'Lord of SQL Injection', a site where you can learn about SQL injection vulnerabilities while capturing dungeons

An attack that manipulates the database illegally by executing a character string that the application does not expect is called
Lord of SQL Injection
https://los.rubiya.kr/
First, access Lord of SQL Injection and click '[enter to the dungeon]'.
It's my first time to use Lord of SQL Injection, so click 'Join'.
Enter the ID, email address, and password used in Lord of SQL Injection and click 'Join'.
Enter the ID and password you registered earlier and click 'Login'.
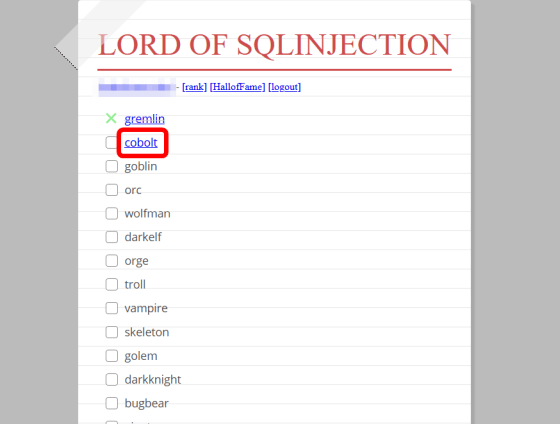
The screen to select the enemy is displayed. Click on the first enemy 'gremlin'.
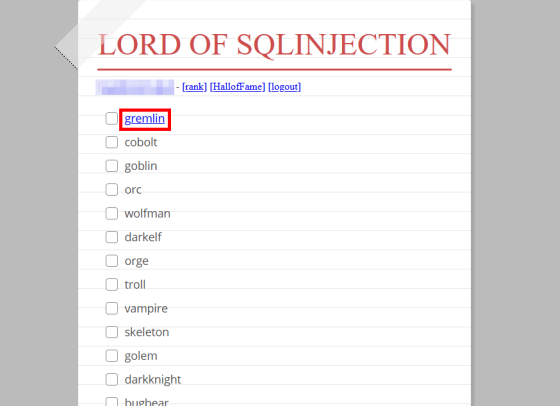
The SQL query executed on the website and the PHP code are displayed. While referring to the PHP code, you can defeat the enemy if you can execute invalid SQL queries.
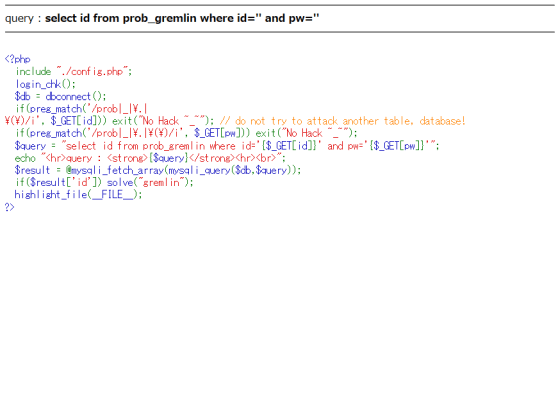
In this problem, you can execute a query that returns some value, so add '?id=admin&pw=' or '1' = '1' to the URL and execute.
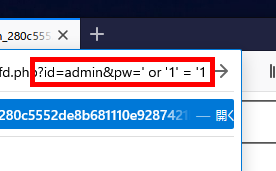
'GREMLIN Clear!' is displayed and I was able to defeat the enemy safely.
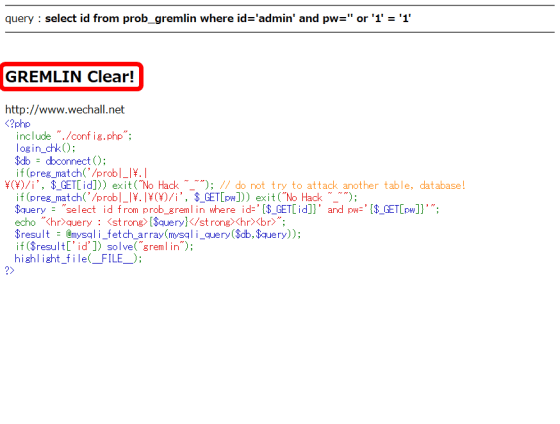
If you solve the problem and defeat the enemy, you will proceed to a new enemy.
The problem of 'cobolt' is like this. It seems that you need to put the
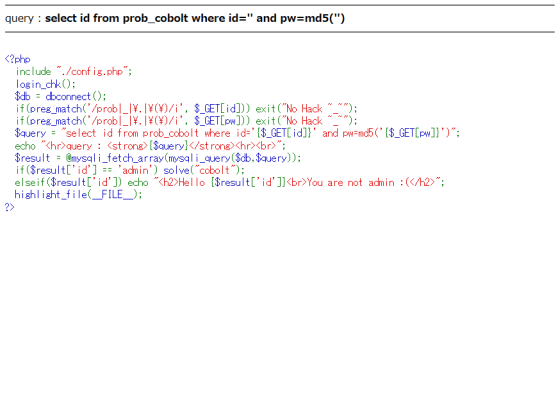
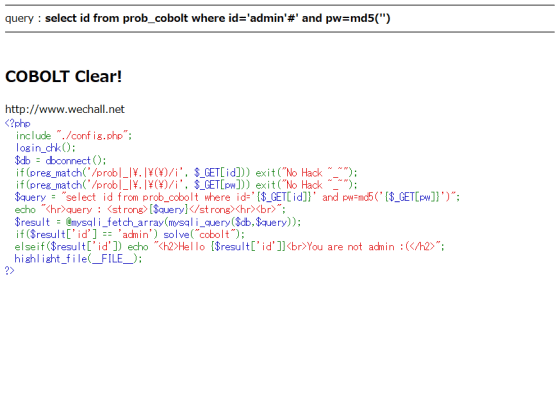
It is also one way to put the MD5 hash value, but this time I wrote it in the URL as follows and executed the query with the password part commented out.
[code]?id=admin'%23[/code]
Cleared safely.
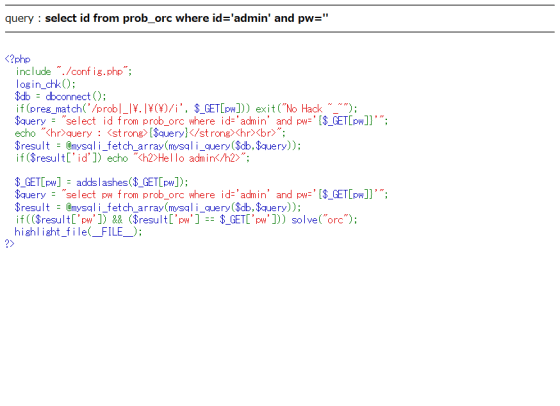
Although 'gremlin' and 'cobolt' were SQL injection types that execute invalid queries, there are also types of enemies that parse correct passwords using blind SQL injection.
There are a total of 49 problems of Lord of SQL Injection including 'All Clear'. Even if you don't understand the problem, you can find many Korean explanations online.
Related Posts:
in Review, Software, Web Service, Posted by darkhorse_log