A security expert warns that if an IP address is leaked via WebRTC even in VPN, a VPN with risk of leakage is also disclosed

Used for secure network connectionVPNAlthough it is a service, VoidSec of a security countermeasure company reports that there is a danger that an IP address can be detected if it is used with a WebRTC-enabled browser due to the vulnerability of WebRTC. VoidSec warns that there is a danger of leakage in 23% of the VPN service we surveyed.
VPN Leak - VoidSec
https://voidsec.com/vpn-leak/
WebRTCIs a standard that enables real-time communication with browsers and mobile applications through API. WebRTC is used in voice chat, video chat, file sharing service, etc. WebRTC is enabled by default in browsers such as Google Chrome, Firefox, Opera.

When using VPN, what can be seen from the site is the public IP address assigned by the VPN server, and you can not see the true public IP address. For this reason VPN is also utilized to hide your identity by hiding your personal information.
However, according to VoidSec, in WebRTC-enabled browsers, due to the characteristics of WebRTC that directly connects two network nodes, even if you are connecting via VPN, you may acquire a true public IP address via WebRTC about. The VPN service which does not take measures against the problem (WebRTC leakage) that the true public IP address from this WebRTC leaks is the risk of identifying the user even if it is connected to the VPN.
VoidSec tested 70 VPN services using browsers enabled by WebRTC such as Chrome and Firefox by default and checked for WebRTC leakage countermeasures. The result is published in the following Google document.
VPN Web RTC Leak
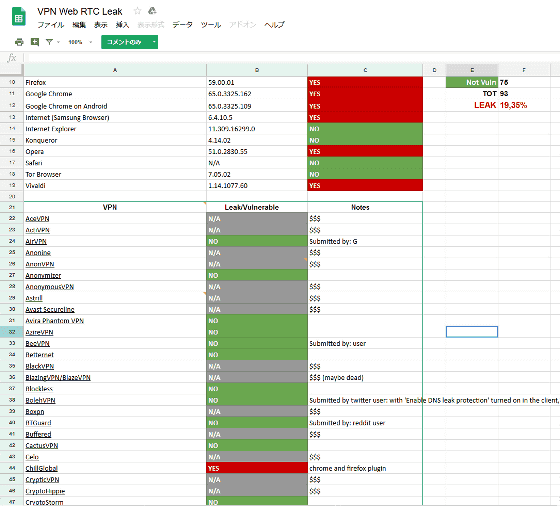
The following 16 VPN services do not take measures against leakage of WebRTC, and there is a danger of information leakage. However, it is important to note that many paid services have not been tested, so they are not safe because they are not listed below.
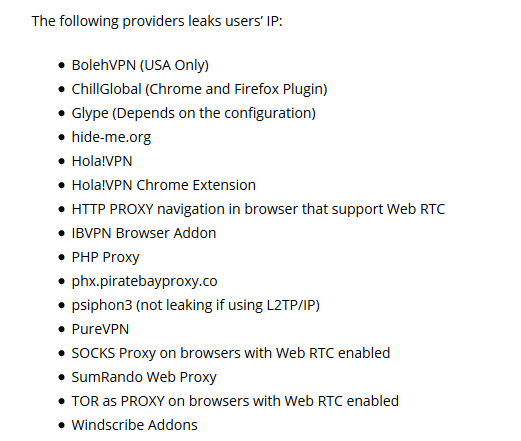
· Boleh VPN (USA Only)
· ChillGlobal (Chrome and Firefox Plugin)
· Glype (Depends on the configuration)
· Hide-me.org
· Hola! VPN
· Hola! VPN Chrome Extension
· HTTP PROXY navigation in browser that support Web RTC
· IBVPN Browser Addon
· PHP Proxy
· Phx.piratebayproxy.co
· Psiphon 3 (not leaking if using L2TP / IP)
· Pure VPN
· SOCKS Proxy on browsers with Web RTC enabled
· SumRando Web Proxy
· TOR as PROXY on browsers with Web RTC enabled
· Windscribe Addons
VoidSec states that the following method is effective to prevent identity identification when using VPN due to WebRTC leakage.
· Disable WebRTC
· Disable JavaScript
· Disable Canvas Rendering for Web API
· Configure DNS fallback for all connectors and adapters
· Clear all browser instances before and after VPN connection
· Clear browser's cache, history, cookie
· Turn off all external connections except VPN provider
In addition, VoidSec has published a site to check whether there is a risk of WebRTC leakage when connecting to VPN. When accessing the following page in the VPN connection state and the public IP address is displayed, there seems to be a risk of leakage.
IP Info
https://ip.voidsec.com/
Related Posts:
in Web Service, Security, Posted by darkhorse_log