What was the 'invisible hack' that attacked iPhone user journalists?

On June 22, 2020, the international human rights group
Moroccan Journalist Targeted With Network Injection Attacks Using NSO Groups Tools | Amnesty International
https://www.amnesty.org/en/latest/research/2020/06/moroccan-journalist-targeted-with-network-injection-attacks-using-nso-groups-tools/
Journalist's phone hacked by new'invisible' technique: All he had to do was visit one website. Any website. | The Star
https://www.thestar.com/news/canada/2020/06/21/journalists-phone-hacked-by-new-invisible-technique-all-he-had-to-do-was-visit-one- website-any-website.html
A Moroccan journalist, Radi is a human rights activist known for addressing corruption and human rights issues in Morocco. Several international human rights groups, including Human Rights Watch and the National Union of Journalists , condemned Radi's arrest when he was arrested in December 2019 for criticizing the Moroccan authorities' crackdown on the human rights movement. And had a large-scale protest in front of the Moroccan parliament.
Mr. Radi was later released, but is currently on appeal after being convicted of four months in prison for insulting the court. Also, in parallel with the trial, he keeps in touch with sources and continues to carry out activities. Meanwhile, Amnesty International found out that Mr. Radi's iPhone was being monitored.
According to a report from Amnesty International, the tool used to attack Mr. Radi was 'Pegasus,' a tool by Israeli-based spyware developer NSO Group . Pegasus has been used for hacking via Facebook's chat app WhatsApp .
There is also a case where spyware is installed, a vulnerability that allows you to take over your smartphone with a single phone call is found in the chat application WhatsApp-GIGAZINE

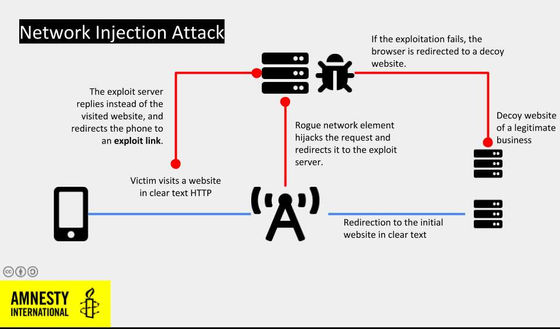
However, Mr. Radi's iPhone had never received a suspicious incoming WhatsApp and there was no evidence of accessing a suspicious URL. Instead, the security lab at Amnesty International, which analyzed Radi's iPhone, found evidence of a 'network injection attack' targeting Radi.
A network injection attack is an attack that intercepts either 'communication between a smartphone and a base station' or 'connection from the base station to the Internet', and spies spyware on the website viewed by the terminal. is. Since the attack is fully automatic and takes a very short time of milliseconds, it is difficult for the target person to notice the attack.
It has also been revealed that the targeted attacks on Maati Monjib and Abdessadak El Bouchattaoui, Moroccan human rights activists similar to Mr. Radi, used fake mobile base stations, believed to belong to the NSO Group. I will.
John Scott-Railton of Citizen Lab, a research institute that is following the NSO Group's move in Morocco, along with Amnesty International, has posted on Twitter a picture of a fake base station believed to be made by the NSO Group.
2. We've known for a while that NSO has been marketing Network Injection. From tactical stuff like this cell tower spoofer, to on-premises kit.(pic taken by @beckpeterson ) pic.twitter.com/qm7FUfv47J
— John Scott-Railton (@jsrailton) June 22, 2020
“A network injection attack is hard to identify because it has few visual clues. You can avoid malicious links, such as through fascinating SMS messages, by simply clicking on them, but network injection attacks can Occurs invisibly just by browsing.” Amnesty International pointed out.
Amnesty International has only found evidence of a network injection attack this time, with no evidence that Moroccan authorities are involved. However, because the attack is very likely to belong to the NSO Group, and because the NSO Group only serves the government, Amnesty International speculates that the attack on Mr. Radi was due to Moroccan authorities. I am.
The oldest attack on Mr. Radi took place on September 13, 2019, just after the NSO Group announced its (PDF file) Human Rights Policy on September 10. Three days later. In its human rights policy, NSO Group promised to 'discontinue service if a customer 'abuses' their product.

As a result, Amnesty International said, 'The findings of this survey mean that the NSO Group is not conducting proper due diligence and that its human rights policy is becoming famous and innocent.' The Moroccan authorities, who appear to be behind the NSO Group, were told, ``The continued abuse of NSO Group tools in Morocco respects their right to freedom of expression, association and peaceful assembly. , Has shown that it is neglecting to protect it,' he accused the authorities of responding.
``It was revealed that the journalists were intercepting communications, and sources were stumbling, as the news daily was intercepted, according to an interview with Canada's daily Toronto Star. Monitoring tools worked really well. I think it is.'
Related Posts: