Security researchers point out that the iPhone 'has a vulnerability that allows payment with Apple Pay without authentication'

Apple Pay, a contactless payment service, is a feature that allows you to easily pay with your iPhone or Apple Watch. With Apple Pay, you basically need to show that 'the owner of the device is paying' by unlocking with Face ID or Touch ID at the time of payment. However, in some transportation systems, you can pay the fare without unlocking the device or opening a specific app. Security researchers warn that a vulnerability in this feature could be used to pay for Apple Pay without authentication.
Practical EMV Relay Protection
Apple Pay with Visa Hacked to Make Payments via Unlocked iPhones | Threatpost
https://threatpost.com/apple-pay-visa-hacked-unlocked-iphones/175229/
Researchers discover security flaw with Apple Pay and Visa
https://www.siliconrepublic.com/enterprise/apple-pay-visa-contactless-hack-iphone
Apple Pay with VISA lets hackers force payments on locked iPhones
https://www.bleepingcomputer.com/news/security/apple-pay-with-visa-lets-hackers-force-payments-on-locked-iphones/
A research team at the University of Birmingham and Sally University backed by the National Cyber Security Center (NCSC) in the United Kingdom reported on the 'vulnerability that allows payment with Apple Pay without authentication'. According to the research team, Apple Pay, a contactless payment service provided by Apple for iPhones and Apple Watches, and a vulnerability in both the credit card company Visa 's system can be used without authentication. It will be possible to pay with Apple Pay.
According to the research team, the requirement to pay with Apple Pay without authentication is to pay the fare by train or other means of transportation without the hassle of waking, unlocking, or opening the app. It is only possible that the ' Express Card ' is enabled. In Apple Pay, whether or not the express card is valid is determined by the card transaction modifier (CTQ), but since this CTQ can be changed, even if you are not using transportation etc. You will be able to pay with Apple Pay without authentication. '

If you are using this express card with a Visa credit card, you can change the CTQ by using a card reader that sends a non-standard byte sequence. As a result, payment without authentication will be possible. Ken Manro, who was involved in the research, said, 'Logically, it is possible to steal money simply by bringing a contactless payment machine close to the iPhone in the pocket of a passenger on the subway. I point out.
All that is required for the attack is a payment reader, an IC credit card (EMV) compatible reader (first from the right), and a terminal such as an Android smartphone (second from the right) equipped with an NFC chip to communicate with the EMV compatible reader.

In the video that plays when you click the image below, you can see how the iPhone sends £ 1000 to credit card readers such as Europay, MasterCard, and Visa, which are not transportation. According to the research team, there are no restrictions on payments.
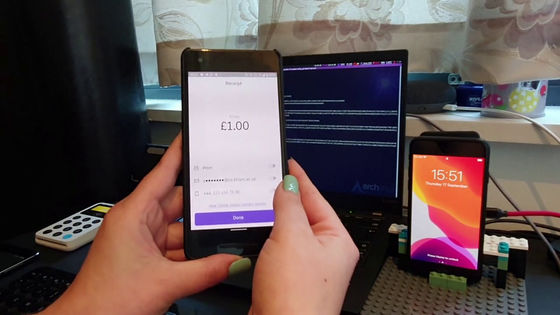
The research team described this attack method as 'a typical man-in-the- middle attack , where Proxmark sends a' magic byte 'to the iPhone to make it believe that the payment is due to an' express card 'and pay without authentication. I will approve it. '
The research team reported the problem to Apple and Visa twice in October 2020 and May 2021, but the vulnerability has not been fixed at the time of writing the article. Apple points out that this is a 'concern about the Visa system,' and Visa said, 'Apple Pay's payment system is secure and it would be difficult to exploit this vulnerability in a real attack.' ..
In fact, the research team notes that an attack that exploits this vulnerability requires more complex elements than the above prerequisites. One of the 'multiple elements' is 'to enable offline data authentication by changing some bits'.
Related Posts:







