Movement to encrypt communication with DNS so that ISP can not read privacy-related information and personal information

Personal Internet access history etc.Privacy informationIs bridging the user and the InternetISPIn order not to be seen in,DNSThere is a movement to encrypt communication with.
How to keep your ISP's nose out of your browser history with encrypted DNS | Ars Technica
https://arstechnica.com/information-technology/2018/04/how-to-keep-your-isps-nose-out-of-your-browser-history-with-encrypted-dns/
The regulation on the neutrality of the network (net neutrality) of handling communications over the Internet fairlyAbolished in the United States in December 2017Since then, including huge IT companies such as Google and Facebook,Burger King makes a campaign to abolish "neutrality of Wapper"There are opinions that various regulations such as net neutrality regulation should survive.
Of particular concern is that communication is read to the ISP and access is controlled. Until now, when communicating with the DNS server when converting domain name to IP address, since it was an unencrypted plaintext exchange, the information "which domain you accessed" was missed by the ISP . But,From April 2018 DNS service provided by CloudflareBy using a specific external DNS such as 'DNS over HTTPS', you can encrypt the communication with DNS and it is possible to prevent the privacy information from being gathered to others to some extent.
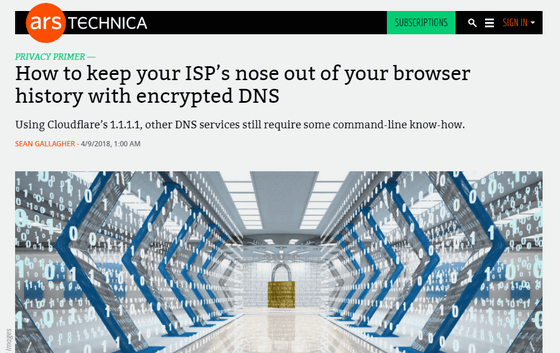
Before DNS over HTTPS appeared, there was a mechanism called DNSCrypt and DNS over TLS. Below is a scene of network security technician · Gallaher,DNS privacy daemon named StubbyCommunication with DNS done using DNS "WiresharkWhat I caught with an analysis tool called. The upper half is normal DNS traffic and the lower half is the communication done by "DNS over TLS" via Stubby. In the upper half it is obvious that you are trying to resolve the address of "www.google.com", but in the lower half you can see that it is encrypted and kept secret like "Application Data" .
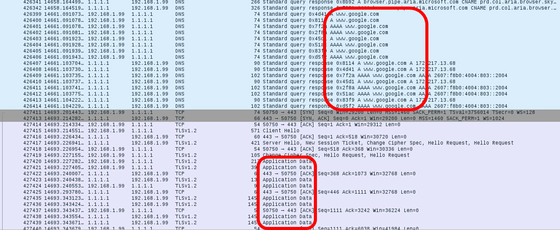
However, as DNSCrypt and DNS over TLS are implemented using the DNS protocol, developers have to learn the mechanism of DNS protocol and development has not advanced. Therefore, a method of providing the DNS service using the "HTTPS protocol" commonly used in Web communication was invented. Since DNS over HTTPS accesses the DNS server using requests such as HTTP GET and HTTP POST used for accessing Web pages, it can be used comparatively easily because it can process the same as HTTPS. The image below analyzes communication over DNS over HTTPS, but when you look at the log you can see that HTTPS is used.
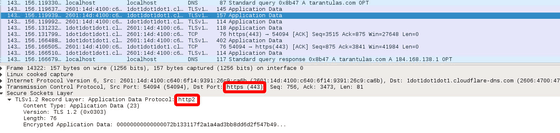
In the current situation there are still technical barriers left to spread widely, so the problem remains that we have to make it easier to use. Although it is not possible to obtain complete anonymity simply by encrypting communication with DNS, it is possible to slightly reduce the possibility of extracting privacy information.
Related Posts:
in Security, Posted by log1d_ts







