin01.github.io/piptagole/security-tools/soar/urlscan/hybrid-analysis/data-leaks/urlscan.io/cloudflare-radar%22/2024/03/07/url-database-leaks- private-urls.html
There are cases in which malware or fake websites that look exactly like the real thing are spread by exploiting URLs that point to web pages, images, and other items on the Internet.
17,000 ``malicious URLs'' are being spread by hackers on Discord - GIGAZINE

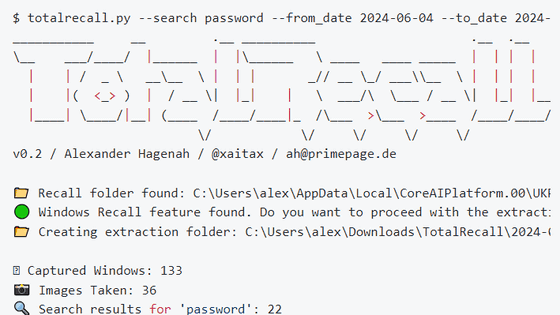
Tools such as urlscan.io, Hybrid Analysis, and URL Scanner exist to address these issues. However, vin01 points out that the number of people entering ``private URLs'' or ``URLs that can access confidential information'' into these URL analysis tools, resulting in information leakage, is rapidly increasing. I am.
According to vin01, the following URLs are shared using URL analysis tools.
・URLs for file sharing created using cloud storage services (Dropbox, iCloud, Sync, Egnyte, Ionos Hidrive, AWS S3, etc.)
・Cloud-connected NAS tools (such as Western Digital's
・URL of communication tools used by companies (Slido, Zoom, OneDrive, Airtable, etc.)
・URL for password reset, URL for Oauth sign-in
These URLs have one thing in common: they are very widely used and are designed to be accessible to anyone using a single private link that includes a random identifier to ensure security. In addition, there are cases where the information displayed on the access destination is protected by setting a password, but in that case, the risk of information leakage is reduced at once.
vin01 points out that many URLs of this type that should not be made public are published on URL analysis tools.
For example, some of the 'URLs that should not be made public' that were published on urlscan.io. In addition, vin01 has already reported this fact to urlscan.io, and the relevant URL has already been deleted.
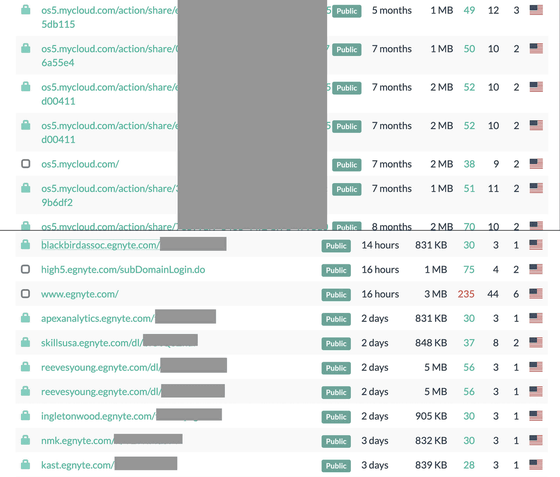
In addition, most of the 'URLs that should not be made public' published on urlscan.io are tagged with ' falconsandbox '. This appears to be input from Falcon Sandbox , a malware analysis solution developed by cybersecurity company CrowdStrike .
Therefore, vin01 seems to have thought that ``URLs that should not be made public'' were also published in Hybrid Analysis, a malware analysis tool owned by CrowdStrike. When we actually investigated, it seems that a large number of ``URLs that should not be made public'' were also published on Hybrid Analysis.
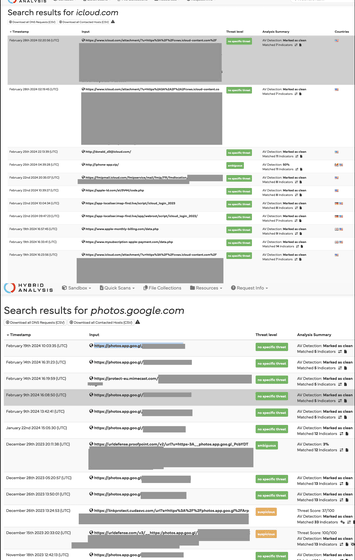
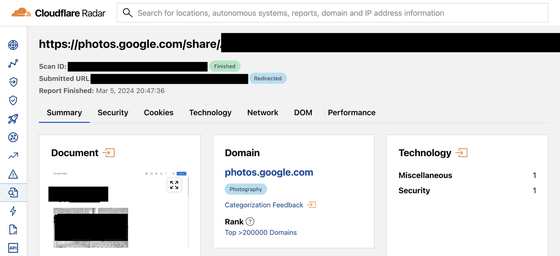
Furthermore, when we investigated Cloudflare's URL Scanner, which is popular as a free URL analysis tool, we discovered an even larger number of ``URLs that should not be made publicly available.''
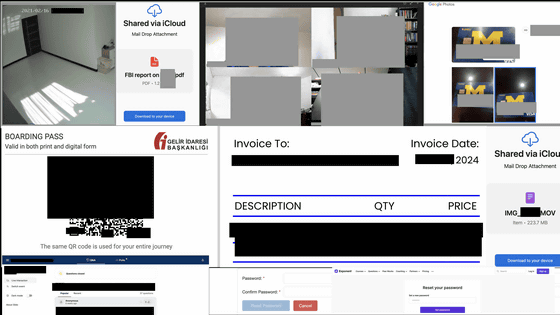
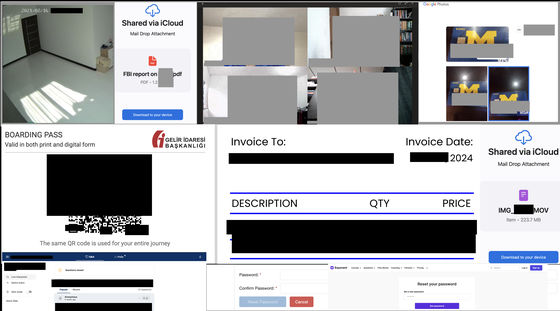
The general types of information hosted on ``URLs that should not be made public'' discovered by vin01 are as follows.
・Private files such as tax documents, invoices, photos, business communications, etc.
・Shared secret information using
・Recorded data of smart home devices
・Online meeting recordings saved in the cloud
Looking at the terms of service, it appears that urlscan.io and Hybrid Analysis do not have a mechanism to review existing content and flag or remove potentially sensitive links. Additionally, urlscan.io and Hybrid Analysis allow you to remove specific links by flagging them.
vin01 said, ``We are confident that the link in question will continue to exist.Using the default setting of ``Private scans'' is probably the most effective option, but ``Threat Intelligence and 'This defeats the purpose of 'sharing analytics', so be mindful of scan visibility when using these tools.'
Related Posts:
in Security, Posted by logu_ii