Intel's security technology ``SGX'' adopted for PowerDVD etc. is accompanied by vulnerability with ``dilemma due to troublesome update''

by
Intel's security technology, Software Guard Extension (SGX) , promises an isolated execution environment protected from all software running on the machine, but has been threatened by many side-channel attacks in recent years. It is said that there is. While Intel repeatedly patches SGX to restore security, a Georgia Tech team investigated whether the SGX update mechanism is effective in preventing attacks in real-world use.
SGX.Fail
https://sgx.fail/
When new SGX vulnerabilities are discovered, Intel typically releases new microcode to mitigate the issue. As microcode is distributed as part of BIOS updates, Intel is working with hardware vendors to integrate these microcode updates for affected platforms.
The research team analyzed six common SGX vulnerabilities and how long it took common vendors to release updates for their devices. The following image shows the analysis result, 'Dell' 'Lenovo' 'ASRock' 'HP' 'MSI' 'Gigabyte' apply patches for six vulnerabilities (color lines) (vertical axis) It shows how many days (horizontal axis) it took. On average, each vendor takes about two months to release a patch.
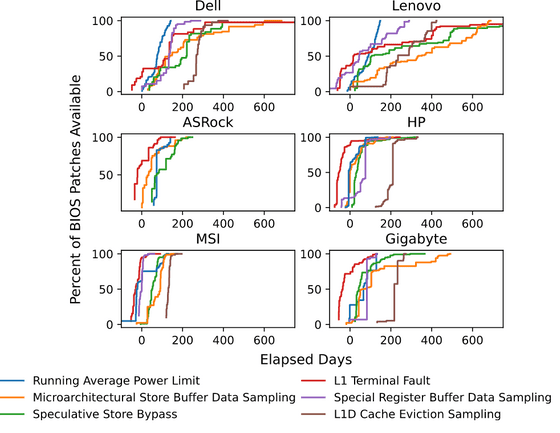
The frequency with which SGX vulnerabilities are discovered and disclosed forces SGX developers to make difficult trade-offs between security and usability. In an ideal world, the SGX developers would only want their software to run on the latest SGX platforms that they fully trust, but installing BIOS updates is a rather tedious task for most users, so Rather than requiring the platform to be fully up-to-date and reliable, it may be more practical to allow older platforms to run SGX software.
However, there are more than a few pieces of software affected by the SGX vulnerability. PowerDVD, a media player developed by CyberLink, is a popular software application for playing UHD Blu-rays on your computer. To prevent disc copying, PowerDVD uses SGX for Digital Rights Management DRM with AACS2 algorithm.
Adopting SGX severely limits the platforms on which Blu-rays can be played, making it impractical to force users to install additional BIOS updates. CyberLink therefore faces the dilemma of allowing AACS2 content to play on untrusted older machines, or restricting PowerDVD usage to a subset of trusted machines.
In fact, our research team has confirmed that PowerDVD allows playback of AACS2 content on unpatched SGX platforms. In addition, it seems that there is a way to reverse engineer the enclave, document the AACS2 algorithm, and play Blu-ray movies that do not support SGX by exploiting PowerDVD's SGX vulnerability.

A vulnerability caused by SGX has also been found in the Secret Network blockchain. Secret Network is the first publicly available instance of a Trusted Execution Environment (TEE) based private smart contract. Secret Network works by storing a secret key in the SGX enclave of each network validator. This key has a public component that you can use to encrypt messages to your network using hybrid encryption.
However, by exploiting the vulnerability found in SGX's xAPIC, it seems that any Pulsar-2 test network transaction can be decrypted, and the research team has actually launched a test service.
The research team said, ``SGX is not foolproof, nor does it require a sophisticated laboratory to exploit its vulnerabilities. We recommend that developers have a TCB recovery plan and implement SGX compromise mitigation as a development priority. In order to keep it down, we should encourage Intel and our partners to start recovering the TCB as soon as possible.'
Related Posts: