It turned out that NSA was planning to distribute spyware which steals personal information from smartphone via app store

It is an intelligence agency in the United States of AmericaUS National Security Agency(NSA), an app store that Google distributes applications for Android devices "Google Play"And an application store operated by Samsung"Galaxy AppsHacking a plan to spread secretly spyware to collect data from smartphonesThe InterceptIt was clarified by investigation.
NSA Planned to Hijack Google App Store to Hack Smartphones - The Intercept
https://firstlook.org/theintercept/2015/05/21/nsa-five-eyes-google-samsung-app-stores-spyware/
Spy agencies target mobile phones, app stores to implant spyware - Canada - CBC News
http://www.cbc.ca/news/canada/spy-agencies-target-mobile-phones-app-stores-to-implant-spyware-1.3076546
In June 2013, as a staff member of the NSA in the past has a history of involvement in information gathering activities conducted by the countryEdward SnowdenMr. Leak leaked top secret sentences that reveal the actual situation of personal information collection by NSA to multiple newspapers. This allows the NSA to refer to personal information on the server of a large company without obtaining special authorization "PRISM"Similarly, the British intelligence agency"GCHQAlso uniqueCommunication interceptionIt was revealed the terrible facts of intelligence activities by governments, such as conducting acts. And, from a part of the secret sentence released at this time, The Intercept discovered and reported that NSA is planning a communication monitoring project for smartphones.
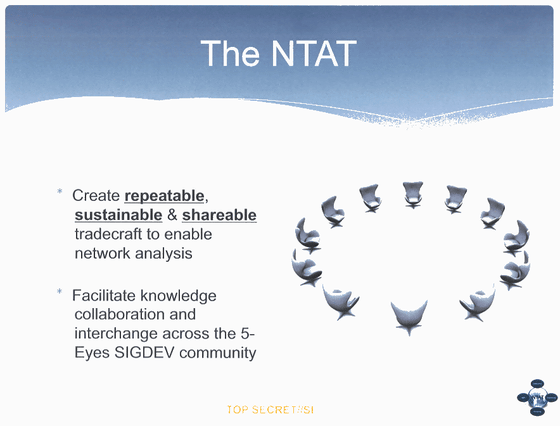
The NSA-planned smartphone communication monitoring project will be conducted from November 2011 to February 2012 by the five countries of the United States, Canada, the UK, New Zealand and Australia that have the agreement on information gathering activities "Five Eyes" It was. In the project, five countries jointly formed a team called "Network Tradecraft Advancement Team (Team for improving know-how necessary for network spy activities, abbreviation: NTAT)" without names, and to develop a new technology for smartphone monitoring It is undertaken.
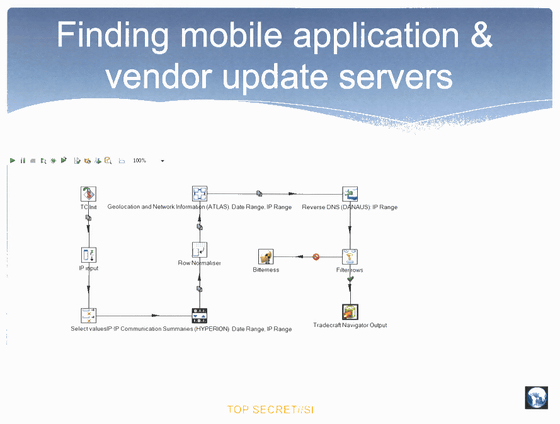
In the project, NSA's "XKeyscore"Using the data retrieval system to identify the communication flow of smartphones aimed at tracking smartphones accessed from servers of app stores such as hacked Google Play and Galaxy Apps.
In addition, there is also part of the test plan called "Irritant Horn" which develops a method for extracting all information secretly from the target smartphone. What I was developing with "Irritant Horn" was spyware that forcibly installs on a smartphone that accessed the app store and sends the data inside the terminal to the outside without being noticed by the user.
It seems that the project aimed at collecting personal information from the target's terminal by combining hacking of the application store and spyware that gathers personal information from the terminal and sends it to the outside, but this plan was drafted It was between 2011 and 2012, and it is not clear what kind of project the project followed.
The NSA has formulated this plan as a result of spreading to the Middle East and North Africa on Tunisia in December 2010Arab SpringAlthough it is concerned about popular movements like "Irritant Horn development as a system to monitor more and more restless molecules" is stated in secret sentences.
Furthermore, it was also found that the NSA of that time was aimed particularly at African countries such as Senegal, Sudan, Congo and others. However, the countries in which the app store server was hacked included France, Cuba, Morocco, Switzerland, Bahamas, the Netherlands, Russia, and others.

In addition, NTAT joint team of five countries, mobile browser applications that are used particularly frequently in China and India in Asia "UC BrowserIt is also clear that a privacy-related vulnerability exists. UC Browser is not so famous application in Western countries, but mainly in AsiaApproximately 500 million usersIt is a popular application that has won. In the top secret sentence, "It is written that UC Browser leaked the user's personal information and it was very appreciated for the intelligence agency".
You can tell what application UC Browser is by looking at the following movie.
UC Browser 10.0 for Android - Clean yet Complete - YouTube
Research institution of University of Toronto "Citizen Lab"The English version and the Chinese version of Android application · UC Browser are" having big problems in security aspect and privacy "Publish detailed reportdoing. According to Citizen Lab, the search history of the user · SIM card number · terminal ID etc are leaked from the application. After Citizen Lab made a report, UC Browser is updating the application, and it says that the problem has been fixed.
Ron Deibert, director of Citizen Lab, said, "The vulnerability of UC Browser not only expose millions of app users to the risk of personal information leakage but also hackers develop technology to steal personal information There is a possibility that it may have helped. " In addition, "Intelligence agencies do not publish information, of course, so even if vulnerabilities are found, they are only informed internally, and in most cases they will be used to create weapons, Ron said NSA created some eavesdropping tool from the vulnerability of UC Browser.

ByHostingCoupons
When Mr. Snowden revealed confidential information, it became clear that the five countries that signed the Five Eyes agreement use spyware to steal e-mail, Internet history, phone content, movies, photos, etc. from iPhone and Android terminal Although it was not understood until the method of the important though it was. However, there is no doubt that facts such as "development of Irritant Horn" and "discovery of vulnerability of UC Browser" clarified by this Intercept's report have something to do with communication interception technology.
In addition, the materials of the presentation made at Five Eyes in 2012 are to be seen from the following, you can see that the existence of NTAT and Irritant Horn is spoken.
Five Eyes presentation: Synergising Network Analysis Tradecraft
https://www.documentcloud.org/documents/2083944-uc-web-report-final-for-dc.html
Related Posts:
in Note, Posted by logu_ii







