WebRTC-enabled browsers such as Chrome, Edge, Brave, etc. Vulnerability test site that leaks the user's local IP address

The function of 'WebRTC', which is used to reduce the time lag when making video and audio calls between user's web browsers, may expose the user's local IP address to a malicious site. It has been reported some time ago. A new test site has been released where you can experience IP address leakage.
WebRTC Local IP Leak Test ???? - github.com/niespodd/webrtc-local-ip-leak
GitHub - niespodd/webrtc-local-ip-leak: Oh no, stop this. You can see my local IP address ????! Use `foundation` attribute against CRC32 lookup table to reveal local IP address of a Chrome/Chromium visitor.
https://github.com/niespodd/webrtc-local-ip-leak
In 2015, security researcher Daniel Roesler demonstrated how a website makes a request to a STUN server , which sends back a ping containing the client's IP address and port. This showed that the user's local and public IP addresses canbe retrieved from these requests by JavaScript.

This issue primarily affects users using Google Chrome or Mozilla Firefox on Windows. 'If advertisers set up a wildcard domain on their STUN servers, this type of request could be used for online tracking, leading to further confusion and the ability for advertisers to identify users even more,' Roesler said. It will be easier,' he warned. In Chrome, etc., a method has been established to later convert the local IP address to UUID.local format using mDNS to prevent it from being acquired.
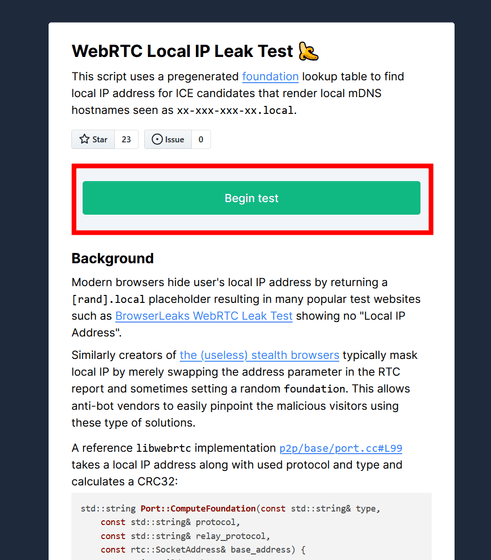
However, since this problem still exists, GitHub user Dariusz Niespodziany created and published a demo page that displays the local IP address from WebRTC reference parameters. That page is below. This script uses a pre-generated lookup table to find the ICE Candidate's local IP address, rendering the local mDNS hostname displayed as 'xx-xxx-xxx-xx.local'. Possible. Click 'Begin test' to run the test and check the local IP address.
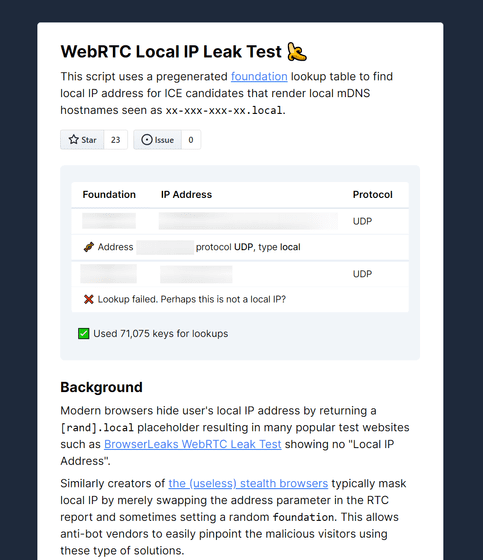
This will display your IP address, protocol, etc.
Related Posts:
in Security, Posted by log1p_kr