What is the method used by the ransomware 'Ryuk' that robbed the ransom of 15.5 billion yen?
Crime Laundering Primer: Inside Ryuk Crime (Crypto) Ledger & Risky Asian Crypto Traders
https://www.advanced-intel.com/post/crime-laundering-primer-inside-ryuk-crime-crypto-ledger-risky-asian-crypto-traders
A study by security firms Advanced Intelligence and HYAS found that Ryuk has earned more than $ 150 million in ransom so far.
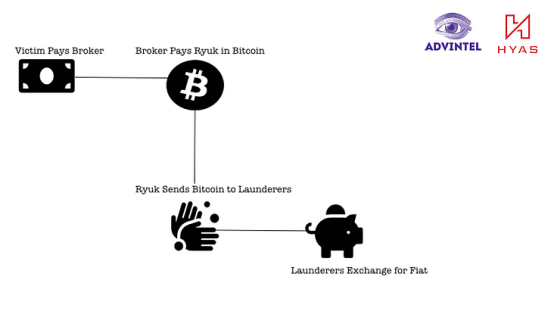
The image below shows the process of converting Bitcoin that Ryuk received as a ransom from an attack target into cash. A study by Advanced Intelligence revealed that Ryuk is cashing on Asia-based cryptocurrency exchanges Huobi and Binance . Generally, strict identity verification is required for cashing crypto assets on exchanges, but since the identity verification procedure is not strictly operated on the exchange used by Ryuk, it is used for money laundering. Advanced Intelligence points out that this is often the case.
Before launching a ransomware attack by Ryuk, an attacker
In addition, attackers using general ransomware use chat services on the web to contact the attack target, while attackers using Ryuk use highly encrypted communication to contact them. It is very difficult to identify the communication source because it is taken. In addition, some ransomware attackers may negotiate the target of the attack, but the contact from the attacker using Ryuk seems to be very clerical and there is no room for negotiation.
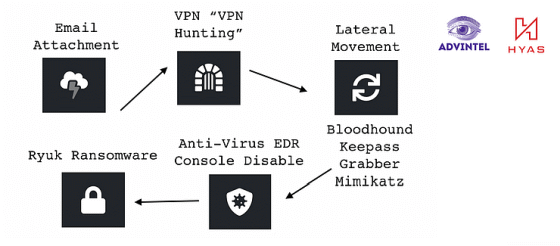
Advanced Intelligence 'restricts the execution of macros in Microsoft Office', 'updates remote access points and uses' two-step authentication '', and 'remote access tools can be used' to prevent attacks by ransomware. We recommend that you take measures such as 'Limiting IP'.
Related Posts:
in Security, Posted by log1o_hf