A vulnerability that can bypass the Windows storage encryption function 'BitLocker' is reported

by
The storage encryption function ' BitLocker ' installed by default in Windows encrypts storage such as hard disks and USB, and allows you to set a password to read the saved data. BitLocker, which is a standard function of Windows and can be easily introduced, is used by many companies as a countermeasure against leakage of confidential information, but security researcher Jonas L ( @jonasLyk ) avoids the lock screen of BitLocker. Was reported to have a possible vulnerability.
BitLocker Lockscreen bypass | secret club
https://secret.club/2021/01/15/bitlocker-bypass.html
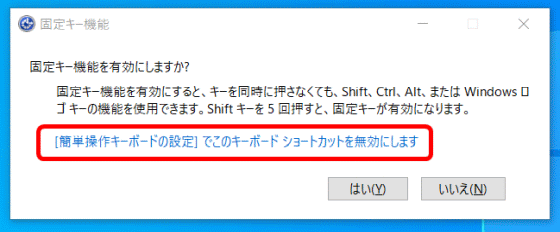
In the bypass method discovered by Jonas, the narrator function of Windows is first enabled, and the screen when the password is forgotten is displayed on the lock screen. As it is, press the 'Shift' key 5 times in a row to display a pop-up that performs 'Enable fixed key function'. This pop-up contained a link to 'Settings', and it was possible to activate the settings from the lock screen.
The movie that actually uses this method and activates the setting from the lock screen is as follows.
March 8, 2020 --YouTube
The red frame is the pop-up where you can enable the fixed key function.
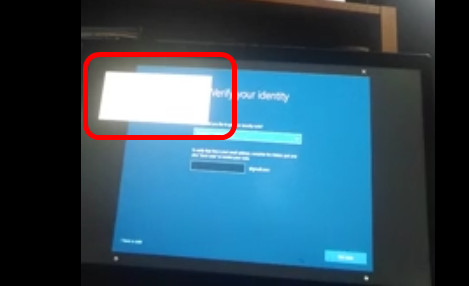
When clicked, the frame of the setting button by the narrator was displayed.
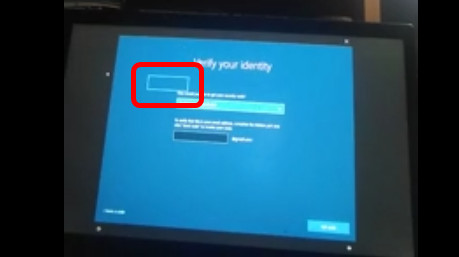
Relying on this narrator frame, you can change the settings from the lock screen.
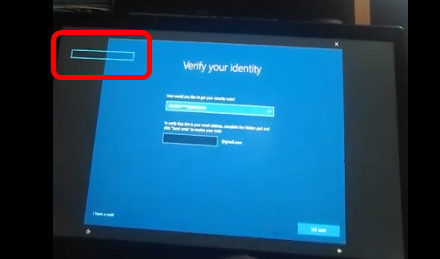
It is possible to change the item of 'automatic playback of removable drive', change this setting to 'open folder and view files' and insert the USB into the PC to execute the files in the USB. It was said that.
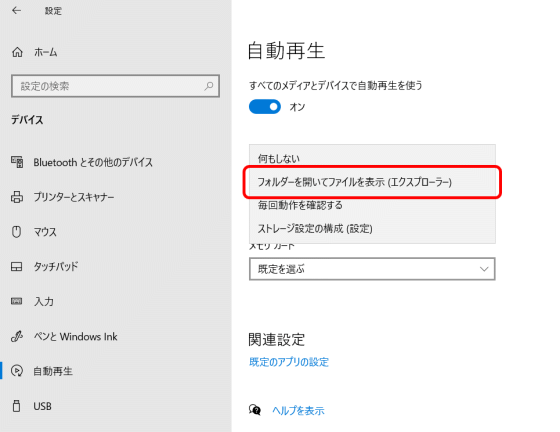
After autoplaying the USB, it was possible to read the data by creating a shortcut destined for a folder in the system area and embedding an executable file from that shortcut, Jonas said. The vulnerability found this time was fixed by Microsoft in July 2020, and you can check the details of the patch from the following URL.
CVE-2020-1398 --Security Update Guide --Microsoft --Windows Lockscreen Elevation of Privilege Vulnerability
Jonas, who discovered the vulnerability, is also the discoverer of a command that destroys NTFS-style storage.
There is also a 'shortcut that destroys storage just by looking' that can find commands that can immediately corrupt storage in just one line --GIGAZINE

Related Posts: