What is 'Circles' that sells spy tools to the nation that steal mobile phone calls, emails, and location information without permission?

By abusing mobile communication systems built around the world to provide network functions to smartphones, etc., intercepting the contents of calls and emails being made all over the world, and the location of terminals connected to the network
Running in Circles: Uncovering the Clients of Cyberespionage Firm Circles --The Citizen Lab
https://citizenlab.ca/2020/12/running-in-circles-uncovering-the-clients-of-cyberespionage-firm-circles/
In 2013, it became clear that the US government has been operating a monitoring system ' PRISM ' that can peep at personal information existing on servers such as Google and Apple for more than 5 years. The fact that cross-border surveillance has been carried out under the initiative of the government has become a big topic, but it is now regarded as a problem that companies are selling tools for such large-scale surveillance. I will. Tools that enable widespread monitoring at the global level are becoming widespread by exploiting vulnerabilities in mobile communication systems.
One of the vulnerabilities that exist in mobile communication systems is derived from the common line signal No. 7 (CCSS7). CCSS7 is a protocol suite developed in 1975 to exchange information and route calls between different carriers. At the time of CCSS7 development, the telephone network was built exclusively by some telecommunications carriers, so there was no need to include authentication or access control in CCSS7 at the time. However, after that, due to deregulation and the spread of smartphones, CCSS7 became widely used. As a result, CCSS7, which has no access restrictions due to the authentication process, has become a target for attackers.
By utilizing CCSS7, attackers can not only intercept voice calls and SMS text messages on mobile phones, but also track the location information of mobile phones. You can also intercept the SMS, so you can intercept the two-factor authentication code sent to the SMS. It seems difficult for telecommunications operators to block attacks that exploit vulnerabilities in CCSS 7 because it is difficult and costly to distinguish between malicious and normal traffic.
CCSS7 is mainly used in 2nd generation mobile communication systems (2G) and 3rd generation mobile communication systems (3G), and in Japan, the main 4th generation mobile communication system (4G) uses another protocol, DIAMETER . I have adopted it. However, since DIAMETER also provides an access control function by authentication as an option, it is said that the problems caused by CCSS7 may be carried over to mobile communication systems after the 5th generation mobile communication system (5G).

'Circles' is one of the companies that builds spy tools that exploit such CCSS7 vulnerabilities. Circles was founded in 2008 and was merged with NSO GROUP after being
Most of the reality of Circles is a mystery, but some details have been revealed by leaks from the inside. There are two types of Circles spy tools: a system used by connecting to the infrastructure built by telecommunications carriers, and 'Circles Cloud' that interconnects telecommunications businesses around the world and intercepts communications via the cloud. It seems to do.
It's unclear how Circles' spy tools are integrated with Pegasus, but a former NSO GROUP employee said, 'Pegasus has a terrible integration with Circles.' 'Circles exaggerates the capabilities of the system.' and by that, ' said we.

Circles has set up a fake phone company called 'Circles Bulgaria' to make it easier to intercept communications around the world. After investigating this Circles Bulgaria, we succeeded in identifying the host name of the firewall. As a result, it is clear that Circles employees are communicating with email addresses that include the '@ tracksystem.info' domain.
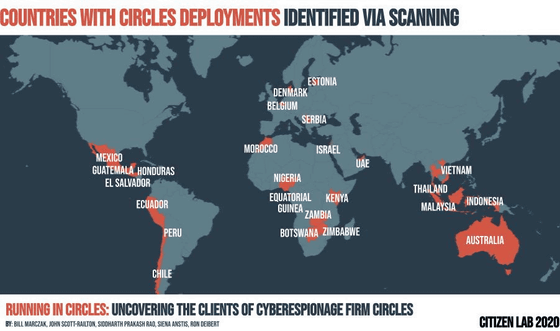
Ultimately, The Citizen Lab identified 25 nations that are likely to be Circles customers from 252 IP addresses. In addition, we have successfully identified 17 potential Circles customers based on WHOIS information, passive DNS, firewall IP, and other information.
The 25 nations and 17 government agencies that are likely to be Circles customers are:
·Australia
·Belgium
・ Botswana (Information Security Service Bureau)
・ Chile (Investigation Police)
・ Denmark (Army Command)
・ Ecuador
・ El Salvador
・ Estonia
・ Equatorial Guinea
・ Guatemala (General Bureau of Citizen Information)
・ Honduras (National Information Bureau)
·Indonesia
·Israel
・ Kenya
·Malaysia
・ Mexico (Mexican Navy, Government of Durango)
・ Morocco (Ministry of Interior)
・ Nigeria (Defense Intelligence Agency)
・ Peru (National Security Agency)
・ Serbia (Security Information Bureau)
・ Thailand (Domestic Security Force, Military Intelligence Battalion, Drug Control Bureau)
United Arab Emirates (Supreme National Security Council, Dubai Municipality, Royal Group)
·Vietnam
·Zambia
·Zimbabwe
Regarding Circles, which has grown significantly with government agencies as its customers, The Citizen Lab said, 'Many of the government agencies that serve Circles have a dire past of human rights abuses and abuse of technical surveillance. Many of Circles' customers lack public transparency and accountability, and only in countries where there is no or minimal independent oversight of the activities of security agencies. '
The Citizen Lab also said, 'It is very difficult to investigate and track companies like Circles that exploit vulnerabilities in CCSS7. Many attacks using CCSS7 do not require involvement with monitored targets. There is no evidence of espionage on the device used by the monitored device, and the lack of transparency of the telecommunications carrier has led to the hiding of the activities of espionage companies like Circles, which spy tools It has also helped to further expand the potential for use, 'he said, adding that the lack of transparency of telecommunications carriers is at the root of the problem.
To government agencies that are customers of Circles, The Citizen Lab said, 'The explosive growth of the global surveillance industry over the last decade has led to the use of espionage technology for problematic regimes and security services. These groups are using their newly acquired spy tools to commit cross-border human rights violations and squeeze political opposition. Circles has close ties to them. It should be of particular concern as it has been reported to merge with NSO GROUP, which has a notorious track record of abusing spy tools in the past. '
In addition, The Citizen Lab fears that the growth of the surveillance industry could continue to reduce legitimate and democratic activity. To protect the rights of citizens, 'establish a stronger domestic and international legal framework and strictly monitor the import and export of surveillance technology' 'For companies that develop and sell surveillance tools such as Circles' , Construction of a system that thoroughly enforces due diligence and enforces severe penalties in the event of violation '' Legislation that allows people damaged by surveillance technology to claim damages against companies ' Is suing.
Related Posts: