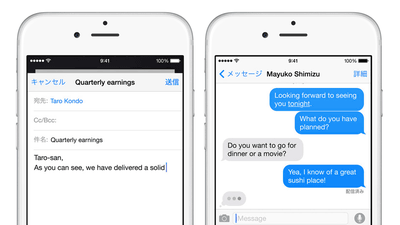
An unfixed zero-day vulnerability was found in the standard email application of iPhone after iOS 6, and attack examples have already been confirmed

Security company ZecOps announced on April 22, 2020, 'An attack has been identified that exploits an unfixed zero-day vulnerability in the email app installed by default on iOS.' This vulnerability existed at least from iOS 6 released in September 2012, and an attacker could execute code remotely. ZecOps has already been reported to Apple and will be fixed in the next iOS update.
You've Got (0-click) Mail!-ZecOps Blog
A critical iPhone and iPad bug that lurked for 8 years may be under active attack | Ars Technica
https://arstechnica.com/information-technology/2020/04/a-critical-iphone-and-ipad-bug-that-lurked-for-8-years-is-under-active-attack/
There are two vulnerabilities reported by ZecOps, the first is that the error check is not performed by writing to the out-of-area memory, and the second was a heap overflow . The two vulnerabilities are said to be due to the bug 'Improperly handling return value of system call'.
An attacker can exploit these two vulnerabilities by embedding junk data in the heap area of the iPhone's memory using an email that consumes a large amount of iPhone's memory (RAM). In particular, ZecOps calls it 'remote zero-click' because the attack using the second vulnerability can be executed without the victim having to open an email or follow a link.
If the attack is successful, the mail application will crash in iOS 12 and will not crash in iOS 13, but the operating speed of the terminal will temporarily decrease. Also, it seems that the attack will be completed before downloading all the contents of the attack mail from the server. After investigating the victim's iPhone, ZecOps reported that it did not find the attack email that it should have received, pointing out that the attacker may have already deleted the attack email.
If the attack fails, the message 'This message has no content.' Is displayed in the body of the attack mail as shown in the image below. According to ZecOps, this attack only works with iOS's default email app, not third-party email apps such as Gmail or Outlook, or macOS email apps.
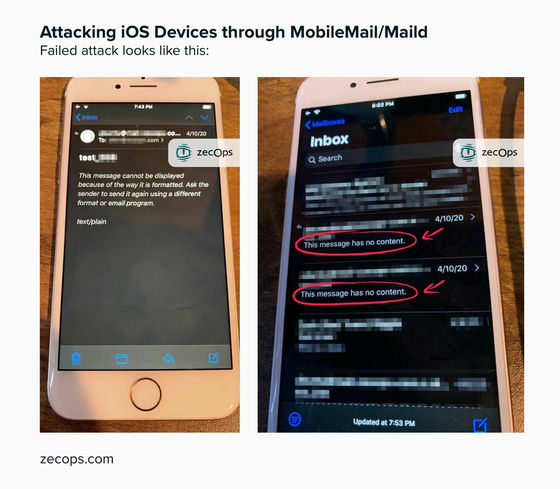
ZecOps added, 'The key factor that affects this attack potential is the use of hardware. IPhone 6 has 1GB, iPhone 7 has 2GB, iPhone X has 3GB, older devices have less physical RAM and virtual memory. The area is also small. ' According to ZecOps, the case suspected of attacking this zero-day vulnerability can be traced to January 2018, and at least six individuals and organizations were damaged. Some of the victims include 'executives of Japanese telecommunications companies.'
Since ZecOps succeeded in reproducing a series of attacks in the lab, it reported to Apple on March 31, 2020 that this attack was a exploit of an undiscovered zero-day vulnerability. It seems that iOS 13.4.5 beta has applied a patch for this issue.
Related Posts:
in Software, Smartphone, Security, Posted by log1i_yk