A vulnerability was discovered in iOS 15 immediately after the release that allowed access to the contents of memos by bypassing the lock screen.

A movie released by a security researcher reveals that iOS 14.8 and
Lock screen bypass enables access to Notes in iOS 15 | AppleInsider
https://appleinsider.com/articles/21/09/20/lock-screen-bypass-enables-access-to-notes-in-ios-15
iOS 15 bug lets anyone bypass locked iPhone to access Notes app
https://mashable.com/video/apple-ios-15-lock-screen-bypass-notes
Security researcher Jose Rodriguez pointed out that iOS 15 has a vulnerability that allows it to bypass the lock screen and access the contents of the memo app. This vulnerability is an unauthorized access to the memo app by combining the 'VoiceOver ' function, which taps the iPhone screen to read out the elements in the area by voice, and the sharing tool.
Below is a movie that reproduces the vulnerability released by Mr. Rodriguez.
iOS 15 Lock Screen Bypass --YouTube
The iPhone X, which has been updated to the latest version of iOS 15, is used to reproduce the vulnerability.
Lock your device once.

Launch Siri from the lock screen.
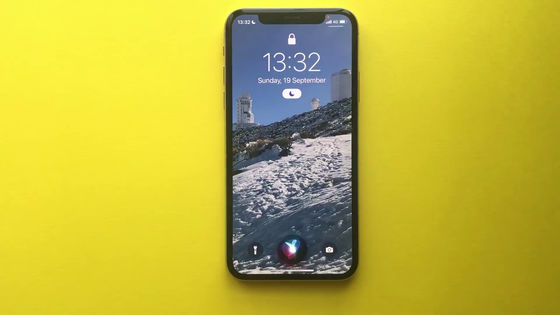
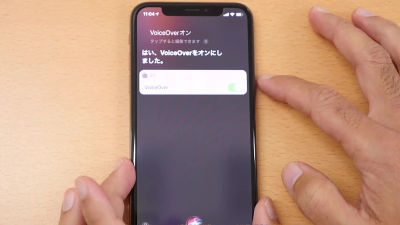
Enable the VoiceOver feature.

Launch the memo app. At this point, only a new note is created, you cannot check the contents of the note.

Open the control center again ...

Next, open the stopwatch of the clock app.

Tap on the screen to have the VoiceOver feature read each element aloud ...

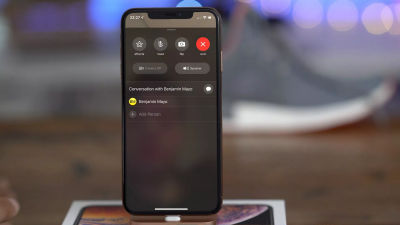
Open the control center ...

If you close it immediately, VoiceOver will call you 'Notes'.

When you take a screenshot, it now reads '0 Seconds' again on the stopwatch screen.

If you tap an empty area on the screen here ...

VoiceOver will read the contents saved in the memo. This succeeded in accessing the contents of the memo without unlocking the lock screen.

In addition, VoiceOver's gesture function allows you to copy the text being read from 'Edit'.

Lock the screen once ...

Use Siri to disable VoiceOver.

Then, call the attacking iPhone from another device.
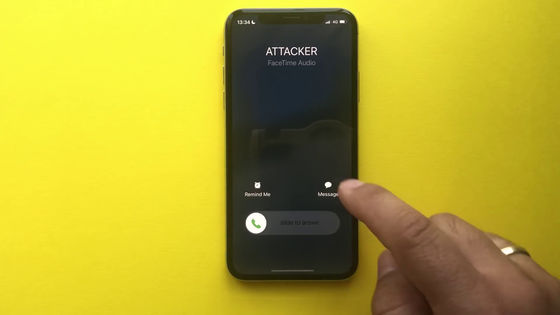
Instead of answering this call as is, tap the button labeled 'Message' and use a custom reply.
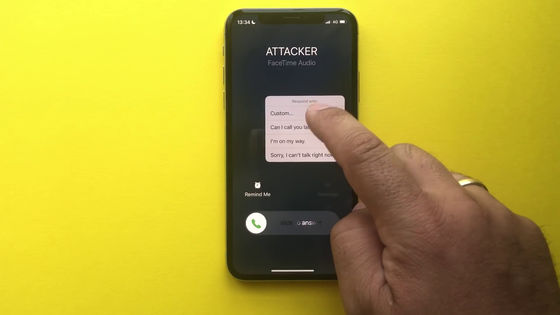
The mail composition form will be displayed, so if you paste it here ...
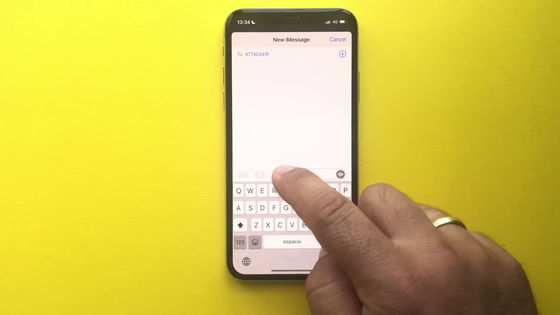
You can send the contents of the memo you copied earlier to a third party.
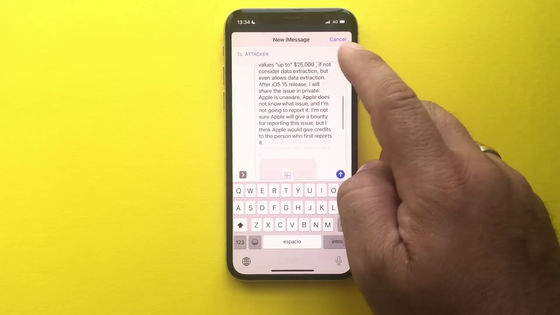
The vulnerability reported this time requires the attacker to have physical access to the 'iPhone that has been updated to iOS 14.8 or iOS 15 that is the target of the attack.' In addition, 'VoiceOver function is enabled' or 'Siri is enabled to enable VoiceOver function from the lock screen' is required, and 'Vulnerabilities such as memos and stopwatches are reproduced in the control center'. It seems to be quite difficult to actually use this vulnerability to illegally read notes on a third-party iPhone, as it even needs to include the apps needed to do so.
Rodriguez explained that such a vulnerability was disclosed to a large number of people about Apple's bug reward program. For Apple's bug rewards program, security researchers said, 'Other tech companies like Google and Microsoft communicate much closer than Apple and pay higher rewards for finding bugs.There are complaints such as 'I will give you', and Mr. Rodriguez agrees.
Mr. Rodriguez has reported to Apple about vulnerabilities such as 'CVE-2021-1835 ' and ' CVE-2021-30699 ' that are more serious than the vulnerabilities discovered this time. These vulnerabilities allowed access to messaging apps such as WhatsApp without unlocking the lock screen.
Apple has set a 'up to $ 25,000' bounty in its bug rewards program, but the first vulnerability Rodriguez has reported is a limit of $ 25,000. Although the dollar was paid, the second one was only able to receive the payment of 5,000 dollars (about 550,000 yen). In addition, Apple seems to have not completely fixed the vulnerability reported by Mr. Rodriguez, but Mr. Rodriguez who was dissatisfied with the series of measures decided to publish this vulnerability on YouTube. He says he has decided.
Rodriguez says he hasn't reported this vulnerability to Apple in advance.
Related Posts:
in Video, Software, Smartphone, Security, Posted by logu_ii